
Microsoft Sentinel: 5 Key Features, Limitations and Alternatives
- 7 minutes to read
Table of Contents
What is Microsoft Sentinel?
Microsoft Sentinel (formerly Azure Sentinel) is a cloud-native security information and event management (SIEM) and security orchestration automated response (SOAR) solution. It integrates with Azure cloud services, providing security analytics and supporting incident response. It helps security analysts detect, investigate, and respond to threats.
The platform uses AI and machine learning to analyze data. This aids in identifying potential threats and vulnerabilities more accurately. Like with others, users can correlate data from multiple sources, including cloud services, on-premises systems, and third-party providers.
Key Features and Capabilities of Microsoft Sentinel
Microsoft Sentinel provides the following features that support security operations.
This is part of a series of articles about information security.
1. Data Collection and Integration
Microsoft Sentinel supports numerous connectors, enabling integration across cloud platforms such as Azure, AWS, and GCP, as well as on-premises environments. This capability intends to provide visibility into potential threats. Sentinel’s ability to integrate logs and signals without additional infrastructure investment may be useful for security monitoring within diverse IT environments.
Data collected by Sentinel is normalized and enriched to enhance threat detection and incident analysis. This process involves tagging, parsing, and correlating data automatically, which streamlines security operations.
2. Threat Detection and Analytics
Threat detection within Microsoft Sentinel intends to identify complex threats. By using behavioral analytics and anomaly detection, the platform identifies unusual activities and potential threats that traditional methods may overlook.
Sentinel’s analytics capabilities can enable custom rule creation and alerting, in the hopes that organizations receive timely notifications of suspicious activities.
3. AI-Powered Investigation
Sentinel’s AI-powered investigation tools simplify the process of threat exploration and resolution. The use of AI accelerates the investigation phase by providing potential insights into attack patterns and possible threat actors. It offers hunting capabilities that intend to allow analysts to search deeper into alerts and related incidents.
Additionally, artificial intelligence is used to automate repetitive tasks, construct incident timelines, and visualize attack vectors.
4. Automated Incident Response with Playbooks
Automated incident response in Microsoft Sentinel is powered by playbooks that standardize response efforts. These playbooks are collections of procedures executed automatically in response to specific incidents. Like all playbooks from other vendors, they are intended to reduce response times and minimize human intervention needed during critical periods.
Automation intends to allow organizations to handle a higher volume of alerts. By utilizing pre-defined workflows, Sentinel intends that each incident is managed consistently while reducing human error.
5. Behavior Analytics and User Entity Behavior Analytics (UEBA)
Behavior analytics and UEBA within Microsoft Sentinel focus on identifying deviations from typical user behaviors. Sentinel leverages these analytics to potentially detect insider threats, compromised identities, and advanced persistent threats by assessing patterns in user activities and flagging anomalies.
UEBA provides context around user actions by analyzing baseline activities alongside current behavior metrics. This approach identifies irregularities, enabling security teams to quickly respond to potential breaches.
Microsoft Sentinel Limitations
While Microsoft Sentinel is a respected solution, it has several limitations that organizations should consider before implementation. These limitations were reported by users on the G2 platform:
- High cost for large data volumes: Microsoft Sentinel’s cost structure, based on data ingestion, can lead to high expenses, particularly for organizations processing large amounts of security data. Unpredictable data volumes may also make costs fluctuate unexpectedly.
- Complex user interface: The interface can be challenging to navigate, and understanding all its features requires a learning curve, especially for users new to Azure or Kusto Query Language (KQL).
- Integration challenges with non-Microsoft solutions: Although Sentinel integrates with Microsoft products, integrating with some third-party or older systems may require additional support and could be less efficient.
- Performance issues: Some users experience slow data query speeds, which can impact responsiveness in critical threat detection and response scenarios.
- False positives from AI capabilities: Sentinel’s AI-driven analytics may generate a high volume of false positives if not finely tuned, potentially leading to alert fatigue among security teams.
- Complicated log ingestion for private resources: Ingesting logs from private resources can be complex and costly, as it often requires using public APIs for data collection rather than a simple private connection.
- Technical expertise required: Configuring and customizing Sentinel to meet specific organizational needs may require technical expertise, adding to setup time and potential risks in deployment.
- Limited customization and parsing for certain logs: Customizing log parsing, especially for logs from sources like syslog, may present challenges, as Microsoft Sentinel’s parsing capabilities can be less adaptable compared to other SIEM tools.
Notable Microsoft Sentinel Alternatives
1. Exabeam

Exabeam is a leading provider of security information and event management (SIEM) solutions, combining UEBA, SIEM, SOAR, and TDIR to accelerate security operations. Its Security Operations platforms enables security teams to quickly detect, investigate, and respond to threats while enhancing operational efficiency.
Key Features:
- Scalable log collection and management: The open platform accelerates log onboarding by 70%, eliminating the need for advanced engineering skills while ensuring seamless log aggregation across hybrid environments.
- Behavioral analytics: Uses advanced analytics to baseline normal vs. abnormal behavior, detecting insider threats, lateral movement, and advanced attacks missed by signature-based systems. Customers report that Exabeam helps detect and respond to 90% of attacks before other vendors can catch them.
- Automated threat response: Simplifies security operations by automating incident timelines, reducing manual effort by 30%, and accelerating investigation times by 80%.
- Contextual incident investigation: Since Exabeam automates timeline creation and reduces time spent on menial tasks, it cuts the time to detect and respond to threats by over 50%. Pre-built correlation rules, anomaly detection models, and vendor integrations reduce alerts by 60%, minimizing false positives.
- SaaS and cloud-native options: Flexible deployment options provide scalability for cloud-first and hybrid environments, ensuring rapid time to value for customers. For organizations who can’t, or won’t move their SIEM to the cloud, Exabeam provides a market-leading, full featured, and self-hosted SIEM.
- Network visibility with NetMon: Delivers deep insight beyond firewalls and IDS/IPS, detecting threats like data theft and botnet activity while making investigation easier with flexible searching. Deep Packet Analytics (DPA) also builds on the NetMon Deep Packet Inspection (DPI) engine to interpret key indicators of compromise (IOCs).
Exabeam customers consistently highlight how its real-time visibility, automation, and productivity tools powered by AI, uplevel security talent, transforming overwhelmed analysts into proactive defenders while reducing costs and maintaining industry-leading support.
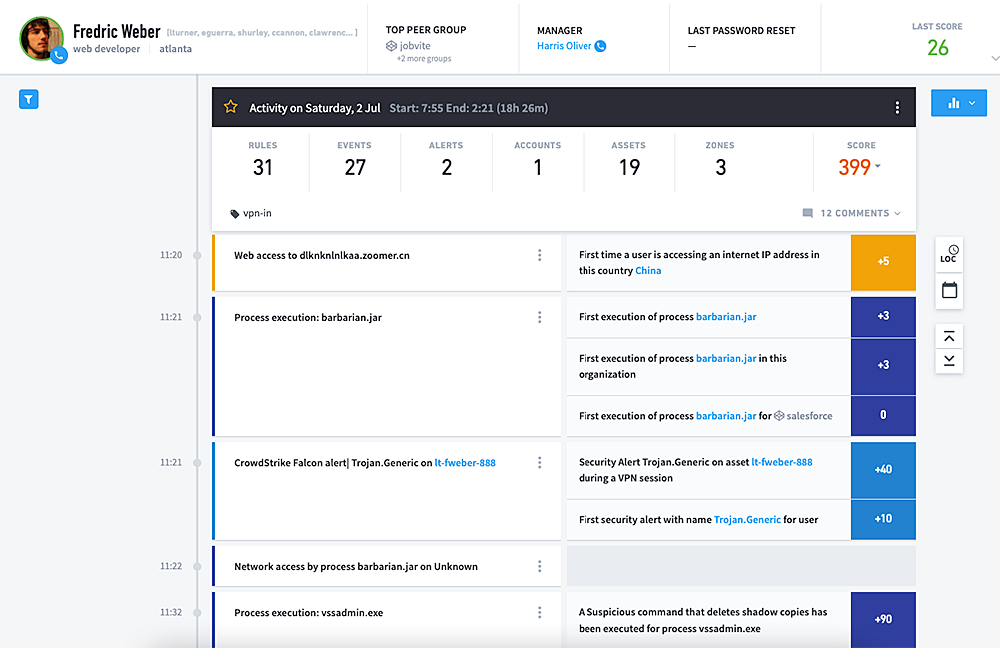
2. Splunk Enterprise

Splunk Enterprise is a platform designed to provide organizations with actionable insights from their data. It supports security, observability, and monitoring across environments.
Key features of Splunk Enterprise:
- End-to-end data visibility: Provides visibility across data sources, enabling monitoring from the edge to the cloud within a unified platform.
- Search and analysis: Supports in-depth data exploration, allowing users to analyze diverse data types and extract insights.
- Custom dashboards and visualization: Offers a dashboard-building experience, enabling custom visualizations that might help teams unlock and communicate insights.
- Real-time data streaming: Delivers data to hopefully enabling quick processing and distribution to Splunk or other destinations.
- Scalable data indexing: Ingests data at terabyte-scale from numerous sources.

Learn more in our detailed guide to Microsoft Sentinel vs Splunk
3. IBM Security QRadar SIEM

IBM Security QRadar SIEM is a security information and event management (SIEM) solution that supports security operations center (SOC) analysts with AI, threat intelligence, and automated incident correlation. It intends to reduce alert noise, prioritize risks, and provide SOC teams with alerts.
Key features of IBM Security QRadar SIEM:
- AI-driven alert prioritization: Uses AI to score and prioritize alerts.
- Automated incident correlation: Unifies related alerts, to potentially minimize false positives and reduce investigation time for security teams.
- Real-time threat intelligence: Integrates IBM X-Force Threat Intelligence, user behavior analytics, and network analytics.
- Sigma rules and federated search: Supports open-source SIGMA rules for seamless threat detection, along with federated search for quick access to distributed security data across platforms.
- User behavior analytics (UBA): Detects unusual user behavior to identify insider threats and account compromises.

4. SentinelOne

SentinelOne AI SIEM is a security information and event management platform for the more autonomous SOC. Based on the SentinelOne Singularity Data Lake, this SIEM solution provides detection, autonomous protection, and visibility across diverse environments, including endpoint, cloud, network, and identity systems.
Key features of SentinelOne AI SIEM:
- AI-enhanced threat detection: Leverages AI algorithms to detect threats by analyzing datasets.
- Real-time visibility: Offers a unified console with visibility across security events.
- Automated incident response: Features automated playbooks for incident response, reducing manual efforts and handling threat scenarios.
- Open ecosystem: Supports ingestion of both first-party and third-party data, with native support for the Open Cybersecurity Schema Framework (OCSF) and integration with various security stacks.
- Hyperautomation: Replaces traditional SOAR workflows, allowing SentinelOne to handle repetitive security tasks autonomously.

5. Rapid7 InsightIDR

Rapid7 InsightIDR is a cloud-native SIEM tool that supports hybrid and cloud-first environments. With a focus on speed, scalability, and actionable threat detection, it helps organizations simplify threat detection, incident response, and security management.
Key features of Rapid7 InsightIDR:
- AI-driven behavioral detection: Uses behavioral analytics and threat content to detect and alert on suspicious activity, providing insights into potential threats.
- Unified attack surface visibility: Combines endpoint, user, and network data into a single view, allowing teams to monitor their environment.
- High-context investigative timelines: Presents attack timelines with context on attack techniques, impacted resources, and recommended responses.
- Cloud-ready scalability: Built for cloud-first and hybrid environments, scaling with organizational growth and supporting agile development, SaaS adoption, and digital transformation.
- Embedded threat intelligence and MITRE ATT&CK alignment: Integrates a detection library mapped to the MITRE ATT&CK framework.

Conclusion
Microsoft Sentinel provides a cloud-native SIEM and SOAR solution that integrates with diverse data sources while enhancing threat detection and supporting automated response through playbooks. Its limitations include high costs for large data ingestion and challenges integrating with non-Microsoft systems, while its advantages include flexibility and scalability. When choosing a security management solution, organizations should consider their needs, data environment complexity, and integration requirements.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
SIEM Tools
Authored by Exabeam
- [Guide[ SIEM Tools: Top 5 SIEM Platforms, Features, Use Cases and TCO
- [Guide] Top 5 Free Open Source SIEM Tools [Updated 2025]
- [Guide] Best SIEM Solutions: Top 10 SIEM systems and How to Choose 2025
Bot Protection
Authored by Radware
- [Guide] Bot Protection: Attack Examples & 8 Ways to Defend Your Network
- [Guide] What Is a Botnet? Types, Examples, and 7 Defensive Measures
- [Product] Radware AI-Powered Bot Protection | Comprehensive Bot Management
Application Security
Authored by Oligo
- [Guide] What is Application Detection and Response (ADR)? 2025 Guide
- [Guide] Application Security in 2025: Threats, Solutions & Best Practices
- [Blog] Critical RCE Vulnerabilities in OpenSSH (CVE-2024-6387, CVE-2024-6409) – How to Detect and Mitigate
- [Product] Oligo | Real-Time Application Security & Risk Detection
More Microsoft Sentinel Explainers
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Making the Switch: A Step-by-Step Guide to Migrating from On-premises to Cloud-native SIEM
- Show More



