The U.S. Constitution mandates a decennial census of everyone living within the country. Results determine congressional districts, apportion congressional seats for each state, and guide transfer of nearly a trillion dollars to programs’ recipients including an army of federal, state and local employees and contractors who administer and dispense the money and services. The census also produces an accurate national database of personally identifiable data. Needless to say, the nation must prevent malicious actors from derailing the census with inaccurate numbers or stealing personal data. Results of a 2020 Census cloud security audit, however, validate reasons for concern – and carry lessons that may apply to other organizations that are moving vital operations into the cloud.
Last June, the U.S. Dept. of Commerce Office of Inspector General (OIG) published findings of its audit of cloud security for the 2020 Census. The audit discovered three serious issues and provided eight recommendations – all of which were acknowledged and accepted by the Census Bureau.
Figure 1: A Census form in 1890. Things have gotten more complex since then.
Oversights caused massive exposure
You may have read about the OIG audit, notably how the Census Bureau failed to secure GovCloud root user keys for eight cloud environments hosted by Amazon Web Services (AWS). Keys were lost for seven 2020 Census cloud environments, making them vulnerable to attacks from any location in the world. A combination of unawareness and miscommunication by the Bureau’s cloud administrators, contractor cloud administrators, the commercial cloud reseller and AWS caused a six-week delay for mitigation, according to the audit.
“The Bureau exposed the 2020 Census preparations to potentially catastrophic risk by not securing root user accounts,” said the audit (p. 9). At the time, no one even knew there was massive exposure. Sources later claimed hackers from Russian IP addresses gained access. The Bureau does not know if data or systems were compromised.
“The 6-week timeframe it took to secure its root user accounts demonstrates the Bureau’s inability to have stopped a potential attacker with stolen root keys from modifying or destroying all cloud system resources hosted in its GovCloud environments,” the audit concluded (p. 9).
Setting a baseline for cloud security
Aside from the obvious securing of cloud root user keys, news about the audit did not say much about OIG’s key prescription for improving general cloud security – namely, the need to set a baseline of security information with ongoing assessments in order to know if a variation signals an attack is in motion. The audit said (p. 13) inaccurate baselines were created and then not implemented. “These inconsistently implemented baselines led to a weakened and vulnerable security posture of the environments. As a result, the Bureau was in violation of federal standards to implement its security baselines.”
Readers of Exabeam’s blog know we have a lot to say about security baselines! And while the OIG audit focused more on cloud configuration baselines, the concept of baselining all activity in your cloud environments is the bedrock of accurate threat detection and rapid response. Here are a few ways that a modern Security Information and Event Management (SIEM) platform with User and Entity Behavior Analytics (UEBA) could strengthen 2020 Census security – and do the same for your own enterprise clouds.
Protecting the census platform
The 2020 Census platform includes a central website with 52 separate systems, 27 of which are for data collection. A big portion of the Bureau’s multi-billion-dollar project is reportedly being implemented by seven contractors and 41 subcontractors. The complexity of this platform requires an approach to security that is interoperable across all cloud systems, networks, hosts, devices and data – and is able to immediately cut through the clutter of noisy alerts to identify probable attacks.
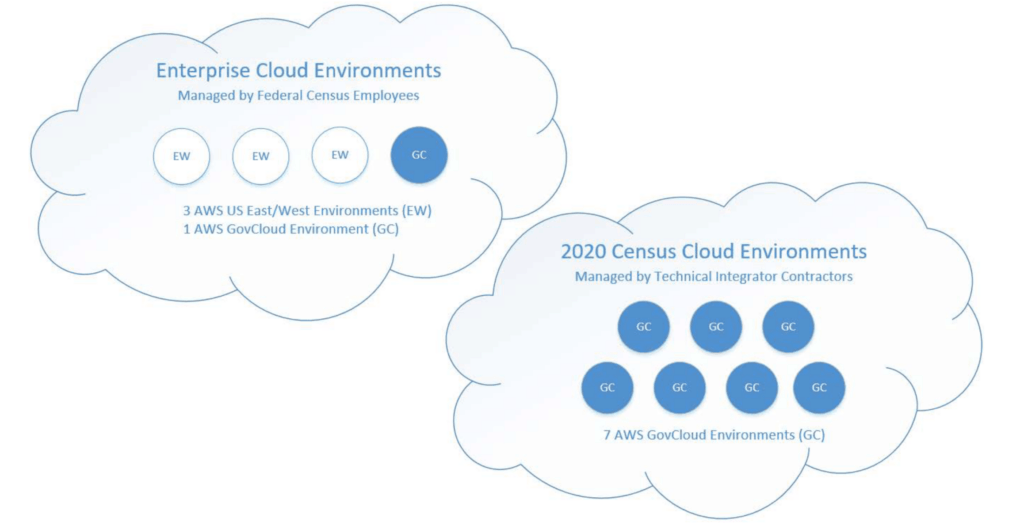
Figure 2: The U.S. Dept. of Commerce Office of Inspector General (OIG) published the Bureau’s AWS cloud environments for the 2020 Census.
UEBA solutions achieve this result by using artificial intelligence and machine learning (ML), advanced analytics, data enrichment, and data science to effectively combat advanced threats. The UEBA solution combines all the data sources together for analysis and automatically synthesizes results. Analysts get a lower volume but higher fidelity feed instead of drowning in alerts.
UEBA also would be valuable for the 2020 Census scenario because it has a low maintenance overhead. The ML system tunes itself via behavioral modeling. It identifies unknown attacks by looking for abnormalities instead of a limited, pre-determined set of activities and maps these activities to a baseline of normal behavior.
For example, UEBA can identify compromised census system elements by monitoring several vectors, including: user accounts to identify anomalous activity and alert analysts with the data they need to understand if a privileged user account was breached; servers for detecting deviations from baseline activity; network devices to monitor traffic over time and detect unusual spikes, non-trusted communication sources, insecure protocols, and other signs of malicious behavior; and anti-virus/malware monitoring to detect protection disablement or removal, or status of threat updates.
In a cloud context, a UEBA solution provides cloud connectors for AWS that can both ingest it as a data source and automatically kick off incident response actions for AWS. Exabeam provides connectors for any cloud provider, which makes it ideal for a multi-cloud hybrid scenario. The UEBA solution also provides integrations with all major identify and access management (IAM) vendors to collect more data for enriched insights into threats.
Preventing a breach of census data
An attack strategy might aim to cast doubt on results of the census. But some attackers may desire more by attempting breaches to steal or alter census data. Those tactics, techniques and procedures (TTPs) can trigger a variety of use cases that are easily handled by a UEBA solution. The most common use case is compromised user credentials, which provide stolen or mishandled keys to legitimate access. Legacy security tools are unable to distinguish when an attacker gets access via an authorized user’s credentials. By comparing all access attempts to baseline behavior, UEBA is able to detect unauthorized access across a combination of a user’s account credentials, devices or IP addresses.
Another use case is lateral movement detection, a scenario where attackers systematically move through a network in search of sensitive data and assets. Perhaps the attack began by compromising a low-level employee’s or contractor’s account. Once inside, the hacker probes other assets for vulnerabilities in order to switch accounts, machines and IP addresses. Opportunity presents itself once the attacker secures administrative privileges. Lateral movement is extremely difficult to detect by legacy security tools because parts of the attack are scattered across the IT environment, spread among different credentials, IP addresses and machines; the seemingly unrelated events all appear to be normal. The lateral movement detection UEBA use case is critical for detecting these breaches in the 2020 Census platform. The UEBA solution uses behavioral analysis to connect the dots between “unrelated” activity and stops these attacks before damage occurs.
Improving mobile census device security
The 2020 Census will employ 400,000 to 500,000 census takers who, starting in May, will visit unreported residences to collect data. In an effort to speed data collection, these temporary employees will, for the first time, enter data electronically via mobile devices instead of using pen and paper. The Bureau expects a 50 percent increase in productivity. Those of you in cybersecurity will immediately see the hacking potential caused by this major upsizing of the attack surface.

Figure 3: A mobile workforce will use mobile apps on phones and tables to gather information during the 2020 Census.
Securing the mobile device scenario is a good use of entity analytics technology within UEBA. The solution ingests operational data from many sources and uses analytics such as machine learning and behavior analysis to determine what is “normal” behavior by entities on the 2020 Census network. The census platform includes many entities such as hosts, applications, network traffic and data repositories, IoT devices – and the half million temporary mobile devices used by census takers.
Entity analytics would create baselines of behavior for each and every mobile device. As anomalous activity is identified, it is assigned a risk score. The score rises with increasing amounts of anomalous behavior until it crosses a predefined threshold. Upon this escalation, entity analytics sends an alert to security operations center analysts who use the data for investigation and appropriate remediation of threats via the mobile census device threat vector.
Toward a safer, secure 2020 Census
We mentioned the Census Bureau has acknowledged the need for improving 2020 Census security; in response to the audit (Appendix C), it pledged to “implement a significant amount of the recommendations in the report.” For example, the Bureau says it has implemented AWS Prowler, which is a command line tool for AWS security best practices assessment, auditing, hardening and forensics readiness. This is a good step, but we believe the Bureau can do more by applying UEBA and machine learning to all the systems, devices, data and people used for the 2020 Census. In these days of wily global opponents, it’s vital to use all of the advanced tools at our disposal to keep the nation’s census safe and ensure accurate, trusted results.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!