Insider threats, whether malicious or compromised, are among the most elusive and frequently overlooked cybersecurity concerns. Traditional security information and event management (SIEM) systems just don’t seem to cut it when it comes to defining the baseline of typical behavior for an insider. By now we’ve all seen the headlines about classified U.S. government documents being leaked on Discord by a military base employee working in cyberdefense operations. It’s equal parts shocking and unsurprising to read the details of incidents like these. This particular individual managed to snap photos of classified military documents and casually shared them in a Discord chat group.
In this article:
- Insider threats: the sneakiest of them all
- Recognizing potential internal adversaries
- Signs you’ve got an insider on your hands
- Why behavior-based solutions are the way to go
- Is prevention the goal?
- Wrapping up
Insider threats: the sneakiest of them all
As we learn more about the Discord leak, one thing is extremely clear: insider threats are incredibly hard to detect due to the complexities of pinpointing abnormal behavior.
Code42’s 2023 Annual Data Exposure Report offers some insights:
- CISOs find insider risk harder to detect than cloud data exposures and malware/ransomware.
- The average cost of an insider incident is a whopping $16 million, usually accompanied by catastrophic reputational damage and compliance consequences.
Recognizing potential internal adversaries
When it comes to tackling insider threats, you need to shift your mindset about what — and who — could pose a risk . Potential adversaries include employees, temporary workers, contractors, vendors, partners, and even executives who might have access to your organization’s most sensitive data. Privileged users and admins are particularly tricky, since their roles demand broad access to information. In the Discord leak case, it appears the leaker was a privileged user, making unusual activity that much harder to detect, since he wasn’t technically breaking any cybersecurity rules when accessing sensitive resources.
Signs you’ve got an insider on your hands
There are plenty of telltale behavioral indicators to watch for, but considering recent news, here are some key ones you should be aware of:
- Downloading confidential or unauthorized data to external drives, using unauthorized external storage devices, or printing confidential or unauthorized material
- Escalating privileges
- Accessing confidential data unrelated to the user’s role
- Network crawling, data hoarding, or copying from internal repositories
- Deviations from typical working patterns
Remember, insider threats aren’t just a single event, but a series of actions that collectively create a discernible threat.
Why behavior-based solutions are the way to go
Insider threats tend to evolve over an extended period of time and slip past traditional rule- and signature-based detection methods. The trick is to proactively identify changes in behavior and patterns, like copying and staging files for later exfiltration or creating new accounts, to uncover malicious intent.
Exabeam delivers a behavior-based solution that uses advanced analytics to assign a risk score to each user, helping security operations teams to quickly identify notable users by their actions. By incorporating machine learning and risk-based scoring, Exabeam connects the dots on user activity and highlights significant events that warrant investigation. Smart Timelines™ automatically piece together security incidents to fast-track the investigation and response process. This spares security analysts from having to manually assemble them — which can take days — enabling a faster and more efficient response to unauthorized activity.
Here’s an example of detecting a data leak, which is notoriously challenging because it often closely mimics normal activity.
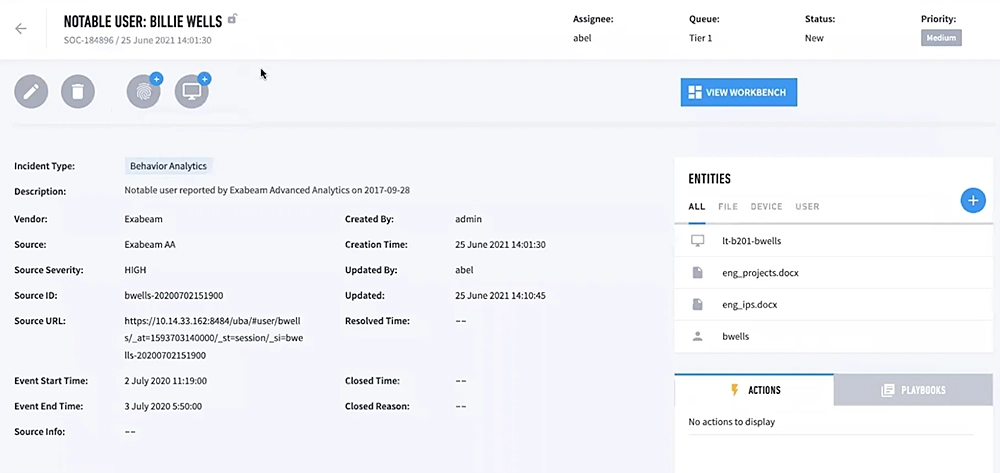
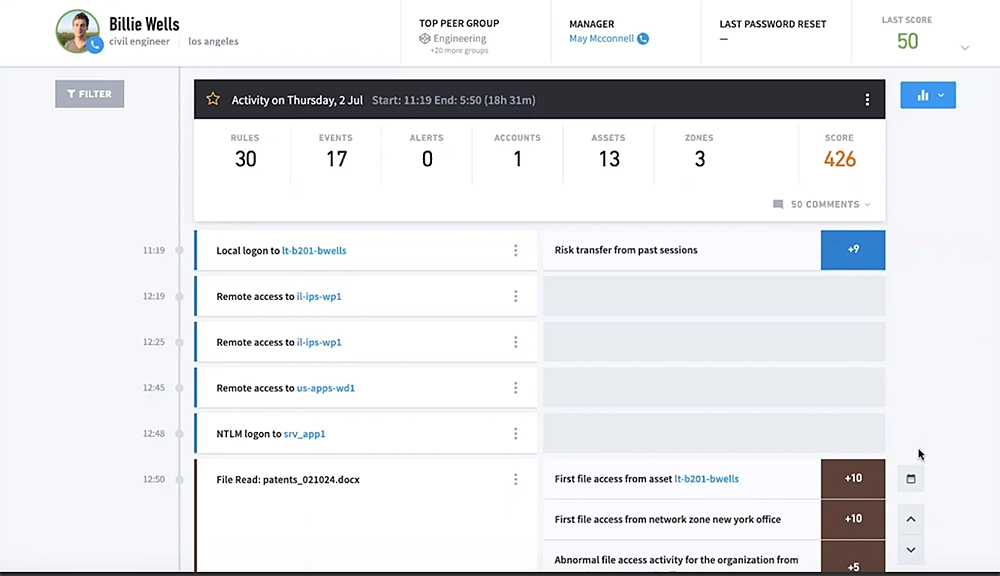
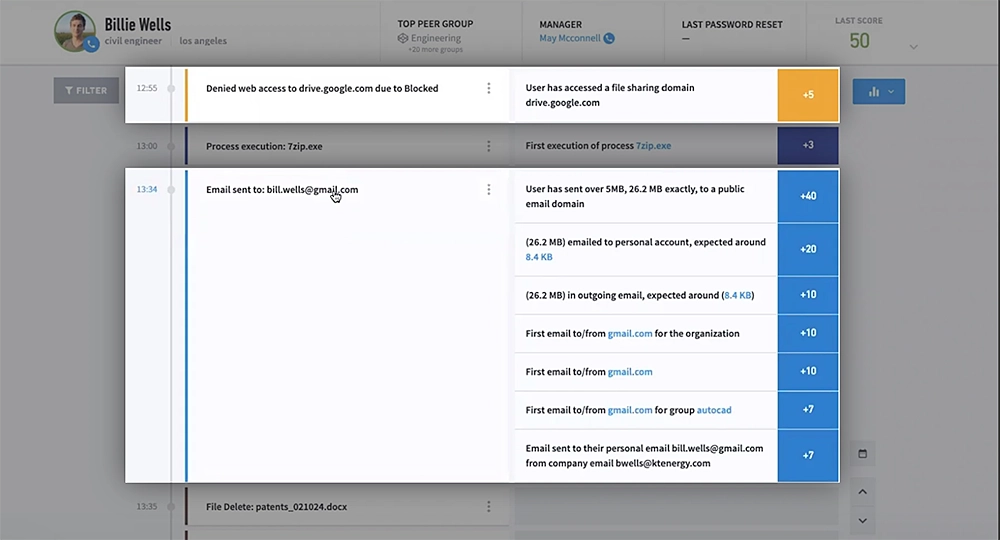
Exabeam connects DLP alerts with authentication, access, and contextual data sources to generate a comprehensive timeline of each user’s activity. This complete view of a user’s activity enables security analysts to accurately determine if an insider is acting with malicious intent and take the necessary steps to prevent potential damage from escalating incidents.
Key data sources to monitor data leak activity include:
- Web security and monitoring
- Print activity
- Data loss prevention
- Email security and management
- File monitoring
- Database activity monitoring
- Endpoint security (EPP/EDR)
Key detection rule types to implement:
- Data leak
- Data leak via email
- Data leak via printer
- Data leak via a removable device
- Data leak via web
Keep in mind that a single activity doesn’t necessarily indicate an insider threat. For instance, if a user uploads an unusually large email to their personal account, this alone might not be cause for concern. However, when coupled with other abnormal behaviors, the action can be flagged as suspicious. Security analysts can then easily place users on a high watch list, and even revoke access to resources if additional suspicious behavior is discovered. And Exabeam offers threat hunting capabilities that enable security analysts to proactively search for threats based on identified behavioral patterns and user context.
Is prevention the goal?
Is it possible to prevent insider threats to your organization with the right tools? The truth is that no tool can guarantee prevention. But monitoring, detecting, investigating and responding to threats is absolutely critical, and the most effective approach is through user and entity behavior analytics (UEBA).
Of course, not every incident makes headlines, and many cases go undetected or unreported — sometimes for years. What’s certain is that insider threats pose a security risk to every organization, so it’s crucial to account for it in your planning, given the severe consequences that can result from a successful attack.
Wrapping up
The Discord leak serves as a wake-up call, highlighting how classified document leaks can put defense personnel at risk and tarnish government agencies’ reputation. Utilizing behavior-based modeling techniques, security teams can establish a baseline for normal behavior, enabling them to. detect and track abnormal activity, map it to potential attack scenarios, and intervene before devastating financial or reputational damage occurs. By implementing solutions like Exabeam, organizations and government agencies alike can bolster their defenses against insider threats and keep their data secure.
Come talk with our team at RSAC booth #2039! Learn how to detect hard-to-find threats, defend against cyberattacks, and defeat the adversaries
Want to learn more about detecting compromised credentials?
Read our white paper, Detecting Compromised User Credentials.
Despite increased security budgets and expanding teams, exponentially larger data breaches continue to happen. Most of the biggest breaches have involved credential-based attacks — attackers leveraging stolen user credentials to masquerade as employees, gain access, escalate privileges, and obtain important data that should only be available to those with the highest level of access.
Many companies have turned to big data solutions — often bolted onto a SIEM — to collect and analyze the plethora of data generated within their environment. While capturing and analyzing data is important, much of it doesn’t help identify attackers who look like legitimate users. Detection of attackers who have obtained authorized credentials requires a new mindset: the attacker is already inside.
Read the white paper and learn:
- How a system that learns credential behaviors and characteristics detects attackers who look like legitimate employees going about their normal business
- How to find attackers that switch identities
- Where credentials enable attack chain functions
- How UEBA helps cut through the noise of alerts to quickly identify and mitigate real threats

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!














