
-
- Home
>
-
- Blog
>
-
- InfoSec Trends
Ransomware: Prevent, Detect and Respond
- Oct 12, 2021
- Tim Lowe
- 5 minutes to read
Table of Contents
It was the most audacious attack in recent months. Kaseya released a public statement denying paying any ransom and reported that they had worked with a third party to decrypt all the data that was encrypted in their customers’ systems. Though a costly ransom was averted in this case, this attack demonstrates the magnitude of a serious ransomware attack. It surely was very costly to remediate and certainly represented a reputational hit to the company.
This attack, which came on the heels of the Colonial Pipeline attack in May, turned the eyes of security practitioners directly onto this serious threat. The Colonial Pipeline attack caused widespread supply chain disruption in the Southeastern U.S. and Eastern seaboard. The attackers issued a $4.4 million ransom demand and threatened to leak the 100 gigabytes of data it had exfiltrated if the demand wasn’t met. Numerous government agencies got involved in the investigation and it resulted in a call directly from the White House for U.S. companies to tighten up their cybersecurity posture. As a result ransomware best practices are now at the forefront of security practitioners’ security strategies.
Ransomware: What is it?
Ransomware is a form of malware designed to render data on an endpoint inaccessible to the user. In this post we’ll be focusing on encrypting ransomware, as it is the most destructive and most common type of ransomware in today’s environment. This type of ransomware encrypts specific file types or entire drives on a device and holds it hostage until a ransom is paid to recover it. This type of attack can be particularly destructive when a user has essential personal data or business critical data residing on it. In this post we’ll be covering how ransomware infects endpoint devices, how it moves laterally through a network, and what can be done to prevent it.
Ransomware: How does it happen?
As we say in the NotPetya and WannaCry attacks of 2017, ransomware is particularly insidious. Despite Microsoft’s Server Message Block v1 vulnerability being patched in 2017, these attacks are still happening today. It only takes one unpatched device, however, for the ransomware to worm its way through a network. Advanced ransomware exploits gain entry to a system by several different means. Once a machine is infected, the exploit often uses lsadump or Mimikatz-type tools to dump credentials and use them to spread laterally through the network.
Some of the common entry points to a network for ransomware are:
Phishing
- Malicious links: Bad actors often will use phishing or spearphishing emails with malicious links to deliver their payload. Spearphishing is a form of phishing that targets the content to the audience, creating realistic looking emails that are likely to be clicked based on the interests of targets.
- Infected attachments: Likewise, opening attachments in emails or from shares is an effective way to gain access to a network. An unwitting user clicks a link and becomes infected, thereby granting potential further access
Drive-by download attacks
- Infected websites: Often attackers will inject their ransomware into a website that automatically downloads ransomware onto a user’s machine. Adware and bundleware are also common culprits of drive-by download attacks.
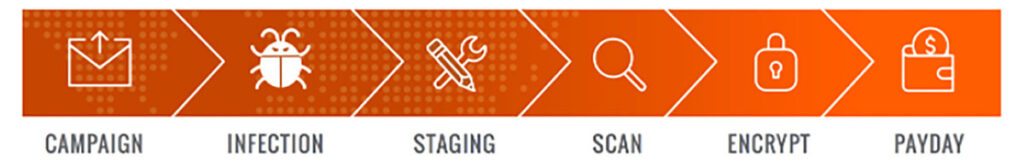
Most ransomware activities follow the six stages of what is known as the ransomware kill chain. The stages are:
- Distribution campaign – attackers use techniques like social engineering and weaponized websites to trick or force users to download a dropper which kicks off the infection
- Malicious code infection – the dropper downloads an executable which installs the ransomware itself
- Malicious payload staging – the ransomware sets up, embeds itself in a system, and establishes persistency to exist beyond a reboot
- Scanning – the ransomware searches for content to encrypt, both on the local computer and the network accessible resources
- Encryption – the discovered files are encrypted
- Payday – a ransom note is generated, shown to the victim, and the hacker waits to collect on the ransom
When an attacker gains a foothold in your network, likely the next move will be to begin attempting to enumerate the network and find places to exploit weak passwords or dump credentials to gain access to more accounts to compromise. It’s important to take a layered approach in the detection of ransomware on your network. Ransomware infecting a machine is not a death sentence to your enterprise. Prevention is clearly the best scenario, but early detection can prevent the lateral movement required to spread the ransomware throughout the network.
Ransomware: early detect or eventually get rekt
Every ransomware attack will vary in its deployment. There are humans releasing this malevolent digital Kraken into the wild so their motivations will drive the means of execution and its timetable. What this means in real terms is that if an attacker does find a way into your network, they will still have some tasks to do before they begin their dirty work. This means you may have some time to detect and isolate it before abject pwning pops off. The best and most efficient way to surface a breach involving compromised credentials, lateral movement, and privilege escalation is behavioral analytics.
While it would be nice if a hacker broke into the network to do your job for you, that is one event that might be one of the few new things under the sun. No attacker is ever going to behave the way a normal user does. They will inevitably be running new processes, touching new assets or files, or otherwise engage in CLI or PowerShell activity that the average user does not. An attacker won’t mimic your habitual activities, so having baselines established that show when an account or asset deviates from normal activity is a priceless resource to uncover unauthorized activity around ransomware on the network.
Ransomware math: prevention > reaction
If you have a breach early detection is key, but even Benjamin Franklin probably knew that an ounce of ransomware prevention was worth a pound of remediation. So how do you keep it off your network in the first place? Here are some best practices for prevention.
Some of the best ways to prevent ransomware from finding a home in your environment include:
Patch software and operating systems
- In the absence of a zero-day exploit, there is likely a patch to prevent attackers from deploying malware on your system. Patching can be a pain and can cause problems from time to time, but they pale in comparison to getting your network hammered by ransomware.
Uninstall legacy and unsupported applications
- Many ransomware attacks attempt to take advantage of old and vulnerable software to create an entry vector to your network. Managing applications on endpoints prevents this in most cases.
School up your crew on security hygiene
- Well-informed employees are often the best line of defense against the attack techniques used by the purveyors or ransomware. According to a 2020 Sophos study, 45% of ransomware attacks emanate from users not understanding how to identify and interact with spam email.
In the case that you do get hit with ransomware, make sure that you have a backup plan in place and are being followed closely.
Frequent backups
Backing up frequently prevents the need to pay the ransom in the first place. Storage is relatively cheap these days so follow established organizational backup procedures to keep good backups, and maybe backups of your backups.
So the bottom line with ransomware is that it is one of the most dangerous types of malware to have in your enterprise network, but with careful preparation and a clearly delineated plan of prevention, detection, and mitigation it is possible to contain and recover from it should it make its way into your network.
Further reading
To learn more about ransomware, check out the following articles that cover Exabeam use cases that address ransomware and the techniques used during attacks.
- Tags
- Phishing
- Ransomware

Tim Lowe
Senior Community Content Developer | Exabeam | Tim Lowe is the Senior Content Creator for the Exabeam Community, principally involved in multi-media product creation in support of Exabeam Use Case methodology. He was an Exabeam user as a Cybersecurity Engineer at a Fortune 500 company prior to coming to Exabeam. He served 14 years as a Cryptologic Technician and Intelligence Analyst for the US Navy and National Security Agency, where he was involved in technical development for a wide array of national security interests. His background, prior to migrating to the field of cybersecurity, is in linguistics. He did his Bachelor’s and Master’s degree in French Literature before studying Arabic at the Defense Language Institute in Monterey, California. He has worked in nine different countries in the security and cyber fields and lived in Europe for five years. He currently lives outside of Birmingham, Alabama with his wife and three daughters. He’s an avid mountain biker, musician, and obsessive audiophile.
More posts by Tim LoweLearn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.