Exabeam’s Cybersecurity History Review

As security practitioners and history buffs, we’re intrigued by the history of cybersecurity. So much so, we built a calendar around it this year. Each month of the History of Cybersecurity 2019 Calendar features a significant date in cybersecurity history, along with a related trivia question and other notable dates in that month.
This is the first of several blog posts we’ll publish throughout the year featuring the historical cybersecurity dates we researched—we hope you find them as interesting as we do. And if you think we missed an important date (or got something wrong – we hope not!), let us know. Share your feedback with us on Twitter.
Back in 2010, disclosures of security breaches were infrequent and unusual. But on January 12 of that year Google shocked the security community when it announced a major breach on its infrastructure had occurred in China.
Google shared its investigation details in a blog post titled A New Approach to China. It revealed that cyberattacks, originating in China, didn’t just target Google’s infrastructure, but the attacks included at least twenty other companies in the internet, finance, technology, media, and chemical sectors.
The advanced persistent threat (APT) series had begun in mid-2009, continued through the end of that year, and were conducted by the Beijing-based Elderwood Group known to have ties to the Chinese People’s Liberation Army (PLA).
Attack known as Operation Aurora
Initially, Google said that “a primary goal of the attackers was accessing the Gmail accounts of Chinese human rights activists.” However, the breach appears to have been aimed at identifying Chinese intelligence operatives in the US who may have been under surveillance by American law enforcement agencies. It’s said the Aurora hackers gained access to certain Google accounts that had US court-ordered wiretaps.
Operation Aurora reportedly also targeted at least 34 companies in an attempt to steal trade secrets, including Adobe, Juniper, Rackspace, Symantec, Northrop Grumman, Morgan Stanley, and Yahoo.
How Aurora got its name
McAfee researchers assess that when the malware source code was made into an executable file, the compiler injected its source code folder name, Aurora, from the attackers’ machine(s)—hence the name given the attack.
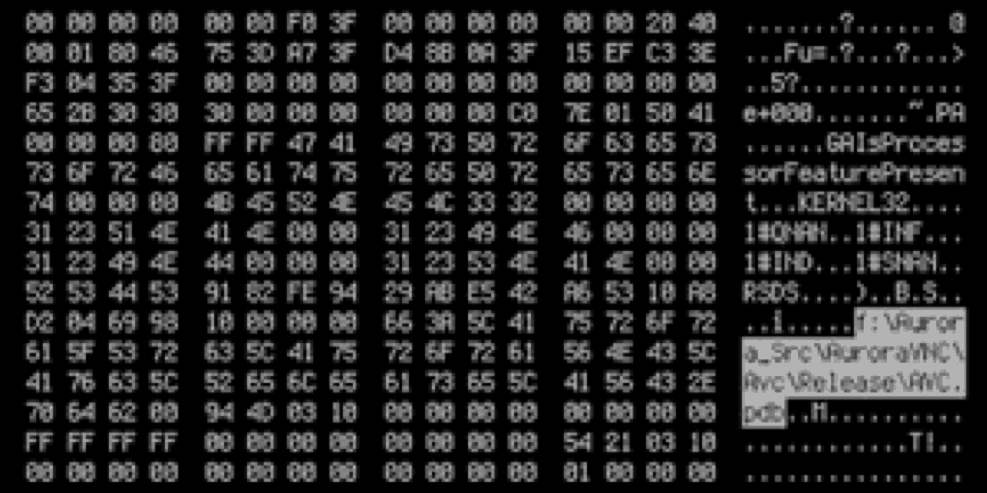
Figure 1- A screen shot showing the source code folder named Aurora.
How Operation Aurora worked
Once a victim’s system had been compromised, a backdoor masqueraded as an SSL connection, linking itself to command and control servers. A targeted system then began probing its protected corporate intranet for other vulnerable systems and intellectual property sources—specifically targeting the contents of source code repositories.
Google and China now
Today, Google’s inroads into the Chinese market is considered by many to be a short-lived experiment. Launched in 2006, the company’s Chinese search engine was pulled from the mainland in 2010 over the Aurora hack along with controversy over censored search results.
In August 2018, The Intercept reported that Google was working on a secret prototype of a new, censored Chinese search engine called Project Dragonfly. After the furor from human rights activists, some Google employees, and US Vice President Mike Pence (who called on Google to end Dragonfly), The Intercept reported that Google has suspended its development efforts in China.
A few other interesting dates in January Cybersecurity History
In addition to Operation Aurora, read about these other notable dates in cybersecurity history that happened in January.
January 15, 1977 – Data Encryption Standard (DES) published as federal standard (FIPS PUB 46)
The Data Encryption Standard (DES) was developed in the early 1970s. It’s based on an earlier design by Horst Feistel, a German-born cryptographer who worked on the design of ciphers while at IBM. The algorithm was submitted to the National Bureau of Standards (NBS), now the National Institute of Standards and Technology (NIST). It followed the agency’s invitation to propose a candidate for the protection of sensitive, unclassified electronic government data.
After consultation with the National Security Agency (NSA), in 1976 the NBS eventually selected a slightly modified version (strengthened against differential cryptanalysis, but weakened against brute-force attacks). This was published as an official US Federal Information Processing Standard (FIPS).
On a case-by-case basis for the protection of classified information, it was then mandated that DES be used in unclassified US government applications for the protection of binary-coded data during transmission and storage in computer systems and networks.
Use of the DES algorithm was made mandatory for all financial transactions of the US government involving electronic fund transfer, including those conducted by member banks of the Federal Reserve System. Subsequent DES adoption by worldwide standards organizations caused it to become a de facto international standard.
DES is a block cipher. This means a cryptographic key and algorithm are simultaneously applied to a block of data, rather than one bit at a time. To encrypt a plaintext message, DES groups it into 64-bit blocks.
Figure 2 – An example of a Data Encryption Standard (DES)
January 19, 1986 – Brain boot sector virus is released
Brain boot virus is considered to be the first IBM PC-compatible virus. It was written by brothers Basit Farooq Alvi and Amjad Farooq Alvi, from Lahore, Pakistan. Brain infected the boot sector of storage media formatted with the DOS file allocation table (FAT) file system—both hard drives and floppy disks alike. It would then sit in the computer’s RAM and infect any floppy disk that had been inserted into an infected machine.
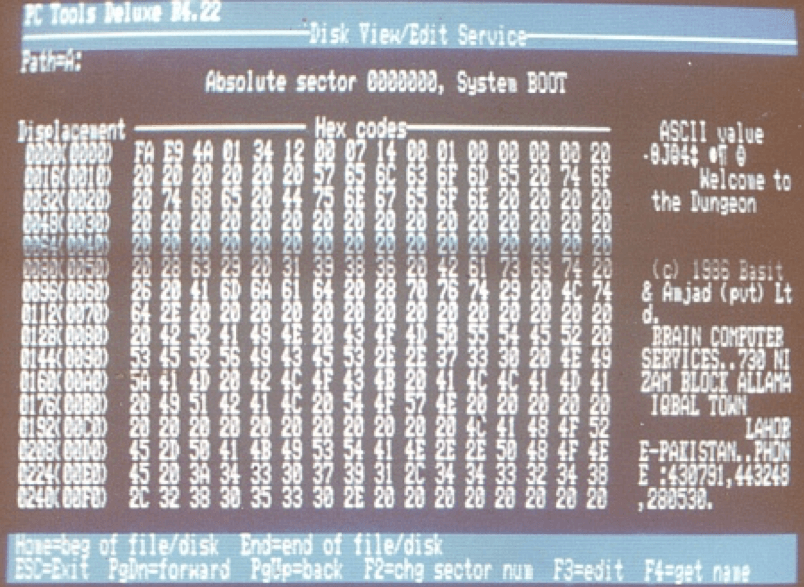
Figure 2 –Brain boot virus
January 30, 1998 – Verisign IPO
Verisign (VRSN) sold 4.56 million shares on NASDAQ at $14 each in a deal underwritten by Morgan Stanley Dean Witter, Hambrecht & Quist, and Wessels, Arnold & Henderson. Share price closed at $25.50, up over 82% for the first day of trading.
Click here for more information and trivia from the Exabeam History of Cybersecurity 2019 Calendar.
Consider yourself a cybersecurity history buff? Share your feedback with us on Twitter!
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











