
-
- Home
>
-
- Blog
>
-
- InfoSec Trends
Shields Up: What You Can Do Following New Reports of Destructive Malware in Ukraine, Latvia, and Lithuania
- Feb 26, 2022
- Exabeam Research
- 3 minutes to read
Table of Contents
The situation in Ukraine unfortunately continues to escalate, and our hearts are with those who’ve been displaced and/or affected by the conflict. We want our customers to know we are here for you, and we will continue to update and inform you on all cybersecurity reports that impact your ability to protect your businesses and people.
What we know
Newly reported destructive malware has been identified impacting computer systems in Ukraine, Latvia, and Lithuania targeting financial institutions and government contractors. The new data wiper malware is believed to be linked to Russia and in support of the on-going invasion happening in Ukraine. We are also hearing reports of network attacks — Distributed Denial of Services (DDoS) — against Ukrainian government agencies and state-owned banks, including ATMs.
For now, it appears that these cyberattacks are highly targeted and focused on Ukraine and members of the Ukrainian government and contractors. There have not been reports of similar cyberattacks waged against neighboring countries or any NATO allies at this time.
Exabeam will continue to monitor the situation in real time, and provide information and guidance to our customers on how to strengthen their defenses and identify known threats and attacks related to the ongoing conflict.
Recommended Actions
| IOC | Threat |
|---|---|
| 912342F1C840A42F6B74132F8A7C4FFE7D40FB77 61B25D11392172E587D8DA3045812A66C3385451 MD5: 3f4a16b29f2f0532b7ce3e7656799125SHA: 1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591 | Win32/KillDisk.NCV trojan 6/n |
Exabeam recommends having on monitor (watchlist) your high privilege accounts and service accounts since these types of attacks rely on users to look to move laterally or escalate privilege. This makes it imperative to understand abnormal behavior on your user accounts.
In previous attacks from similar attacker groups (exa Sandworm Team and APT29) they rely heavily on privileged accounts to damage disk partitions or impact the functionality of the operating system.
https://attack.mitre.org/groups/G0016/
https://attack.mitre.org/groups/G0034/
Based on current information, the following activities could prove useful on detection of these types of malware threats:
- Have a watchlist with an updated list of:
- Privileged users
- Service accounts
- Have a constant threat hunt operation for the following types of behaviors, adding as scope user label privilege accounts and service accounts.
- Query registry
- System information discovery
- Lateral movement
- Privilege escalation
Exabeam will continue to monitor this threat and provide more guidance as data becomes available.
The best indicator to detect this ever-evolving type of threat is knowing and understanding user behavior, since mostly every threat actor requires an account to propagate inside your network.
For customers using Exabeam Fusion SIEM and Fusion XDR products, please see our instructions below to create watchlists and more easily add rule tags to threat hunter searches.
How to add/modify context tables
How to create custom Context Tables
- On the Advanced Analytics Admin page, click on “Context Tables”
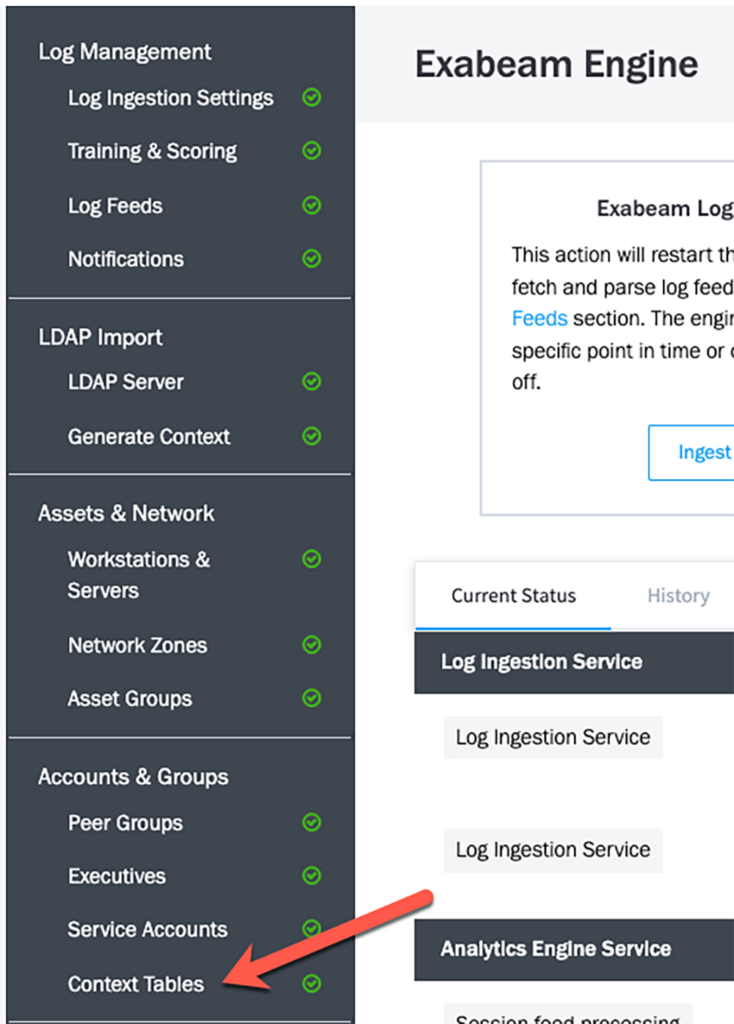
- Search for “priviliged_users”
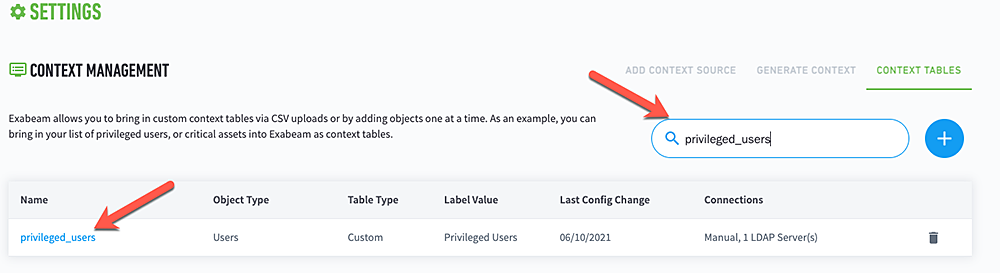
- There are two options to add accounts to the context table.
- You can upload a CSV of all your privileged users
- You can add in a single privileged user
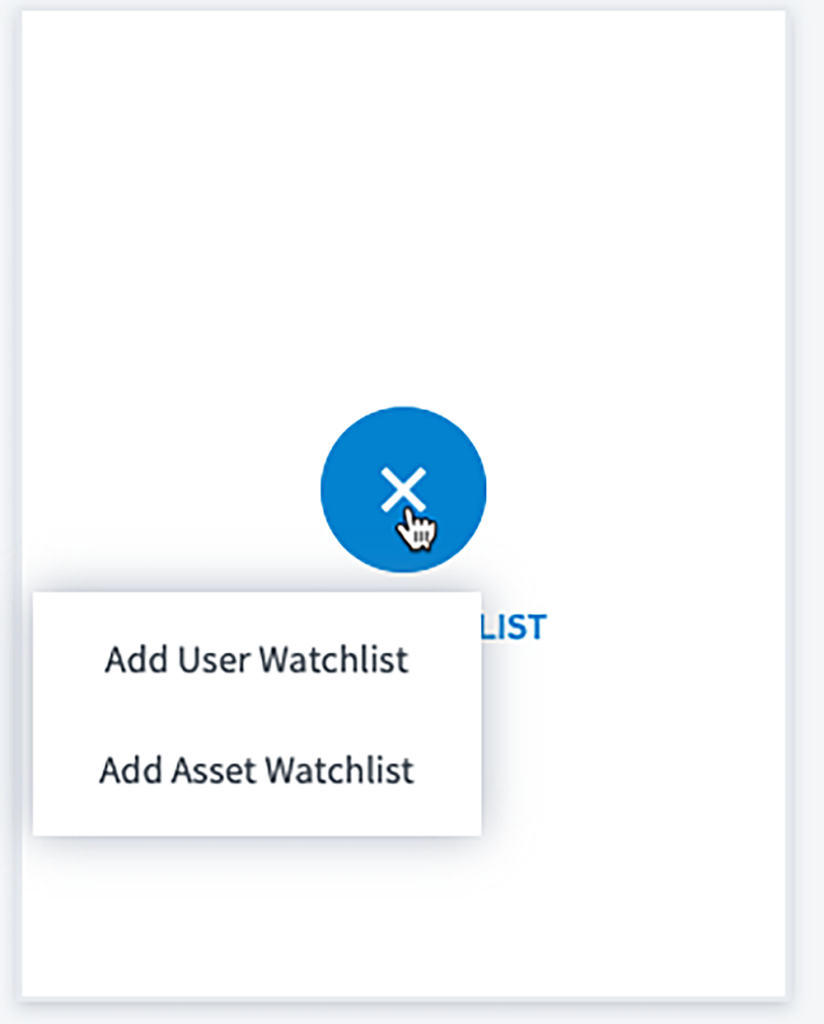
- On the Advanced Analytics homepage, click on the new watchlist and select “Add User Watchlist”
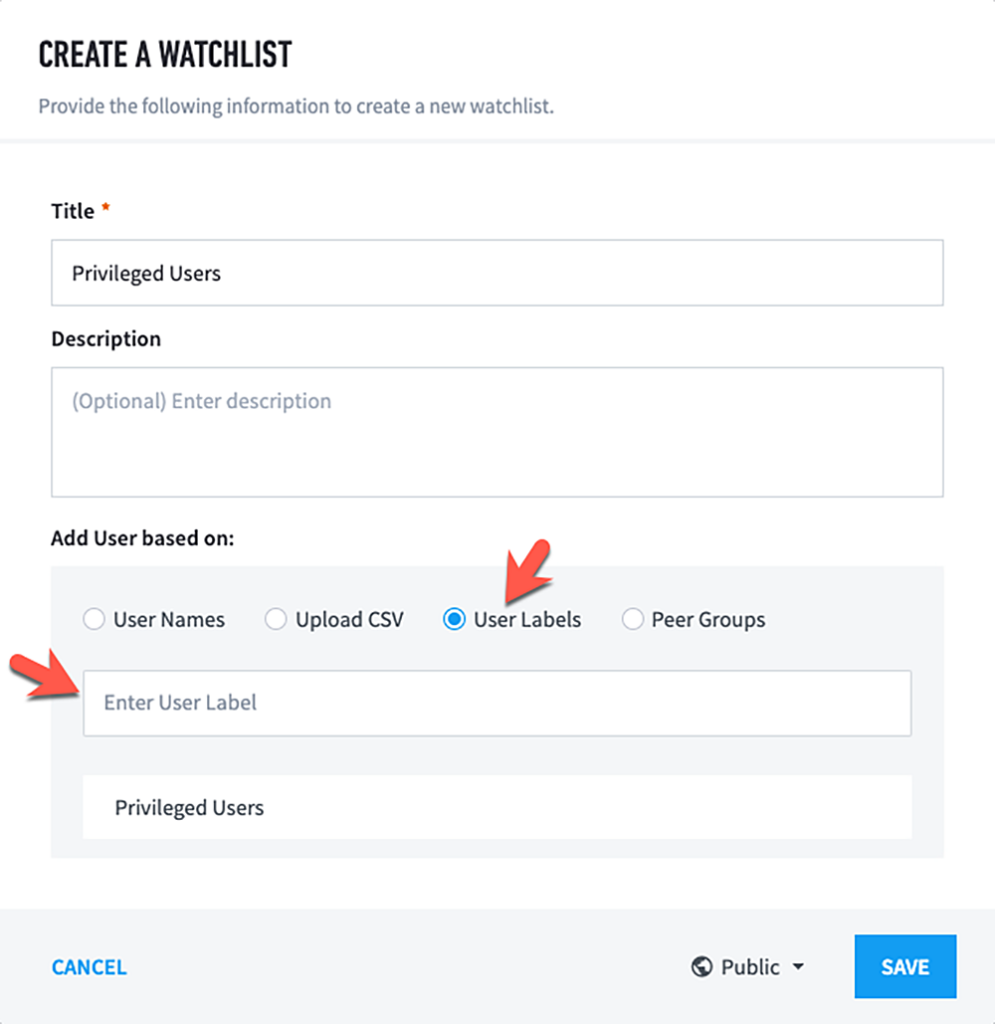
- Set the following attributes
- Title
- User Labels
- Privileged Users
- Then “save”
How to add Rule Tags to a Threat Hunter Search
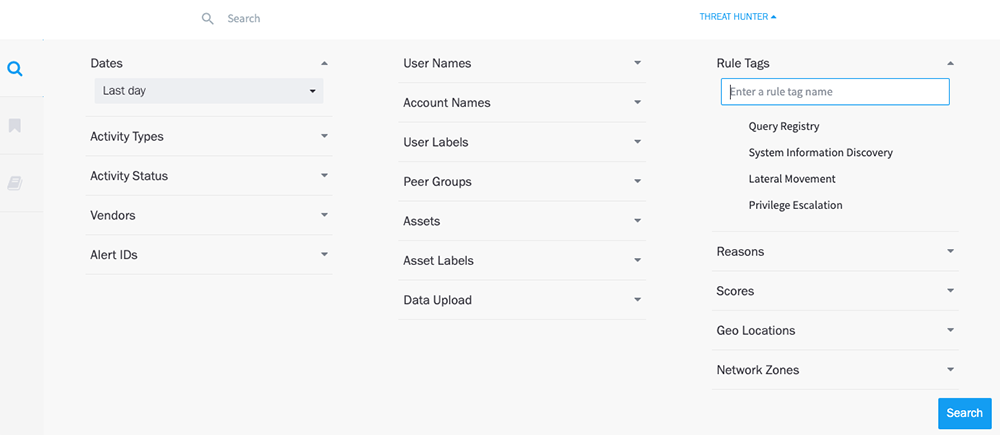
How to perform Threat Hunter searches
- Go to Threat Hunter
- Add the following to “Rule Tags”
- Query Registry
- System Information Discovery
- Lateral Movement
- Privilege Escalation
How to add a correlation rule
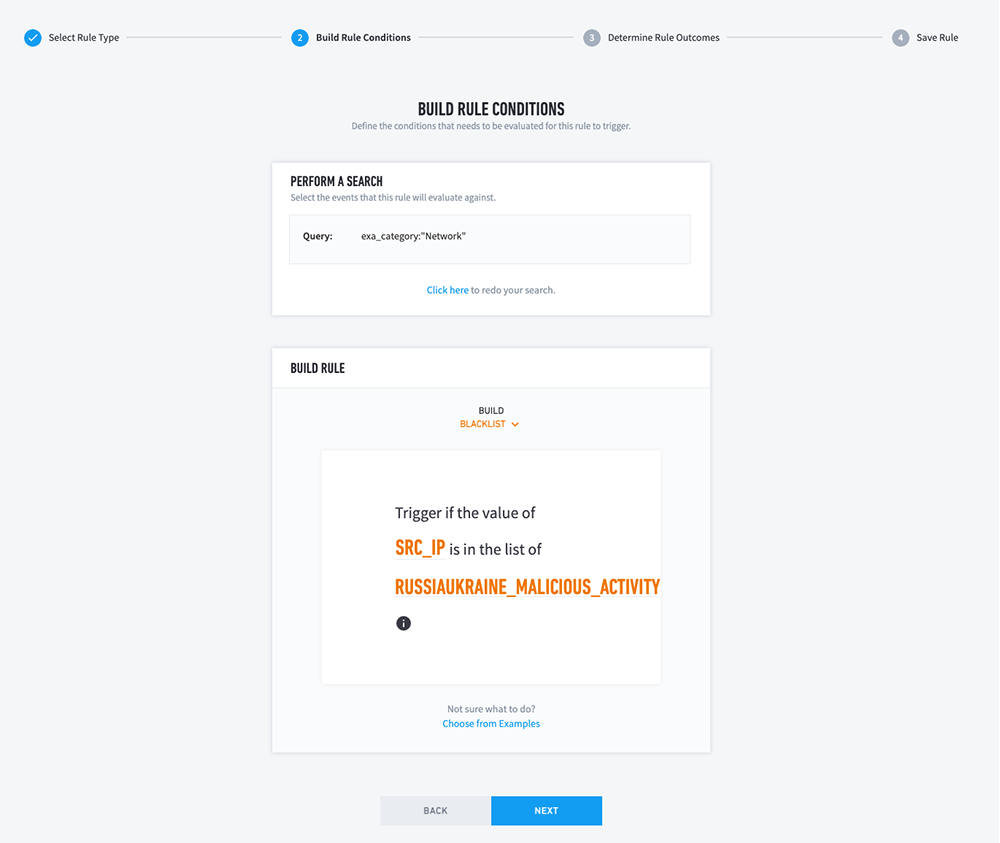
Create a Correlation Rule with the following attributes
- Rule Type: Blacklist
- Search Query – exa_category:”Network”
- Trigger if the value of “SRC_IP” is in the list of “RUSSIAUKRAINE_MALICIOUS_ACTIVITY”
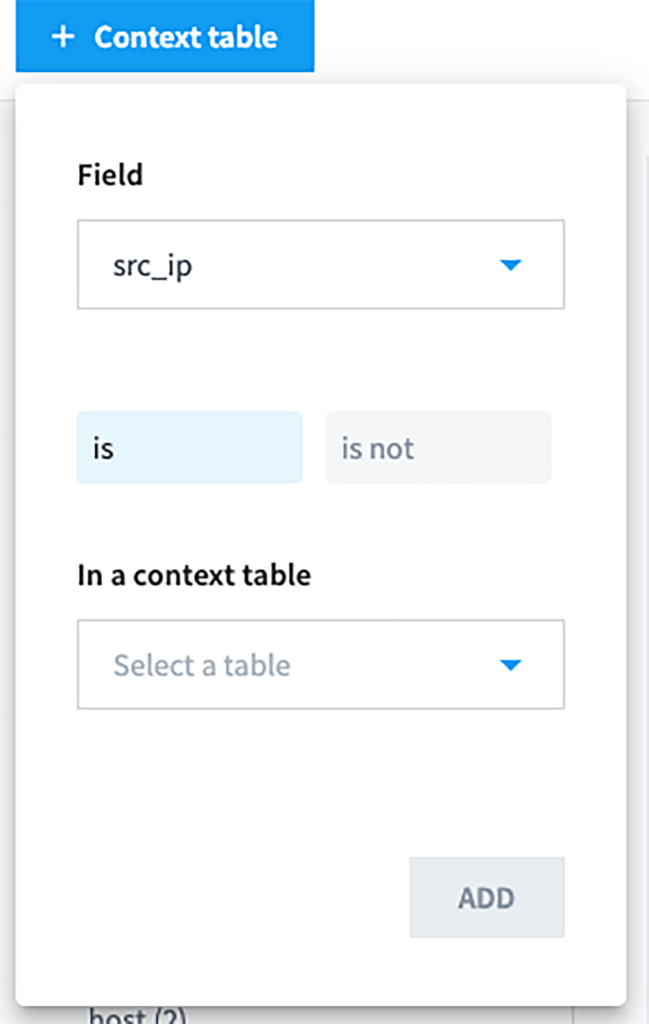
How to perform historical searches using context tables
- Create a search query using “exa_cateagory:”Network”

- Click on the “Context Table” button.
- Select
- Field: “src_ip”
- In Context Table: Name of context table created earlier
To get a complete list of all IP addresses related to this attack to date, go here. Thank you to Greynoise.io for sharing this information with the public.
If you have any questions, please open a support ticket or reach out to your Customer Success Manager.
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.



