
-
- Home
>
-
- Blog
>
-
- SIEM Trends
The Significance and Role of Firewall Logs
- Mar 22, 2022
- Christopher Beier
- 6 minutes to read
Table of Contents
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. In addition, to this policy, firewall log information is needed to audit the security efficacy of the firewall.
Firewall logging records when and how access attempts are made, including source and destination IP addresses, protocols, and port numbers. A SIEM data lake uses this data to help investigate historic attacks and find evidence of probing.
Firewall Logging
A firewall, at its most basic form, is created to stop connections from networks or protocols not explicitly allowed by rule. The firewall inspects the source address, destination address, and the destination port and protocol of all connections to determine if this traffic matches any of its rules.
A Data Lake can aggregate information on the source address, port, destination address, and port for simplicity. As tracked by the firewall, we can view this information as an identifying attribute of any attempt to connect.
These attributes are the basis by which firewall rules are created. And it’s these rules that determine which connections are permitted and which must be denied. If the connection attributes (source, destination, port, protocol) match an existing rule, the firewall may permit access and allow the network traffic.
Firewall policies typically suffer from two significant problems for firewall managers.
- The firewall policies grow in size with each new rule access request. Often rules are added, but few rules are ever removed.
- Firewall admins write rules to allow the most access possible (not a security best practice). These overly permissive rules have unintended consequences that would enable risky network connections.
Therefore, the success of any firewall depends on the management of these policies. Firewall managers must know when and why a firewall allows and denies access and from where.
A firewall ruleset must be augmented with a successful logging feature to be most effective.
The logging documents how the firewall deals with each network connection. These logs offer insights into, for example, time, day, source and destination IP addresses, protocols, port numbers, or applications.
When and why firewall logging is useful
- Conduct firewall rule-usage analysis optimizes rules. Complete faster ruleset audits
- Find and eliminate redundant, shadowed, or overly permissive rules
- To discover potentially malicious activity occurring within your network
- If you identify repeated unsuccessful tries to access your firewall from a single IP address (or from a group of IP addresses), you may wish to investigate the origins of the network traffic
- Outgoing connections derived from internal servers, for example, web servers, may show that someone is using your system as a launchpad. They could be launching attacks against computers on other networks from your system
- Improve your network performance and overall security efficacy by optimizing or removing old, irrelevant, shadowed rule sets
Linux Firewall Logs
The Linux kernel has a packet filtering framework called Netfilter. Netfilter offers various functions and operations for packet filtering, network address translation, and port translation, which provide the functionality required to direct packets through a network and prohibit packets from reaching sensitive locations within a network. This framework lets you permit, drop, and modify the traffic in and out of a system. A tool called iptables furthers this functionality as a firewall, which you can configure using rules. Additional programs, like Fail2ban, also rely on iptables to block attackers.
How do iptables work?
Iptables is a command-line interface to the packet filtering capabilities in Netfilter. However, we won’t distinguish between iptables and Netfilter for this article. To keep things clear, we will refer to the entire concept as iptables.
The packet filtering function offered by iptables is structured as tables, targets, and chains. Put simply; a table lets you process packets in a certain way. The filter table is the default table.
Chains are connected to these tables. You can monitor traffic at different points using these chains. You can see traffic as it arrives on the network interface or before it is passed over to a process. You can also add rules to the chains to match certain packets, such as TCP packets going to port 70 and connecting them to a target. A target will determine if the packet should be permitted or blocked.
When a packet enters or exits (according to the chain), iptables compares it against the rules in these chains one at a time. When it identifies a match, it isolates the target and carries out the required action. If it doesn’t recognize a match with any of the rules, it carries out the action specified by the chain’s default policy. The default policy also acts as a target. By default, all chains have a policy of permitting packets.
Working with and interpreting iptable firewall logs
To create firewall logs, the kernel needs to be firewall logging enabled. By default, matched packets are logged as kern. Warn (priority 4) messages. You can change the log priority with the –log-level option to -j LOG.
Most of the IP packet header fields are disclosed when a packet matches a rule with the LOG target. By default, firewall log messages are written to /var/log/messages.
Windows Firewall Logs
Windows Defender Firewall (in Windows 8, Windows 7, Windows Vista, Windows Server 2012, Windows Server 2008, and Windows Server 2008 R2) is a stateful host firewall that helps secure the device by allowing you to create rules that determine which network traffic is permitted to enter the device from the network and which network traffic the device is allowed to send to the network. The firewall does not log any traffic by default. However, you can choose to configure the firewall to log permitted connections and traffic that is dropped. If you authorize Windows firewall logging, it creates “pfirewall.log” files in its directory hierarchy. You can see the Windows firewall log files via Notepad.
How to enable Windows 10 firewall logs
Go to Windows Firewall with Advanced Security. Right-click on Windows Firewall with Advanced Security and click on Properties.
The Windows Firewall with Advanced Security Properties box should appear.
You can move between Domain, Private, and Public Firewall profiles. Generally, you should configure the Domain or Private Profile. Let’s see how to create Windows Firewall logging on a Windows Firewall Private Profile. The steps below will work both for a public profile and a domain.
Click Private Profile > Logging > Customize
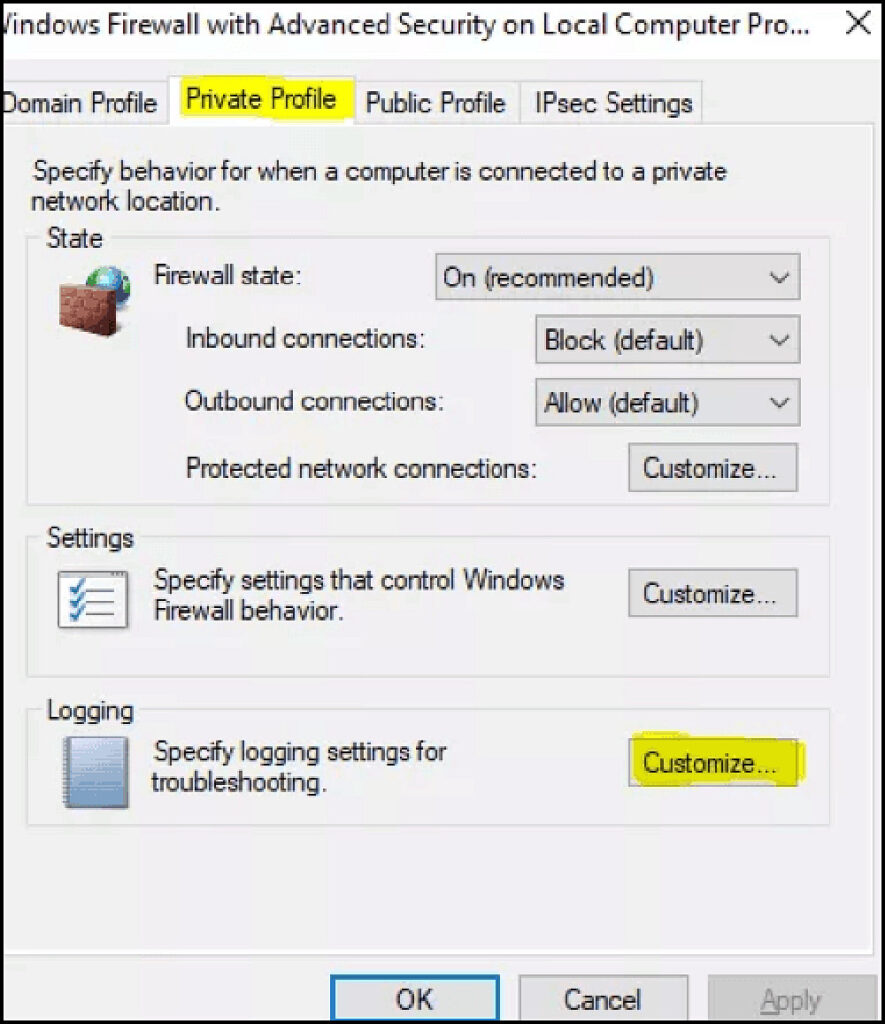
Go to “Log Dropped Packets” and switch to Yes
Generally, we turn on logging for “Log Dropped Packets” only. We won’t log successful connections as successful connections generally are not helpful when resolving problems.
Copy the default path for the log file. (%systemroot%system32LogFilesFirewallpfirewall.log) And then Press OK.
Open File Explorer and go to where the Windows Firewall log is kept. (%systemroot%system32LogFilesFirewall) . You will see, in the Firewall folder, a pfirewall.log.
Copy the pfirewall.log to your desktop. This will let you open the file with no firewall warnings.
Interpreting the windows firewall logs
Your Windows Firewall log will look like the following:
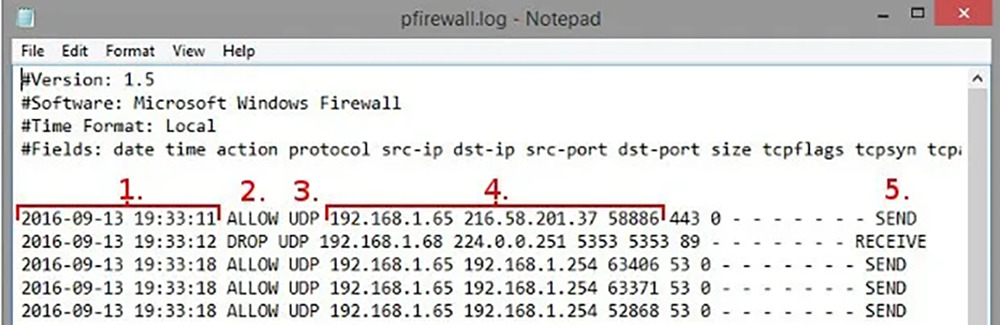
Here is an analysis of the critical aspects of the above log:
- The time and date of the connection.
- What became of the connection. “Allow” means the firewall permitted the connection, while “drop” means it has prevented it.
- The kind of connection, TCP or UDP.
- The IP of the source of the connection (your PC), the IP of the destination (your desired recipient, e.g., a webpage), and the port used on your computer. You can use this to identify any ports that need opening for software to work. You should also lookout for any suspicious connections, as they may indicate malware.
- Tells you if this connection was your computer receiving a packet of data or sending one.
How to Analyze Firewall Logs
Firewall logging, especially permitted events, can help discover potential network security threats. An organization generally places strict protection on assets that should not be freely accessible. These may include internal corporate networks and the workstations of employees. Typically, no unmediated inbound connection to these systems is allowed.
What to look for in firewall log analysis
Once you have gathered and started analyzing the logs, you can decide what to look for. You should refrain from only looking for “harmful” events. Your firewall logs not only help you isolate compromises and incidents, but they can also help you specify the normal operations of the firewall.
One way to see whether the behavior logged is suspicious is to see what the normal operations are and then to note the anomalies.
Some events should always cause suspicion and prompt further investigation. They are as follows:
- Traffic dropped
- Firewall stop/start/restart
- Firewall configuration modifications
- Administrator access granted
- Authentication failed
- Administrator session ceased
- Rule add/update
- Firewall log reset/delete
- Rule usage analysis
Log Analysis and Alerting with Exabeam
Log Management and Next Generation SIEMs
Log management is challenging, and it is becoming increasingly so with the rapid growth of network devices, microservices and cloud services, endpoints, and the vast increase in data and traffic volumes.
Next-generation Security Information and Event Management (SIEM) solutions like Exabeam Fusion SIEM can assist you with your management of security-related log events and help you learn about events relevant to a security incident.
Next-generation SIEMs:
- Security data lake, which can retain and search against unlimited data volumes of historical logs
- User and entity behavior analytics technology for improved threat detection via behavior analysis.
- Automated incident response capabilities provide service integrations via playbooks for automated investigation, containment, and mitigation of incidents.
- Advanced data exploration features can assist security analysts with their threat hunting activity.

Christopher Beier
Senior Product Marketing Manager | Exabeam | Christopher Beier is a Sr. Product Marketing Manager at Exabeam with over 25 years of experience helping clients, sales teams, and partners discover technology solutions. Prior to joining Exabeam, he was a Sr. Product Marketing Manager at Skybox Security, and before that, he worked as a Sr. Product Marketing Manager at Firemon. He graduated from the University of Oregon with a degree in Computer and Information Sciences.
More posts by Christopher BeierLearn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Exabeam Named a Leader for the Sixth Time in the 2025 Gartner® Magic Quadrant™ for Security Information and Event M...
- Show More


