
-
- Home
>
-
- Blog
>
-
- SIEM Trends
Introducing Exabeam SIEM: A Hyperscale Cloud-native SIEM
- Oct 27, 2022
- Sanjay Chaudhary
- 4 minutes to read
Table of Contents
Introducing Exabeam SIEM
Cybersecurity today is a big data problem. Every sensor, detection product, or feed required to enable security use cases drives the collection of more data, often into terabytes per day. As the window of opportunity to detect and investigate attacks decreases, defenders are left vulnerable if they don’t know what to look for. As data volumes, exposure points, third-party alerts, and the cost of talent and storage have all multiplied, the speed of SIEM innovation has not kept up. Unfortunately, most SIEM products can’t meet the requirements of today and so industry analyst are asking customers to settle for less with XDR; customers deserve a better approach rather than jump to one more category.
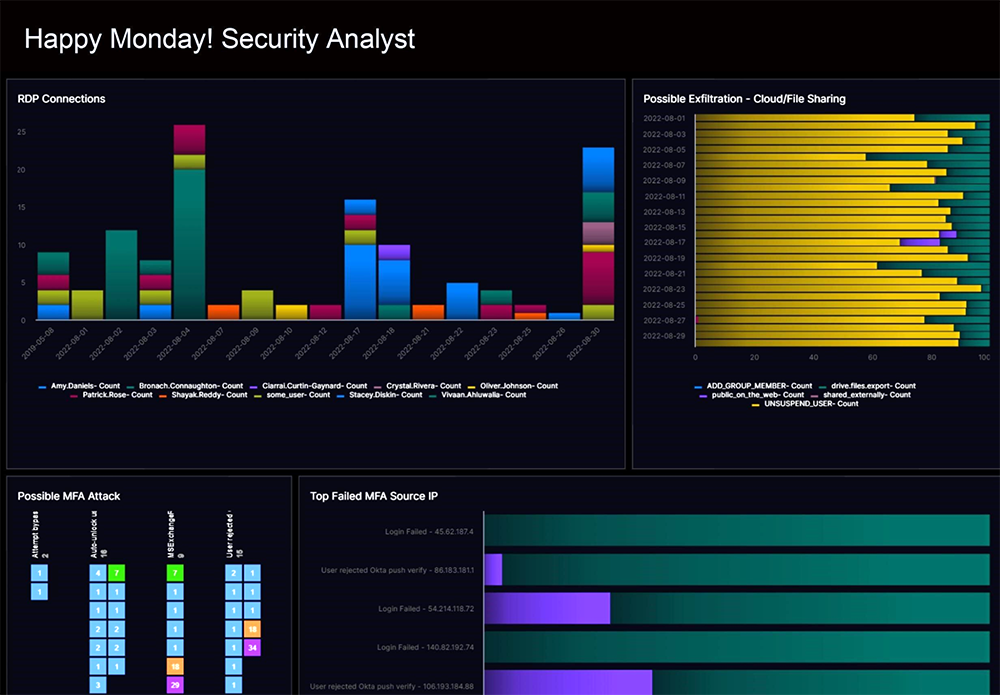
I am excited about the launch of Exabeam SIEM and the new Exabeam Security Operations Platform. Exabeam SIEM delivers limitless scale to ingest, parse, store, search, and report on petabytes (PB) of data — from everywhere. You can now bring data at 1 million+ EPS sustained across 500+ IT & security products, and leverage Exabeam SIEM to search and detect threats across PB of data. On top of Exabeam SIEM integrations, usability and performance is offered at a competitive pricing against any SIEM in the market. In a market notorious for expensive, difficult-to-use products, Exabeam SIEM changes all of that.
Visualize patterns and trends across petabytes of security data
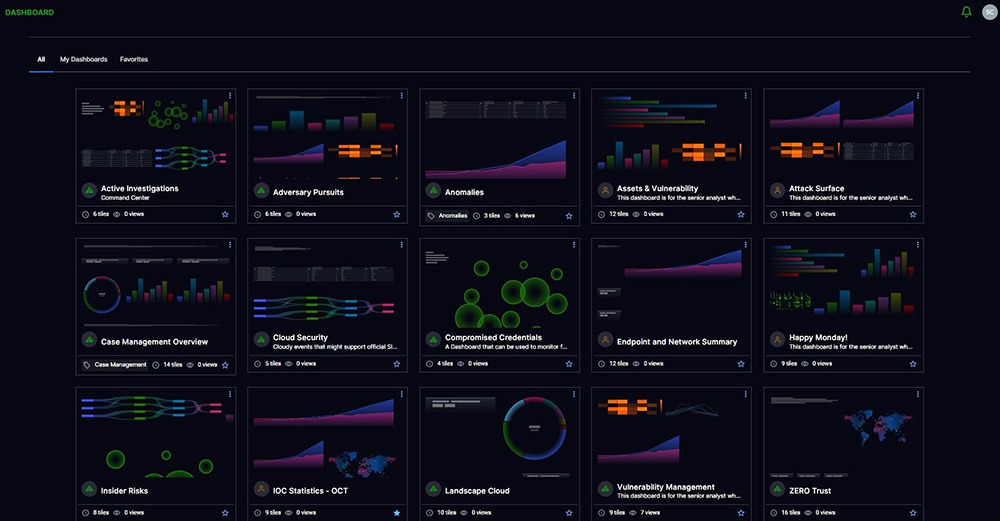
The Reports and Dashboards application allows you to build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool. The Exabeam Reports and Dashboards app is fully integrated within Exabeam SIEM, allowing you to create powerful visualizations from your parsed log data quickly. Customers can choose one or more visuals to meet their business needs. These include bar chart, column chart, line graph, area chart, pie chart, donut chart, bubble chart, funnel, single value, sankey map, word cloud, heat map, table, and a Coverage Map. Bring data from 100s of security tools and visualize patterns and trends across these tools.
Search and hunt threats across multi-year data

Search is a feature that provides a simplified experience with faster query and instant results over PB-scale and/or years of data. Search across real-time or historical data is no longer a barrier. SOC teams do not have to import and wait for historical data to be restored and processed. Search is a single interface that allows analysts to search for events, logs, or Indicators of Compromise (IoCs). Moreover, there’s no learning curve, meaning analysts aren’t required to learn a proprietary query language. Search delivers a query builder wizard experience to point and click from a list of intelligent fields to help build effective search queries quickly and easily.
Customize detections against your adversaries

The Correlation Builder feature lets you write, test, publish, and monitor custom correlation rules for your most critical business entities and assets, including leveraging a library of more than a hundred pre-built correlation rules. Correlation Builder provides analysts with an easy application to create custom correlation rules suited to their organization’s security and use case requirements. All Exabeam SIEM correlations can be enhanced with the most up-to-date IoCs using the Exabeam Threat Intelligence Service. Available on all Exabeam products at no additional cost, this service provides enrichments such as file, domain, IP, URL reputation, and TOR endpoint identification to prioritize or update existing correlations. Adding to this coverage is the Exabeam Security Research Team that automatically publishes new detections for you to test and use to stay up to date with emerging threats.
Raw logs to security insights at 1M+ EPS sustained
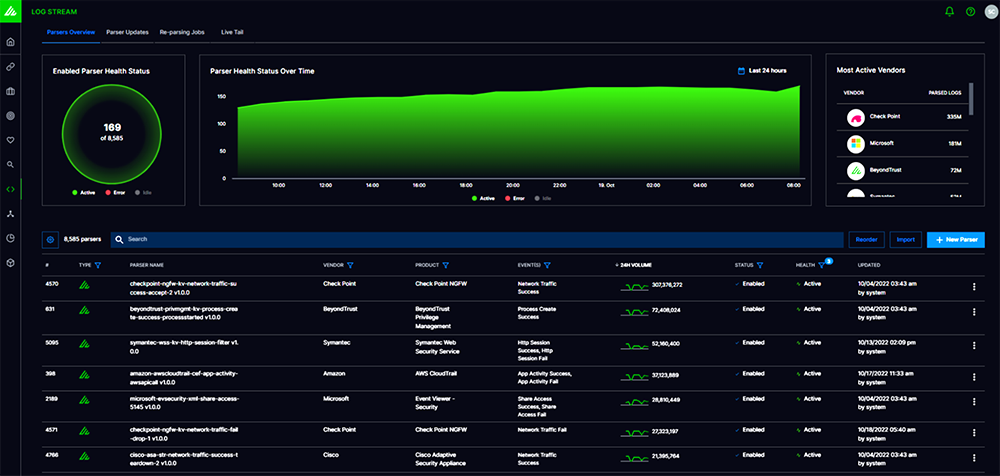
The Log Stream app provides rapid log ingestion and processing by converting raw logs into security events at a rapid 1M+ EPS sustained per tenant. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam products and features. As it is ingested, data is parsed using 7,937 pre-built log parsers, and enriched using open-source and commercial threat intelligence feeds and finally converted into multi-vendor normalized security events based on Exabeam Common Information model. Serverless processing and scale is at the heart of Log Stream.
Manage all security alerts and cases in one place
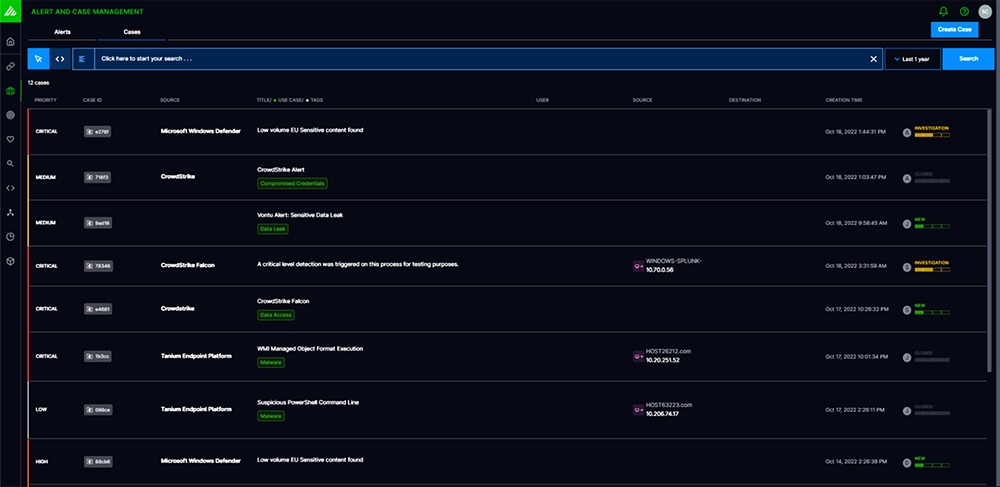
Alert and Case Management centralizes events and alerts sourced from Exabeam or third-party products, letting an analyst review alerts individually or at volume, or set conditions to automate the alert triage workflow and escalate events and alerts into incidents. Alert and Case Management helps analyst add tags and events to incidents, collaborate across groups and time zones, and offers customizable, outcome-driven steps for analysts to guide them through to mitigation or resolution.
Make progress on security outcomes which matter most for your business
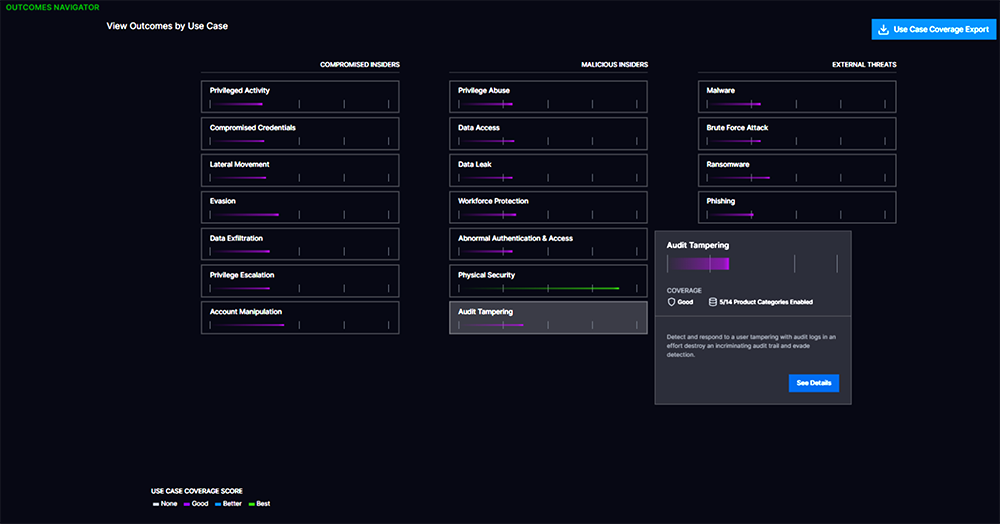
Outcomes Navigator maps the feeds that come into Exabeam SIEM against the most common security use cases and suggests ways to improve coverage. Outcomes Navigator supports measurable, continuous improvement focusing on outcomes by recommending information, event stream, and parsing configuration changes to close any gaps.
Avoid business risk with legacy SIEM — upgrade to Exabeam SIEM
Exabeam SIEM combines hyperscale search and powerful detection, reporting, dashboarding, and case management with a cloud-native security operations platform. If you are still using legacy SIEM or IT log management vendors’ SIEM, it’s time to upgrade for better security outcomes!
Learn more: Discover New-Scale SIEM.
No cybersecurity solution can prevent all attacks; however, some can detect intrusions and anomalous activity better than others. And while some SIEMs have better detection and analytics capabilities, many require specialized expertise or are too costly for ingesting, analyzing, and maintaining all the logs that might help your teams stitch together the story of what really happened in an attack. Combating these challenges requires a system equipped to find the true gems of discovery amidst the noise of alerts.
There are a lot of SIEM vendors in the marketplace. How do you know you’re selecting the right fit for your organization?
Download this guide to learn the three critical success factors when choosing a new SIEM.

- Tags
- new-scale siem
- SIEM
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.



