Exabeam secures AI agents by applying Agent Behavior Analytics (ABA). ABA provides a centralized platform to analyze all agent activity. By collecting and correlating logs, the New-Scale Platform gives security teams visibility into AI-driven risk and powerful forensic tools to investigate suspicious behavior.
AI-DRIVEN DETECTIONS
Identify the Threats Other Tools Overlook
Go beyond legacy tools with the advanced AI in the New-Scale Security Operations Platform. It uses machine learning to build reliable behavioral baselines for users and entities, while providing deep visibility into the activity of AI agents. It correlates events, applies dynamic risk scoring, and tunes itself to prioritize credible threats—like credential misuse and insider attacks—for rapid remediation.

DETECT ANOMALOUS BEHAVIOR
Pinpoint High-risk Anomalies
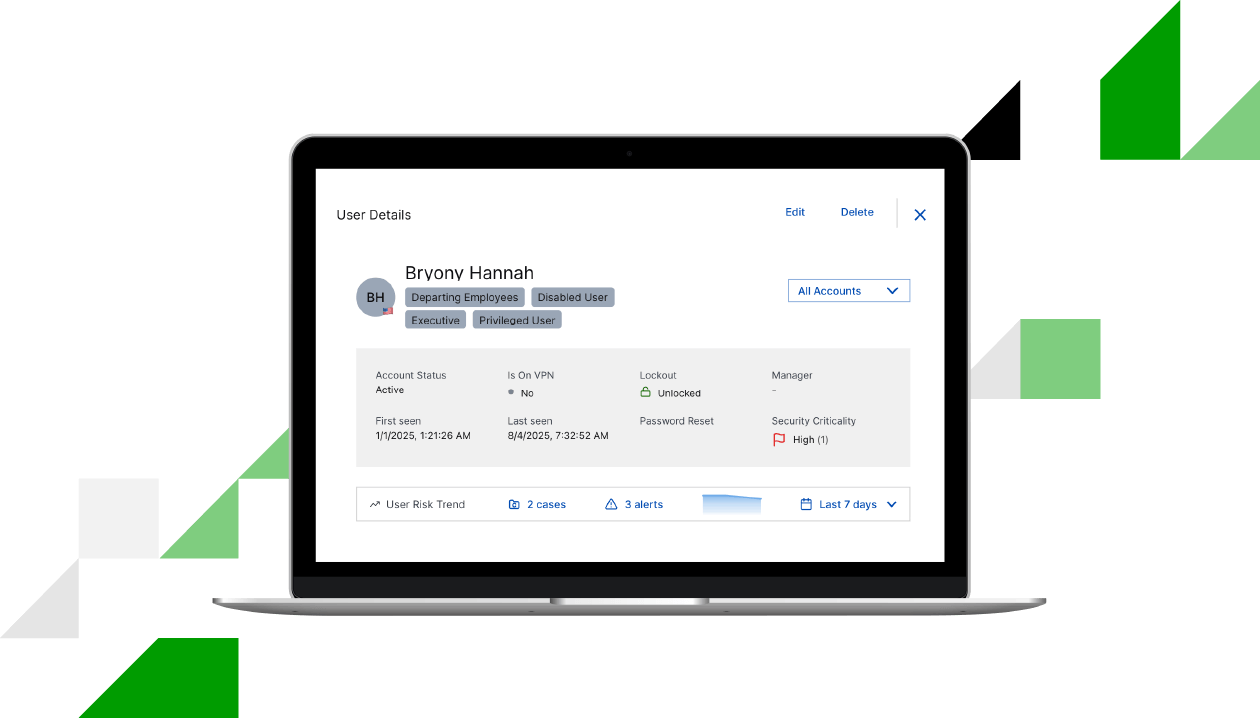
Detect attacks by identifying meaningful deviations from normal behavior. As a pioneer of user and entity behavior analytics (UEBA), Exabeam establishes accurate behavioral baselines for users and entities to flag high-risk anomalies, while comprehensive monitoring of agent identities provides clear visibility into a new category of risk.

PRIORITIZE THREATS
Focus on Credible Threats with Intelligent Prioritization
The New-Scale Platform automatically groups related detections and uses multi-layered risk scoring to surface credible threats. By factoring in event rarity and critical business context, it ensures your analysts are always focused on the highest-risk alerts and cases.

DETECT LATERAL MOVEMENT
Track the Complete Attack Progression
Trace subtle lateral movement across devices, IP addresses, credentials, and automated processes. Patented Exabeam technology reveals detailed attack chains, giving analysts a complete picture of an attack with no gaps.

STRENGTHEN DETECTION WITH CONTEXT
Gain a Comprehensive Understanding of Risk
Attack Surface Insights enriches every detection with critical entity context by automatically building complete profiles for users, devices, applications, and AI services. By mapping asset relationships and criticality, the New-Scale Platform provides essential context to make detections more precise and helps analysts instantly understand the business impact of an alert.

How can we help? Talk to an expert.
Contact UsFrequently Asked Questions
How does Exabeam detect and secure AI agents?
Can you provide more information about your generative AI guidelines and guardrails?
Exabeam ensures that inputs and outputs processed by foundation models, adapter models, and safety classifiers during prediction remain proprietary customer data. This data isn’t stored longer than necessary to generate Exabeam Nova output and is never added to Foundation Models.
How does Exabeam provide strong insider threat coverage?
Exabeam delivers complete insider threat coverage by addressing risk from every identity. For human users, our industry-leading UEBA capabilities baseline normal behavior to detect subtle deviations. For non-human identities, we provide deep monitoring of AI agents and service accounts to give you clear visibility into this new category of trusted, high-risk activity.
“Exabeam gives us an initial alarm followed immediately by context information on the alarm’s severity and timelines if more data is required. The SIEM only pushes forward with serious alerts, so we know if we need to switch into incident response mode.”
See Exabeam in Action
Request more information or request a demo of the industry’s most powerful platforms for threat detection, investigation, and response (TDIR).
Learn more:
- If self-hosted or cloud-native SIEM is right for you
- How to ingest and monitor data at cloud scale
- How monitoring and analyzing AI and automated agent behavior uncovers risky non-human activity
- How to automatically score and profile user activity
- See the complete picture using incident timelines
- Why playbooks help make the next right decision
- Support compliance mandates
Award-Winning Leaders in Security




































