The New Breed of “Fileless Malware” and How It Can Be Stopped with Behavioral Analytics and Machine Learning

A new genus of malware has emerged that breaks the rules of traditional detection and defense methods. Unlike other breeds of malware that require the installation of software on a victim’s machine, fileless malware infects a host computer’s dynamic memory, or RAM. Fileless malware attacks can also hijack Windows, essentially turning the power of the OS against its own users by using common tools like PowerShell (which is integrated into Windows 8) for its malicious activities.
What are the steps of a fileless malware attack?
Beginning with a phishing email, a visit to a malicious website, or the use of an infected USB flash memory stick, fileless malware scans the machine looking for vulnerabilities—whether it’s unpatched Flash or a Java plug-in, or almost any process that involves PowerShell.
Malicious websites may also download Flash or Java onto a user’s machine. The payload then begins executing the attack by using the dynamic memory of the user’s computer, such as leveraging browser processes. (See Figure 1 for more information on the steps of an attack.)
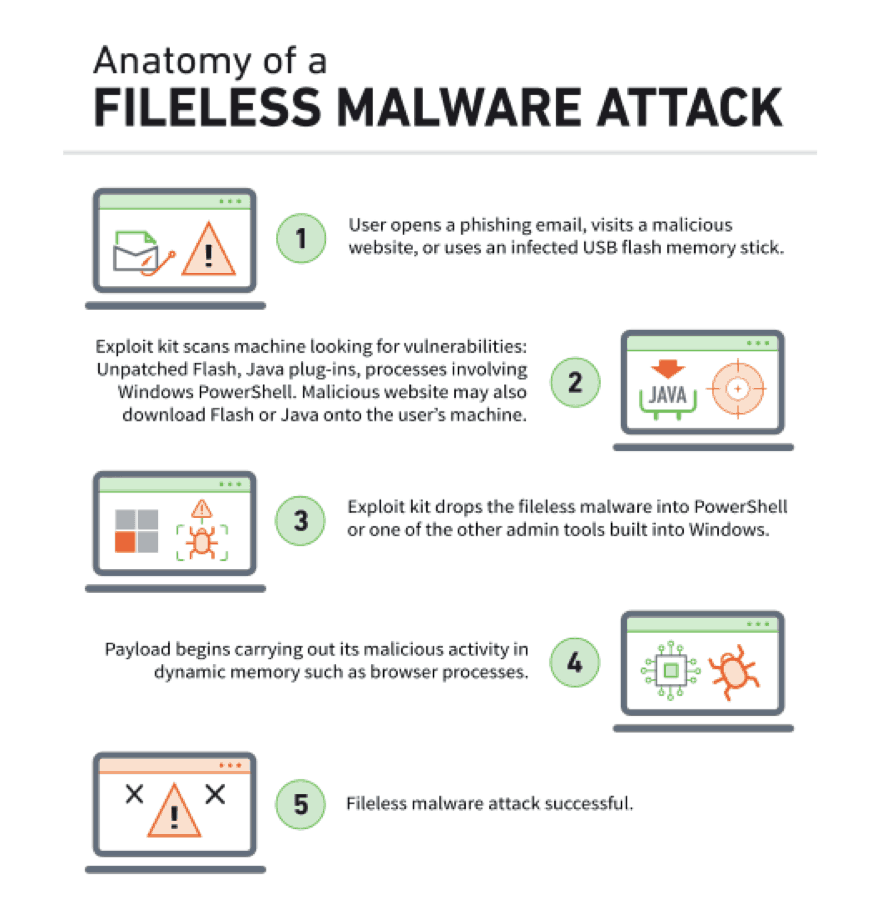
Figure 1- The steps of a fileless malware attack
The growth of fileless attacks
According to research by the Ponemon Institute, fileless malware attacks accounted for about 35 percent of all cyberattacks in 2018, and they are almost 10 times more likely to succeed than file-based attacks.
Although fileless malware doesn’t yet have the notoriety of ransomware and other attack vectors, fileless attacks nevertheless can pose a major threat—and they’re evolving, according to a 2017 report by Malwarebytes.
A Ponemon Institute data breach report cites that fileless malware attacks account for about 35 percent of all attacks in 2018, and they’re almost ten times more likely to succeed than file-based attacks.
Threats entering your network undetected
What lets these attacks fly under the radar is that they don’t write to your disk. Instead, the malware lurks in memory using hiding places such as PowerShell (widely used by system administrators to automate tasks), Visual Basic (VB) scripts, and Windows Management Instrumentation (WMI).
This makes fileless attacks very difficult to detect since typical anti-malware programs only scan for malicious files, which are then flagged for removal. But that strategy fails when there’s no file on a system. Lack of cookie crumbs (aka remnant code) also makes it tough for security teams to analyze the malware behavior later.
In addition, bad actors are equipping fileless malware with new abilities. These not only enable such attacks to evade detection, but their payloads can also deliver advanced infections. One concern for enterprises is that fileless attacks are “borrowing the propagation and anti-forensic techniques seen in the complex nation-state attacks.”
Powerful payloads and persistence
Persistence is one area where such added tactics, techniques, and procedures (TTP) are having a greater impact. With potentially many months needed to remediate an attack, imagine how much critical data an attacker could drain from your network during that time.
In one case, hackers used an obfuscated PowerShell infrastructure to drop fileless malware on targeted computers, which in turn fetched payloads from a command-and-control server. This created a very effective advanced persistent threat (APT) that allowed the attackers to operate undetected for half a year, with data being exfiltrated all the while. And because a trusted program executed the commands, security staff and the tools they used all assumed the commands were legitimate.
One roadblock to their persistence is that fileless malware lives in dynamic memory. In theory, regular system reboots should flush it. But today’s craftier cybercriminals have even devised ways for their code to linger after a reboot.
Cutting-edge tools to fight a cutting-edge threat
Since this new breed of malware can evade traditional detection tools and techniques, it’s critical to look beyond signatures, prewritten rules, disk scanning, and the like. Instead, what if you could track the activity of those having administrator and super user privileges to detect anomalous behavior? (Remember these account credentials are just as susceptible to being hacked.)
Perhaps one such user uncharacteristically accesses different databases or systems in sensitive areas such as HR or finance. That could be an indicator of compromise (IoC). By automatically and swiftly alerting your incident response (IR) team, you could remediate the threat before the damage has been done.
User and entity behavior analytics for fileless malware threat detection
Rather than looking for malicious files, detecting anomalous behaviors or entities can indicate the presence of malware. User and entity behavior analytics (UEBA offers the best solution. Unlike conventional security monitoring tools that scan disks and use signatures or rules—which is useless in detecting fileless malware—behavioral modeling and machine learning offer the best opportunity to identify anomalous and suspicious user and entity behaviors.
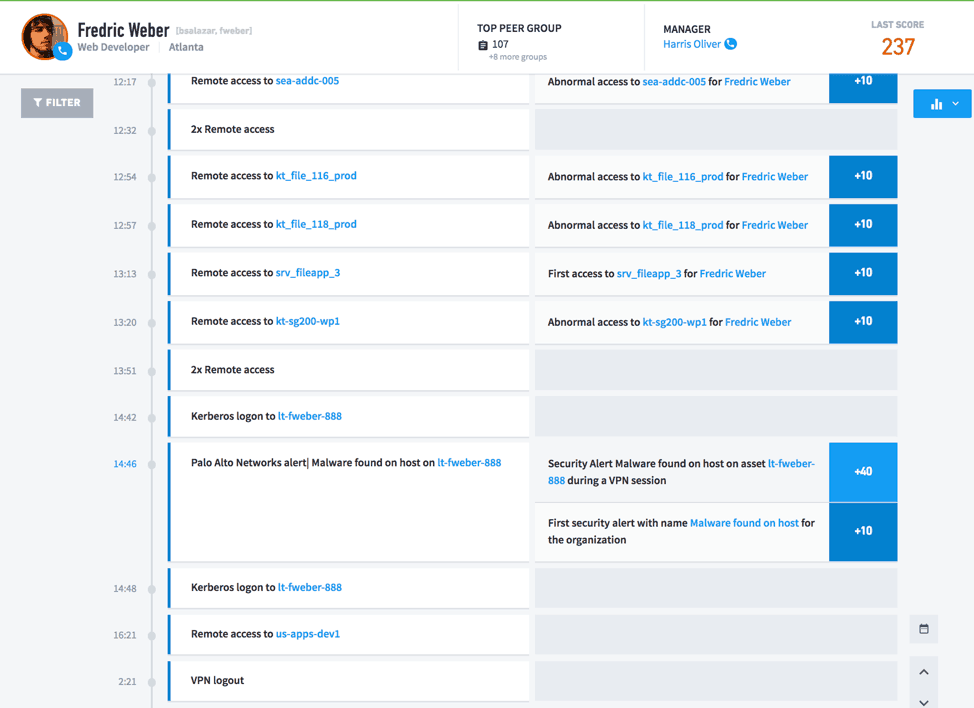
Figure 2: An Exabeam Advanced Analytics, User Incident Timeline, showing anomalous and abnormal behaviors stitched together to find a threat
UEBA can monitor user activity as well as the behavior of applications and services. This includes inter-process communications, unauthorized requests to run applications, changes made to credentials or permission levels, and other uncharacteristic behavior. UEBA’s automated, around-the-clock monitoring can alert your security team of a fileless malware attack.
Learn more on how behavioral modeling and machine learning can stop the damage of fileless malware attacks, using Exabeam’s Advanced Analytics.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












