In the previous post in this series, I described a user and entity behavior analytics (UEBA) event-processing journey going from raw events to eventually generating their risk scores. In this post, let’s proceed to the next layer of processing: packaging up the scored events into cases for prioritization and presentation. There are three options for doing this:
- Presenting events as is
- Organizing events into fixed units
- Dynamically organizing events into threat stories
1. Presenting events as is
One default option is to do no additional work beyond the scored events produced by the event-scoring risk engine. Those that scored above a predetermined threshold are presented as is to users. This simple scheme only works if the number of risky events presented is within the investigation budget of a security operations center (SOC) — which is most definitely never the case.
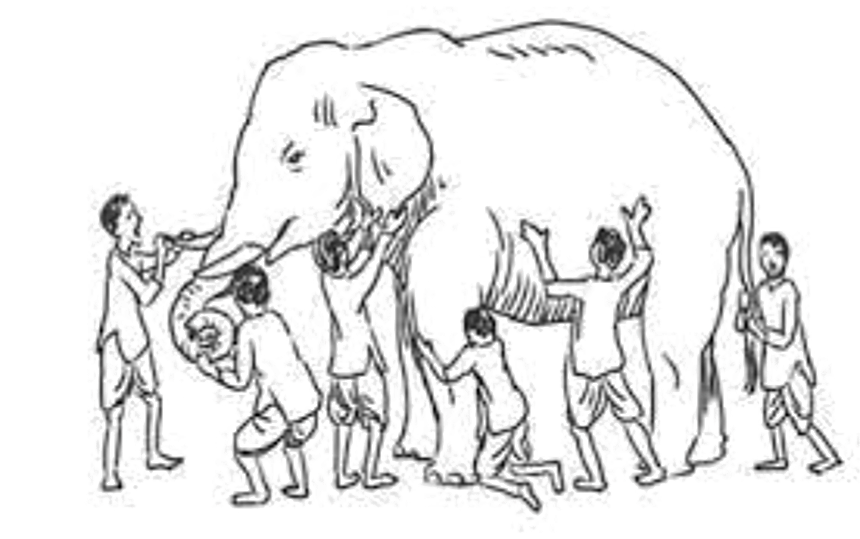
A bigger drawback is that since events are individually presented, the onus is on the user to manually discover any relationships present among events. For example, a threat from remote shell access manifests itself in a set of related anomalous events. Without linking these anomalous events together, the investigation experience could be like the Indian parable of six blind men each feeling different parts of an elephant, and all of them missing the complete picture.
2. Organizing events into fixed units
A resource-constrained SOC is overwhelmed with a high volume of anomalous events every day. It is impractical to present these events to analysts as they are. These events must first be grouped into higher-level summaries for presentation. A common event summarization approach is organizing events into per-user and per-day groups, or sessions. As the first order approximation, this is a reasonable idea, as anomalous events from a user on a day are generally related to one another. Sessions can be scored based on the simple sum of event scores. Prioritized by their scores, sessions are typically presented to analysts as investigation cases.
One can see that there are alternatives in the grouping logic: for example, grouping anomalous events per different types of entities, e.g., assets, files, geo locations, or security groups; or grouping events per different windows, e.g., per hour or per week. The choices depend on the use cases.
While grouping schemes like those above are helpful, they leave much to be desired. For one thing, a threat is not always confined in a rigid boundary defined by a single user or entity over a fixed time period. In fact, a malicious insider can switch accounts, hop from machine to machine, and do their deeds within hours or months. In addition, a mere collection of anomalous events, however they are grouped, doesn’t readily tell a story. The burden is still on users to manually examine them for insight.
3. Dynamically organizing events into threat stories
A more dynamic way of organizing anomalous events that are linked across users, assets, and time is needed, along with a way of doing so with a high degree of explainability and a threat-centric focus. Anomalous events should be organized into a story — one that is based on the MITRE ATT&CK® framework. A story consists of a path of time-ordered anomalous events with labeled attack stages that move from left to right across the ATT&CK tactic columns, e.g., from Initial Access to Data Exfiltration. Finally, these stories must come with scores as well, to allow for prioritization. This form of UEBA outcome, that comes with readily actionable insight, is infinitely more valuable than the above alternatives. This is the vision — the holy grail — of UEBA.
This is accomplished by employing a graph streaming algorithm that processes each arriving anomalous event freshly out of the risk engine to update graphs consisting of nodes of historical events. The real-time update first links disparate events using logic defined by security domain knowledge, then searches for the best paths over the graph in ways that conform to the ATT&CK tactic movement ordering. These dynamically updated paths of events are presented to the user for review. The criticality of a path can simply be the sum of events scores along the path, unless otherwise dictated by business policies. In this way, analysts are provided with machine-automated insights based on the ATT&CK tactic phases. Further details will be discussed in a future post.
Conclusion
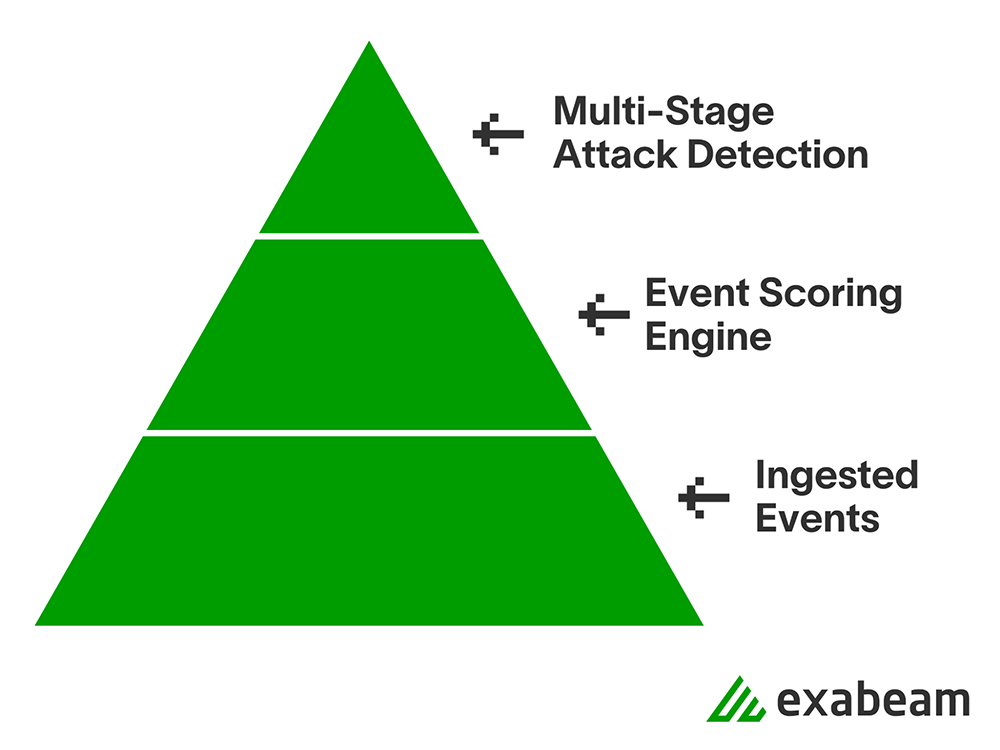
Making sense and mining for insights from security and network logs is a sifting process. Starting from the terabytes of raw events, a risk engine outputs anomalous events in many orders of magnitude less. These anomalous events are then further processed and organized into just a handful of potential multi-stage attack stories. Security knowledge, machine learning, and algorithms supported by a matching cloud-native infrastructure are what make a complete, end-to-end UEBA experience possible.
Want to learn more about UEBA?
Get The Ultimate Guide to Behavioral Analytics
This comprehensive guide was created to help organizations evaluating UEBA solutions better understand it and how it can be adopted to improve your overall security posture with faster, easier, and more accurate threat detection, investigation, and response (TDIR).
Read this eBook to gain clarity on confusion about the growing UEBA market, and learn about:
- What UEBA is and why it is needed
- How UEBA is different from other security tools
- The different types of UEBA solutions
- Factors to consider when evaluating UEBA solutions
- Threat-centric use cases

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!