The Exabeam Security Research Team (ESRT) reviewed the attack characteristics of 24 recent breaches, and this article outlines some of our findings.
The most common initial attack vector is stolen or compromised credentials, averaging $4.5 million per breach, according to the 2022 Cost of a Data Breach Report. And the costliest initial attack vector was phishing, at an average of $4.91 million.
Phishing emails are one of the most common ways attackers attempt to trick users into providing their user credentials and other information via links to websites that imitate legitimate ones.
The recent Twilio data breach was a textbook example of the risks associated with phishing links. Twilio writes, “On August 4, 2022, Twilio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials. This broad based attack against our employee base succeeded in fooling some employees into providing their credentials. The attackers then used the stolen credentials to gain access to some of our internal systems, where they were able to access certain customer data.”
In this article, we’ll give some background on phishing and walk you through the steps involved in a phishing investigation.
In this article:
- What is phishing?
- 4 steps for investigating a possible email phishing incident
- How Exabeam can ease the load
- Conclusion
What is phishing?
Phishing is a cybersecurity threat that uses social engineering to lure individuals into providing sensitive data such as personally identifiable information (PII), banking and credit card details, and passwords.
Phishing emails, most of the time, can be identified by of these common indicators:
- Too good to be true
- Sense of urgency
- Hyperlinks
- Attachments
- Unusual sender
We know it is tough to monitor all employees. It is likely not a question of if they will get phished, but when, so what are the best practices for what to do in a phishing scenario?
Let us imagine we are already in a phishing investigation.
We receive a suspicious email at this point, and we don’t know whether it is malicious or not. So, what would be the best tasks to follow to be successful and prevent/reduce the impact on the business?
The first thing we need to do is investigate. It is best to have a workflow commonly known as a playbook that is repeatable and can be used for every phishing investigation.
4 steps for investigating a possible email phishing incident
- Analyze the contents of the headers.
What does the header contain? Does it come from a reputable domain? Does it contain SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance) records? Not having an SPF record, even though it is not a clear indicator that the email is spoofed, opens the door for your domain to be spoofed, since you don’t limit the IPs who can send the IP with your domain.
DKIM is an email security standard that could help detect if the email has been tampered with before it reaches its final destination. DMARC uses SPF as one of its foundations but adds more features, so if DMARC does not match the SPF, it could lead to a possible spoofed email. Do these records match? Is there a possibility of being spoofed?
Does the IP address come from a reputable location? Leverage your threat intel platform or use free ones available online to check the reputation of the IP. Make a reverse DNS request, and do a nslookup query. Reverse DNS will help get the translation from the IP to the DNS that serves this domain. Presenting a DNS that doesn’t match the current domain could be a good indicator that this email is not coming from an actual server, but a client. nslookup will query a specific DNS server and retrieve the requested records associated with the domain you provided. Doing a reverse DNS and nslookup together can help you find if this email comes from a reputable email server.
When we make a WHOIS request, does the domain come back as a reputable business? By making a WHOIS request, you get more information about the domain you are querying, like the creation date and expiration date. This is useful since disposable domains will have a rather new creation date, and the registrant information wouldn’t match the information from a real business.
- Collect information from the body.
- Does it contain links?
- Does the message reflect a sense of urgency and/or sound too good to be true?
- Does the body provide little details on the message and push the victim to click links or open attached files?
- Analyze the URL/file collected.
- Submit links/URLs for reputation analysis. Does it come back as malicious?
- Find related domains using OSINT (open-source intelligence).
- Run attachments through a file/hash sandbox. Do they contain potentially malicious results?
- Determine the impact.
- Who else got this email?
- Was it spear phishing or a phishing campaign?
- Did the victim click the URLs in the body of the email?
- Did they open the attached files? If yes, is any account and/or critical asset compromised?
If any of these comes back as potentially malicious, another process might be needed.
Since attackers know that organizations focus on phishing attacks, to avoid detection they rarely reuse domains, links, and attachments; but they may continue to use the same template. From the investigation, one could find keywords that could be helpful for filtering from preventing new emails from the same attacker. Although an essential task is to check if the email recipient’s account was compromised — since one of the bigger goals from a malicious actor is to gain access to accounts — check if there is any behavior of note for this user account example:
- Has abnormal behavior been exhibited from the user’s account or asset after receiving the email?
- Have there been any logins from new locations and access to new applications and systems?
- Are we getting more network traffic from the IP that sent the email?
- Have any other security tools triggered an alert for this user?
- Is this account or asset part of another watchlist?
- Has the email been removed from the user’s inbox to prevent accidental clicks on the malicious attachments?
How Exabeam can ease the load
Exabeam can be helpful during an investigation, because we can automate and streamline specific repetitive tasks that otherwise would be time-consuming.
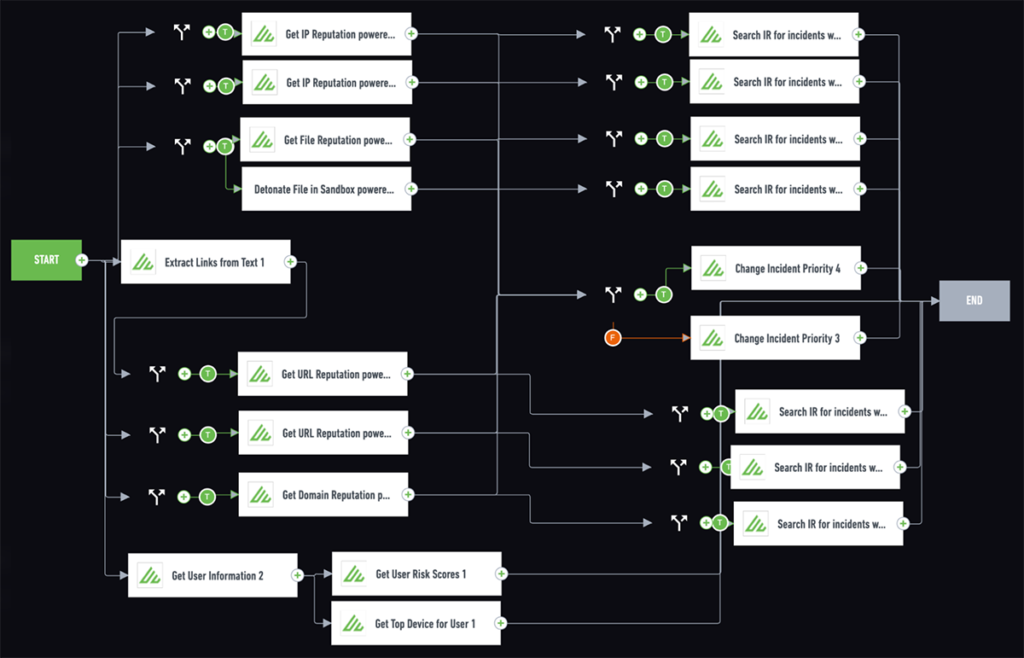
Exabeam can automate much of the phishing investigation process by ingesting all suspicious emails, parsing the contents, and analyzing the various artifacts using pre-built integrations without any setups or the need for other security solutions.
Steps in the Exabeam Phishing Playbook:
- Parse the email into a case
- Separate the header from the email for analysis.
- Use part of the email into case fields so they can be actionable.
- Analyze the attached URL/files attached to the email.
- Check email for potential phishing wording.
- Check the domain through OSINT.
- Check if another user has received this email.
- Check the user account for other Security Alerts.
Conclusion
Organizations should attempt to address potential phishing attacks as rapidly as possible by identifying and alerting these malicious links. Innovative organizations need a modern approach to securing their environments in order to identify these types of attacks quickly. To help achieve this, machine learning-powered SIEM, automated investigation and response tools, and UEBA technology should absolutely be part of their security stack.
Exabeam Security Research Team (ESRT) Mission Statement:
The ESRT strives to provide unique insight into how we look at the world of cyberthreats and risk by highlighting the common patterns that different threats and threat actors use, and why we need to reorient our detections and priorities to tactics, techniques, and procedures (TTPs) vs. indicators of compromise (IOCs).
We aim to share a newer ideology of investigating threats by answering the following questions: “who, what, and how”.
Want to learn more about phishing investigations?
Read our guide to mitigating phishing attacks to make sure you understand the common challenges of phishing attacks, and get five steps you can take to protect your organization.

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













