Part one of a two-part series
Imagine running the operations of a luxury hotel and your guests are suddenly locked out of their rooms until you pay hackers a bitcoin ransom. Or consider what would happen if the heating system for major public buildings is shut down during the middle of winter—such as in Finland, where temperatures can drop as low as −30°C to −50°C.
And what happens if a major metropolitan police department loses all of their dashcam video archives after following FBI advice to refuse paying hackers a ransom? Or a US healthcare network ends up paying $55K in bitcoin to criminals so as to regain access to its critical computer systems?
None of these scenarios are a bad dream; rather, they’re actual recent ransomware attacks. Now ranked as one of the top cyber threats, for several years ransomware has been wreaking havoc on organizations around the world. Verizon’s 2018 Data Breach Investigations Report cites ransomware as the cause of 39 percent of malware-related data breaches. That’s more than double the previous year, which was double that of the year before.
Not just a nuisance anymore—Beyond the scammers and tricksters
When ransomware first emerged, enterprise security teams rarely saw it as a major security threat. Typical victims were home computer owners who were unaware of the importance of avoiding suspicious websites or exercising caution with mysterious email attachments.
That early ransomware—which evolved considerably through the late nineties to 2010—mainly consisted of pranks and vandalism, where the primary goal for hackers was obtaining notoriety.
Typically, a ransom demand would display a message on screen offering spyware removal. There were ads for phony computer performance-enhancing apps that originated from driveby download websites. And threatening messages might appear after downloading malicious attachments in response to crudely written phishing emails. Usually these early ransom demands sought a fee to fix fake problems they claimed had infected the user’s computer—when in reality the computer was operating fine.
In 2008, we started to see the first computer-locking Trojans. One was Trojan.Randsom.C, which demanded users call a premium phone number (with a charge appearing on their phone bills) to regain access to their machine.
The rise of crypto-ransomware
Hackers took it to the next level with crypto-ransomware in 2013. The most notorious, Cryptolocker Trojan, sent a shocking message to victims that their files had been encrypted and would be deleted if a ransom wasn’t paid within three days. It was almost impossible to defend against; Cryptolocker’s programmers had found a way to generate strong 2048-bit RSA public and private key encryptions to infect files. Even though IT staff could remove the Trojan, affected files remained inaccessible in a way that was difficult to decrypt.
Today ransomware is no longer just a home computer nuisance where penny ante ransoms are demanded. Instead, hackers are executing calculated, dangerous, and costly attacks on enterprises and governments that can threaten public safety. And ransomware’s sophisticated delivery is designed to fool even the most savvy users.
High-value targets, bigger paydays
A 2018 F-Secure report, The Changing State of Ransomware explains how the rate of simple ransomware is slowing down, but that other, evolving attacks have become far more sophisticated. Today analysts are seeing an increase of hardcore extortionists using ransomware to target prime organizations with high-value targets.
Targeting enterprises is more lucrative than infecting individual users. While a user’s personal device may only cost a few hundred dollars to decrypt, attackers can extort tens of thousands of dollars or more from a high-value target.
One 2017 worldwide cyberattack showed everyone how vulnerable companies are to ransomware attacks. WannaCry attacked computers running a Microsoft Windows operating system by encrypting data and demanding bitcoin ransom payments.
Being incredibly pervasive, WannaCry’s infection via SMB ports ensured that it was focused on organizations, cites the F-Secure report. And ransomware spreading via exposed, compromised remote desktop protocol (RDP) ports is no longer uncommon.
As for RDP, the weaknesses that made it a popular pathway for hackers include:
- Leaving port 3389/TCP open to any inbound connection
- Not requiring administrators to change their default admin account credentials
- Permitting numerous login attempts before triggering an alert or account lockout
These enterprise threat vectors essentially allow criminals to focus on the quality, rather than quantity, of targets—for a potentially bigger pay out.
An annual 2017 ransomware report by Druva cites that more than half of enterprises report having been hit multiple times by ransomware, and attacks have moved beyond user endpoints, with 33 percent hitting corporate servers.
Exabeam’s own research, The Anatomy of a Ransomware Attack, found a rise in ransom prices as another trend, and that ransomware hackers are creating ever more complex tools.
How can ransomware be detected and stopped?
A user has unwittingly clicked on an attachment or link that draws them into a phishing site. Ransomware has penetrated your network. Now what? The good news is it’s still possible to detect it early enough in its kill chain to stop it cold and prevent hackers from getting their payday.
Detonating 86 strains in our lab, Exabeam researchers identified six stages common in ransomware’s kill chain. Each stage is consistent to any specific strain in the face of ongoing permutations or improvements subsequently made by hackers.
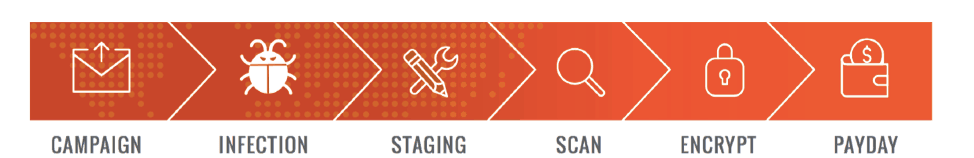
Figure 1 – The ransomware attack chain, from the email campaign to payday
1. Distribution campaign
During the distribution campaign, hackers use techniques such as social engineering and weaponized websites to trick or force users to download a dropper. This kicks off the ransomware infection.
2. Malicious code infection
Once aboard an infected machine, the dropper phones home (connects to a predefined list of IP addresses) to download a malicious .EXE (or a camouflaged executable) and stores it in a local TEMP folder. The dropper script then is terminated, removed, and the malicious payload is detonated.
3. Malicious payload staging
Here the ransomware sets up and embeds itself, while also establishing persistency to endure after a system reboot.
4. Scanning
Now the ransomware searches for content to encrypt, both on the local computer and on network-accessible resources. Affording security teams precious time to respond, this phase can be detected; it presents them with their opportunity to interrupt the ransomware kill chain.
Scanning the local machine and synched cloud folders can be accomplished in seconds. But mapping out a large corporate network, investigating the scan results, checking for read/write permissions, and other actions can take minutes to hours—depending on the amount of information that must be assessed.
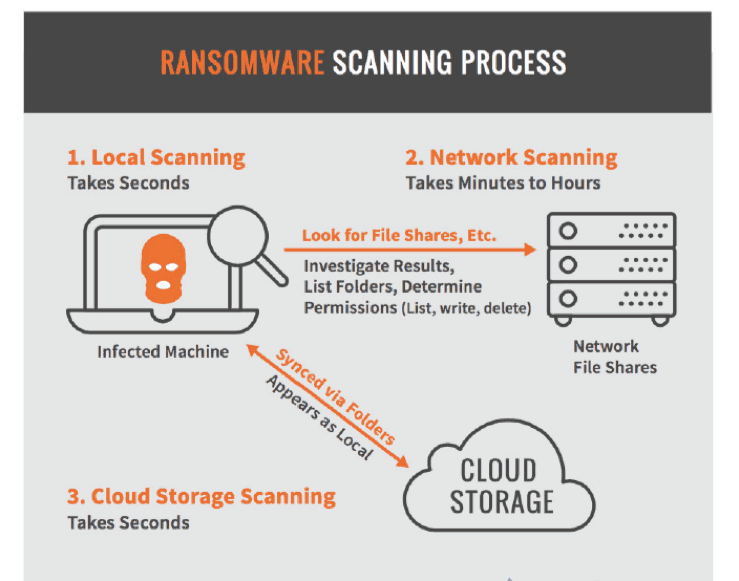
Figure 2 – The ransomware scanning process
4. Encryption
The ransomware has unpacked itself and performed reconnaissance on the system. Again there is still time to stop the attack—nothing that’s potentially irreversible has happened yet.
But control begins to favor the hacker during this phase, where the ransomware starts encrypting all the files it discovered during its scan. This phase can take anywhere from seconds to hours, as the encryption process runs locally on the infected machine. The ransomware must fetch a file, encrypt it, upload the encrypted version to the original location, then delete the original file.
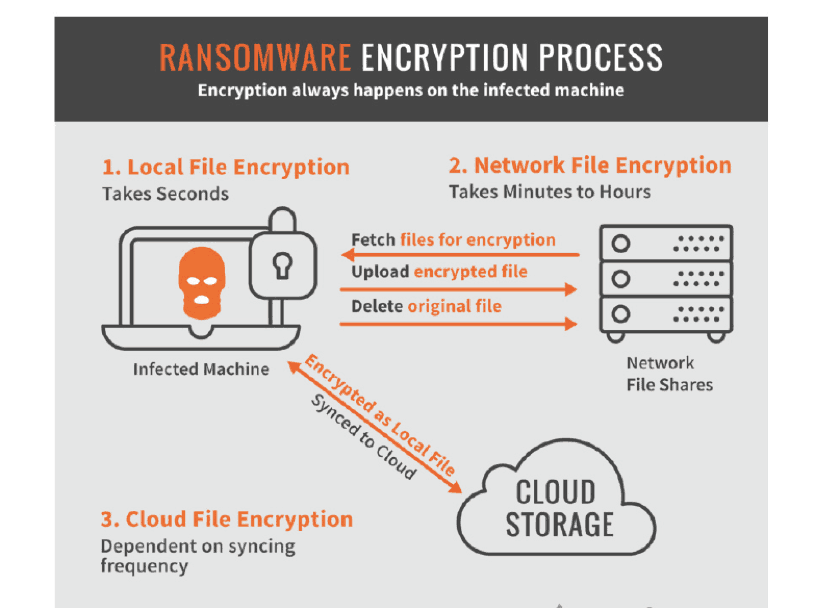
Figure 3 – The ransomware encryption process
Such attacks can be even more sinister. Should network or cloud storage locations discovered during scanning phase become unavailable, the ransomware can lay dormant. Relying on persistency precautions it takes during staging, it patiently waits for your resources to reenter its path.
Now the infection displays a ransom note and the hackers wait for payment to be deposited to their bitcoin wallet. You’re left to decide whether to pay the ransom or lose your encrypted files. In addition, their price can go up—many ransomware types are preconfigured with timeout thresholds; once each is reached the ransom amount increases.
Detecting ransomware before it does damage
As with malware, ransomware has no silver bullet. Attackers will continue to evolve their distribution methods and find increasingly inventive ways to infect their victims.
Fortunately, response teams have an opportunity to disrupt the process during the scanning phase, when the ransomware provides telltale signs that it has penetrated your network. Exabeam can detect anomalous machine and user behaviors—the damage precursors—in real-time. The next post in this series will detail how the Exabeam defense works and how your organization can successfully defend against ransomware.
For more detailed information on ransomware, see Exabeam’s research report, The Anatomy of a Ransomware Attack
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!