In our first post, we looked at how to prepare for migrating a security information and event management (SIEM) platform. In this post, the second of the three-part series, we present the middle phase of executing the migration. The steps in this phase are where you bring your new SIEM to life by configuring its log sources, preparing SIEM content and defining operational processes. Taking a strategic approach to this phase is crucial because it establishes the operational capabilities of your SIEM – one of the most critical tools for securing a large enterprise.
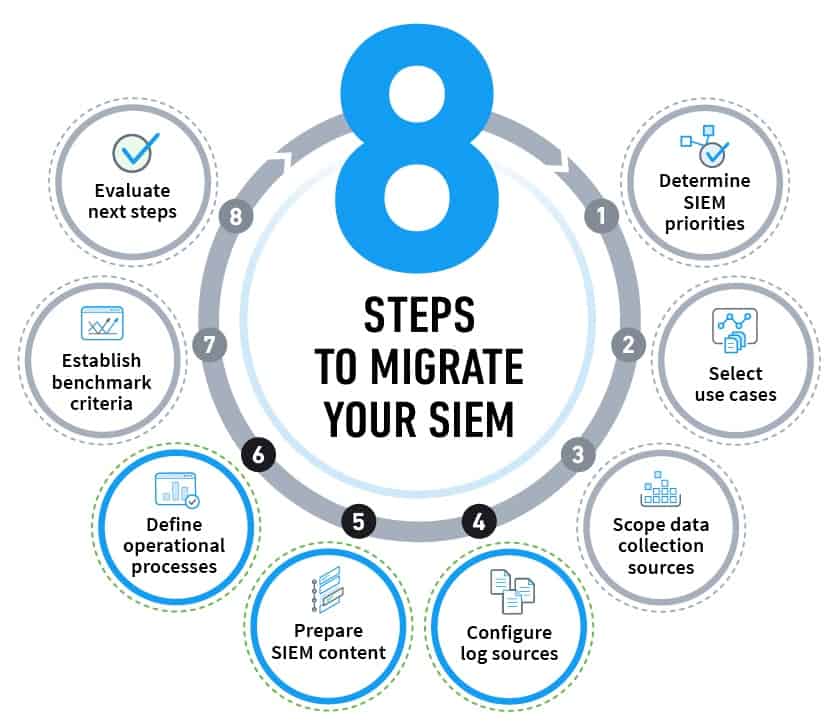
Steps for execution
-
Configure log sources
Configuring log sources is a non-trivial process. It entails far more than simply putting logs into configuration scripts. One option for success is to assemble a team with skills for configuration as this task may exceed the capabilities of existing analysts. Your new SIEM provider can provide assistance if needed.
Configuration usually entails three steps; the first is enabling ingestion of log files, which may require building out infrastructure to ensure that log files can get into the SIEM and that each field of data is properly identified.
Next, you may need to create specific parsers to parse each field used in the log file for SIEM detection. Log files and naming conventions are not always clear, so creating parsers may entail some detective work. Some SIEM providers require you to do this work yourself or will charge extra to do it for you.
Exabeam provides customers with more than 2,500 parsers for over 200 products to help them quickly make sense of logs. If a parser does not already exist for a particular data source, Exabeam customers can quickly get one at no extra charge, usually within days, by sending log samples to Exabeam. Customers can easily build their own parsers as well.
After clarifying parsers, move the legacy SIEM database of log files into the new SIEM. This will entail collaboration with storage, backup, IT operations, and compliance teams. Modern SIEMs are capable of ingesting and using vastly greater amounts of data, in the cloud if that is desired.
If your migration will entail temporarily running the legacy SIEM in parallel, the sources of log files will need to simultaneously feed data to the old and new systems in parallel or in sequence. Collaboration with respective log source owners and related IT infrastructure will be required to facilitate dual log feeds. Feed maintenance includes identifying systems that drop off, or new systems that are added but not feeding logs into the SIEM.
Timeline: Step 4 is one of the lengthiest in a SIEM migration; it can take 2-6 months. Delays in getting third parties to set up feeds are the main reason for requiring this much time.
-
Prepare SIEM content
Train SOC analysts in the approach of the new SIEM if you are moving from exclusive reliance on rules triggering alerts to models built using behavioral analytics based on machine learning. In most cases, behavioral analytics speeds detection, provides more accurate results and enables rapid, precise response to critical incidents.
Your SOC analysts will need help understanding what capabilities the new SIEM provides. Using Exabeam Security Management Platform (SMP) as an example, your new SIEM:
- identifies the most important events requiring investigation;
- provides a point-and-click dashboard to simplify and structure daily work; and
- provides reporting for audit and compliance.
As part of content preparation, the migration team will need to ensure the new SIEM’s dashboard, reports and alerting system meet requirements of use cases selected for migration. Modify reports if needed to match your new use case requirements.
Executives will be keen to ensure the new SIEM addresses requirements for compliance, which will vary by the company’s industry. Your organization’s risk manager can provide specific requirements.
Timeline: Step 5 typically takes 2-8 weeks. The extended time range is mainly due to the choice of use cases being implemented as some are more complex than others.
-
Define operational processes
Getting good results from the new SIEM will require SOC analysts to adjust their daily operating processes. Analysts will especially want to know if they have to learn a new query language. A modern SIEM often has a point-and-click interface which alleviates the need for command line controls.
A critical point of understanding is how your new SIEM’s alert-and-response system varies from the legacy SIEM. A new SIEM will exponentially reduce the number of false positives, “noisy” interruptions that could be ignored but demanded response actions.
Determine which SOC analysts are appropriate for new SIEM operations. A modern SIEM’s ease of use allows Tier 1 analysts to do many things a more technically knowledgeable and experienced Tier 2 analyst was required to do with a legacy SIEM. Ironically, inaccurate results produced by legacy SIEMs often mired even the senior Tier 1 analysts in a reactive mode. Migration to a modern SIEM can improve everyone’s productivity!
Speaking of productivity, another important realignment entails expectations of productivity for SOC analysts. A legacy SIEM query often requires hours to get search results, while a modern SIEM’s results may appear in just a few minutes. This capability, coupled with instant response playbooks and machine-built timelines can immediately boost overall productivity for SOC analysts and allow them to focus on higher-priority issues.
The migration team will need to review and tune operational processes and their playbooks defined for the initial phase of migration. A critical component for automating elements of instant response playbooks are the integrations with third-party vendors to orchestrate remediation actions. Example solution integrations include asset discovery, cloud applications, endpoint detection and response, email, firewall, identity and access management, mobile device management, sandboxes and threat intelligence. Exabeam SMP has incident response integrations with over 55 vendors.
Finally, the migration team should document new SIEM processes for SOC analysts, auditors and other stakeholders. Definitely not an implementer’s favorite task, but it’s one that will pay big dividends after the migration.
Timeline: Step 6 can take as little as 2 weeks to learn how to use a new SIEM. However, it can take much longer to change habits and processes that were formed using the legacy SIEM. Expect up to 4 months before new operational processes are fully defined and internalized.
Proceeding to the Last Phase: Assessment
Our final blog in this series will look at the assessment phase of SIEM migration. To learn more right away about migrating your SIEM, watch our webinar, “Eight Steps to Migrate Your SIEM.” Or download our white paper, Eight Steps to Migrate Your SIEM. These sources will provide you with more details to help guide the migration process.
Further reading
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













