
-
- Home
>
-
- Blog
>
-
- SIEM Trends
Exabeam Agent Behavior Analytics: First-of-Its-Kind Behavioral Detections for AI Agents
- Feb 10, 2026
- Kevin Binder
- 3 minutes to read
Table of Contents
AI agents are moving into real workflows faster than most teams expected. According to PwC’s 2025 AI Agent Survey, 79% of companies are already adopting AI agents, and 88% of executives expect to increase AI-related budgets in the next year. These agents are now handling research, summarization, customer engagement, and operational tasks at a scale humans can’t match.
As organizations adopt them, a new reality is emerging: AI agents introduce risk that resembles insider threat activity. They operate as “non-human insiders” with broad access to systems, applications, and sensitive data. They run sequences of actions—queries, tool calls, automations, and updates—in rapid succession. When these actions start to drift from expected behavior, it rarely shows up as a single malicious event. It shows up in the pattern.
Traditional SIEM rules weren’t built for this.
Which is exactly why Exabeam created Agent Behavior Analytics (ABA).
ABA extends our user and entity behavior analytics (UEBA) foundation to a new entity type: AI agents. As the first SIEM vendor to deliver behavioral analytics for agent activity, Exabeam provides the detection layer organizations need to safely adopt agentic workflows at scale.
And with our January 6 release, we introduced new behavioral detections designed specifically for AI agent activity.
Why a Session Data Model Changes What’s Possible
Here’s the core issue: AI agents behave like workflows, not events.
Most SIEM-only detections only look at:
- Single log events
- Correlation rules with short time windows
That approach works for many threats, but not for agentic activity. Agents break tasks into a chain of steps: prompt → tool call → data access → action → outputs→ repeat. Detecting misuse requires understanding the sequence of those steps, not just their individual parts.
A session data model solves this by:
- Connecting related activity into a single narrative
- Preserving the full history of what happened
- Automatically generating timelines that show cause and effect
In practice, the suspicious activity is usually the pattern, not the event.
The “First-Time” Advantage: Where Rules Fall Short
Behavioral analytics is strongest when the key question is:Has this entity ever done this before?
That question is essential when monitoring AI agents. Agents often perform legitimate actions, but a sudden shift—an unusual dataset, a new system, or an odd sequence—can signal risk long before anything becomes malicious.
ABA includes multiple “first-time” detections tied to AI guardrail events, such as:
- Abnormal number of guardrail violations
- Guardrail violation observed
- First guardrail violation for a user
- First guardrail violation for a user in an org
- First guardrail violation for a user in a department
These detections help teams see emerging anomalies immediately. A traditional SIEM can alert on “guardrail violation observed,” but representing “first time for this user in this context” with rule logic alone becomes complex, brittle, and noisy.
Why a SIEM Alone Isn’t Enough for Agent Monitoring
Your SIEM is excellent at collecting logs, searching data, and executing rules. But agent monitoring demands deeper context:
- Novel behaviors: AI agents introduce new error paths and misuse patterns. You can’t write rules for issues that haven’t happened yet.
- Sequence-driven activity: Agents chain actions. Without history, alerts arrive as isolated fragments.
- Behavioral prioritization: Behavioral analytics weights actions by relevance. Instead of treating every event the same, you see what’s unusual for that specific agent, user, department, or organization.
This reduces noise and accelerates investigation.
Tracking Maturity With Outcomes Navigator
To help teams adopt ABA effectively, Outcomes Navigator now includes the new Agentic AI Security use case. It provides a structured way to:
- Track progress across users, departments, and workflows
- Measure improvements as detections and guardrails expand
- Identify where coverage is strong and where gaps remain
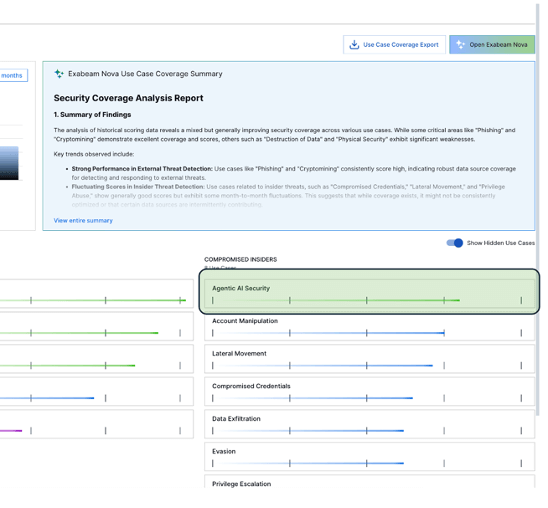
ABA: The Foundation of the Agent-Focused Detection Layer
ABA is the beginning of a broader strategy: applying the proven behavioral modeling and session-based analytics of Exabeam to autonomous agents. Rule-only approaches are expensive to maintain and struggle with the pace and variety of agentic activity.
AI agents aren’t just another log source. They’re autonomous actors operating inside your environment. Securing them requires a detection layer built on behavior, history, and sequence.
That’s what Agent Behavior Analytics delivers: the missing layer organizations need to operate AI agents safely.
See how ABA fits into the New-Scale Security Operations Platform. Explore New-Scale Analytics and dive deeper with our white paper, Enabling the High-Fidelity SOC With Behavioral Detection.

Kevin Binder
Senior Product Marketing Manager | Exabeam | Kevin Binder is a cybersecurity marketing professional based in Morgan Hill, CA. Kevin has over 20 years of experience in information security marketing with companies including Amazon Web Services, Citrix Systems, and Nortel Networks. In his previous roles, Kevin was responsible for go-to-market strategy for emerging technologies such as cloud-based security services, mobile device management, and user-behavior analytics. He received a B.S. degree in Managerial Economics from UC Davis. In his free time, Kevin enjoys spending time with family and friends, sporting events, and golf.
More posts by Kevin BinderLearn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Exabeam Agent Behavior Analytics: First-of-Its-Kind Behavioral Detections for AI Agents
- Show More

