
Table of Contents
What Are SOAR Tools?
SOAR tools, short for Security Orchestration, Automation, and Response, are platforms that help cybersecurity teams manage and respond to security threats more efficiently. They work by integrating various security tools, automating repetitive tasks, and orchestrating complex incident response workflows through predefined “playbooks”. Key benefits include increased productivity, faster response times to threats, better use of resources, and a centralized view of security activities, leading to a stronger overall security posture.
The primary goal is to improve the efficiency and effectiveness of security operations centers (SOCs) by automating repeatable tasks and offering a centralized environment for incident management. The tools collect security data from multiple sources, correlate the information, and trigger rule-based responses without the need for constant human intervention.
SOAR improves incident response times and allows security analysts to focus on higher-priority tasks that require human judgment. As a result, SOAR platforms are now an essential component for organizations aiming to mature their security posture and manage the ever-increasing volume of alerts and security events.
Features and Capabilities to Look for in SOAR Tools
Integration Capability
A SOAR platform’s effectiveness strongly depends on its ability to integrate with a wide array of security products, such as SIEM, firewalls, endpoint protection, threat intelligence feeds, ticketing systems, and more. Robust integration support yields a unified workflow, enabling seamless data exchange and simplified incident response. Organizations should prioritize SOAR solutions with extensive APIs, prebuilt connectors, and easy customization to extend integrations as their environments grow and diversify.
Lack of integration flexibility results in information silos and reduces the value of orchestration and automation. When evaluating SOAR tools, ensure they can accommodate both legacy and modern security systems, and that they provide mechanisms to create custom connectors for homegrown or niche point solutions.
Playbook / Runbook Flexibility
Modern SOAR platforms rely on playbooks (or runbooks) to automate investigation, triage, and response. The platform should offer intuitive playbook editors and flexibility to tailor workflows to adapt to evolving threats, use cases, and internal processes. Essential functions include branching logic, conditional actions, user prompts, automated approvals, and the ability to call external services as part of workflows.
Relying on rigid, limited playbooks restricts the SOAR tool’s value. Analysts should be able to create, modify, and test playbooks without extensive coding knowledge, while advanced options (such as scripting support) should be available for complex automation scenarios. Playbook versioning, auditing capabilities, and reusable components further simplify automation deployment.
Alert Management
SOC teams face overwhelming alert volumes. SOAR tools must intelligently collect, deduplicate, enrich, and prioritize incoming security alerts from heterogeneous sources. Effective alert management reduces noise, guides analysts toward relevant incidents, and provides automated contextualization with threat intelligence and asset information.
Automation capabilities should extend to responding to common alert patterns, escalations, and false positive suppression. Analysts benefit from alert grouping, timeline visualizations, and correlation to related incidents. The SOAR solution should provide robust alert tracking and notification mechanisms so that critical issues are surfaced rapidly and routine ones are handled automatically.
Case / Incident Management
At the heart of SOAR platforms lies a robust case or incident management system. This feature enables analysts to track, document, and coordinate responses to security events, ensuring visibility and accountability throughout the incident lifecycle. The platform should support comprehensive evidence collection, workflow assignment, collaboration features, and time-stamped audit trails for each case.
Effective incident management extends to linking related alerts, tracking mitigation actions, and preserving forensics for post-incident analysis. SOAR tools should allow customizable case templates, enable role-based access control, and offer seamless integration with ticketing or ITSM solutions to align with broader business processes.
Reporting, Dashboards, Metrics and Analytics
Visibility into SOC activities is critical for operational success. SOAR tools should provide customizable dashboards and automated reporting to surface key security metrics, such as response times, incident volumes, automation efficacy, and analyst workload. Real-time and historical analytics enable organizations to spot trends, uncover gaps in detection or response, and justify investments to stakeholders.
Beyond basic reporting, advanced SOAR platforms deliver drill-down capabilities, interactive data visualization, and integration with business intelligence tools. Automated and scheduled reports can be tailored for executive, compliance, or technical audiences, ensuring all stakeholders remain informed.
Scalability, Performance, and Reliability
A SOAR platform must scale with an organization’s needs, handling surges in alert or incident volumes without performance degradation. Scalability includes support for distributed or multi-tenant architectures, horizontal scaling, and high-availability deployment options to minimize downtime and business impact. Responsive user interfaces and low-latency automation execution ensure analysts remain effective even during peak periods.
Reliability also includes built-in fault tolerance, disaster recovery features, and robust support for upgrade or patching cycles without data loss. Monitoring and alerting on SOAR health, system utilization, and workflow status prevent technology from becoming a bottleneck.
Compliance, Audit and Governance Support
Organizations across regulated industries need SOAR tools to aid compliance, audit, and governance efforts. Centralized incident records, immutable audit trails, and detailed documentation of every response action make it easier to demonstrate regulatory adherence. SOAR platforms should automate evidence collection, maintain chain-of-custody records, and support custom reporting for compliance frameworks such as GDPR, HIPAA, or PCI DSS.
Advanced SOAR solutions offer granular role-based access control and customizable data retention policies to protect sensitive information and ensure only authorized personnel have access. Workflow approvals, sign-off tracking, and clear escalation paths underpin effective governance.
Notable SOAR Tools
1. Exabeam

Exabeam combines SIEM, UEBA, and built-in automation to streamline threat detection, investigation, and response. It unifies telemetry from identity systems, endpoints, networks, cloud services, and threat intelligence into a single analytics layer, then automates investigations and playbook-driven actions. The Nova agentic AI accelerates case summaries, suggests next steps, and helps analysts prioritize response while low-code playbooks orchestrate actions across the stack.
Key features include:
- Integrated SIEM and SOAR: Exabeam’s SIEM provides advanced log management and behavioral analytics that feed its automation capabilities. Detections can trigger standardized response workflows, allowing analysts to move from alert to action without switching tools.
- Low-code playbooks and workflow automation: Prebuilt and customizable playbooks enable rapid containment, eradication, and recovery. Analysts can view, modify, and reuse workflows to match evolving threats and operational preferences.
- Agentic AI for faster TDIR: Nova’s agentic AI automatically summarizes cases, classifies threats, identifies attack paths, and recommends next steps, reducing mean time to respond by 80% and improving consistency.
- Behavioral analytics and risk-based prioritization: Exabeam’s UEBA models typical user and entity behavior to establish baselines. When deviations occur, it assigns dynamic risk scores that help analysts focus on the most critical threats and automate related responses.
- Broad ecosystem integrations: The platform connects with EDR, NDR, IAM, cloud security, and ticketing systems to enrich alerts and execute response actions such as account lockdown, device isolation, or policy updates.
- Incident response at scale: Machine-built timelines, guided investigations, and automated workflows reduce manual effort throughout the entire detection and response lifecycle.
2. Cortex XSOAR

Cortex XSOAR is a SOAR platform to help SOC teams automate, orchestrate, and centralize their incident response processes. It enables organizations to reduce the time and effort required to manage incidents by automating repetitive tasks, enriching alerts with context, and enabling real-time collaboration.
Key features include:
- Automation-first design: Offloads routine, time-consuming tasks to automation, reducing manual work and analyst fatigue
- Integrated war room: Centralized interface for real-time collaboration, investigation, and incident management
- Visual playbook editor: Code-free interface for building and customizing workflows with thousands of ready-made actions
- Extensive integrations: Over 900 prebuilt integration and automation packs to connect with tools across the security stack
- Accelerated Investigations: Consolidates threat intel, indicators, and incident data to simplify investigation workflows

Source: Microsoft
3. Splunk SOAR

Splunk SOAR is a security orchestration, automation, and response platform that unifies security operations across tools, teams, and processes. It integrates with Splunk Enterprise Security to offer a native, data-driven incident response experience. It enables teams to automate security tasks, orchestrate complex workflows, and make faster decisions.
Key features include:
- Automated playbooks: Execute security actions in seconds using a wide range of customizable playbooks, aligned with frameworks like MITRE ATT&CK and D3FEND
- App integrations: Supports over 300 third-party tools and over 2,800 automated actions to connect the entire security stack without replacing existing tools
- Visual playbook editor: Drag-and-drop interface simplifies playbook creation for users of all skill levels, enabling rapid development of automation workflows
- Integrated case management: Built-in tools for task assignment, tracking, and documentation ensure end-to-end incident handling within a single system
- Threat intelligence integration: Embedded threat insights from the Splunk Threat Research Team help prioritize alerts and guide investigations
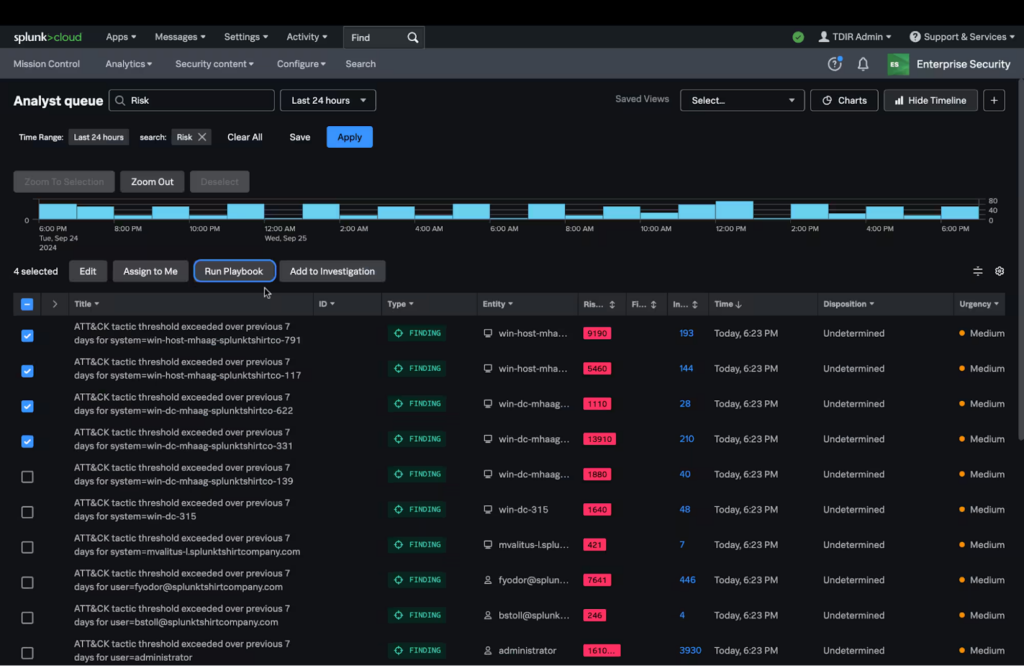
Source: Splunk
4. FortiSOAR

FortiSOAR is Fortinet’s security orchestration, automation, and response platform designed to centralize incident management, standardize processes, and automate analyst workflows across IT and OT environments. It acts as a central operations hub, helping security teams reduce manual effort, respond faster, and enforce consistent best practices.
Key features include:
- Centralized incident management: Consolidates alert investigation, response, and documentation to simplify analyst workflows across SOC, NOC, and OT environments
- AI-driven automation: FortiAI and the built-in recommendation engine use generative AI to assist with playbook creation, threat investigation, and response decisions
- Prebuilt content library: Over 800 ready-to-use playbooks and 500+ integrations provide rapid time-to-value and support a wide range of use cases
- No/low-code playbook builder: Drag-and-drop interface enables rapid workflow design with patented visual tools, reducing reliance on coding skills
- Threat intelligence: Integrates FortiGuard Labs data and public intelligence sources to enrich alerts and enable more informed responses
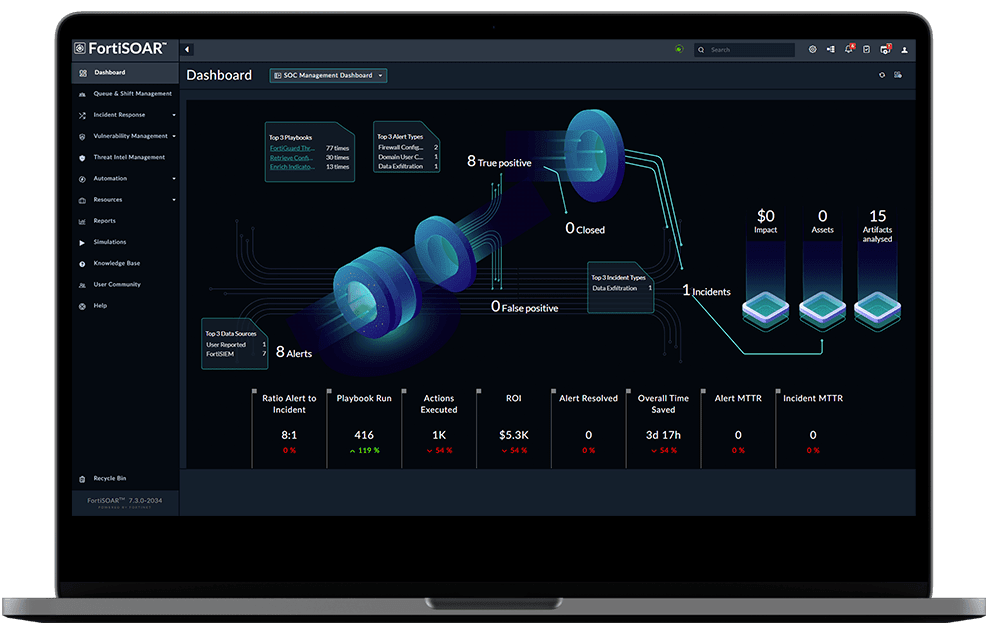
Source: Fortinet
5. Cyware

Cyware offers a low-code, vendor-agnostic SOAR platform to unify and automate threat detection, analysis, and response across diverse environments. It simplifies security operations by integrating with cloud and on-premise tools, enabling end-to-end automation of cybersecurity, IT, and DevOps workflows.
Key features include:
- Low-code workflow automation: Visual playbook editor with drag-and-drop functionality and over 100 prebuilt templates enables fast, flexible automation development
- Vendor-agnostic orchestration: Decoupled architecture allows orchestration gateway deployment independent of incident management, supporting full-stack integration across any toolset
- Automated threat intelligence actioning: Natively automates ingestion and actioning of ISAC-shared and other threat intel across SIEM, EDR, NDR, firewall, and other detection/response systems
- Unified case and threat management: Single-pane interface for managing malware, vulnerabilities, threat actors, and incidents with analyst mapping, SLA tracking, and centralized governance
- Cloud and on-premise coverage: Uses lightweight agents to orchestrate security workflows across hybrid environments without requiring external network exposure
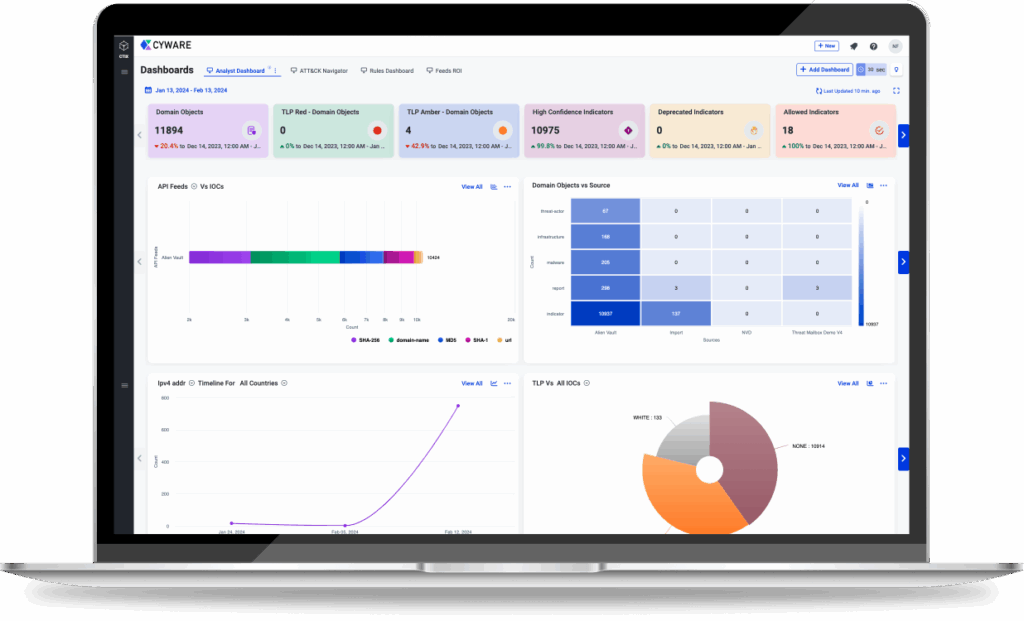
Source: Cyware
Conclusion
SOAR tools are a critical enabler for modern security operations, helping organizations manage increasing alert volumes and complex threat landscapes with greater speed and efficiency. By automating repetitive tasks, orchestrating multi-step workflows, and centralizing incident management, these platforms free up analysts to focus on higher-value activities. Their integration capabilities and built-in intelligence streamline response efforts and reduce the likelihood of human error.
More SOAR Explainers
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Making the Switch: A Step-by-Step Guide to Migrating from On-premises to Cloud-native SIEM
- Show More



