Compliance
Always-on compliance makes adherence simple.
Trusted by organizations
around the world





















Security that works
Many organizations use manual processes and disparate security products to meet regulatory requirements, like General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS) and Sarbanes-Oxley (SOX).
These ad hoc processes leave organizations at risk for audit failure, fines, and disclosure reporting. Exabeam provides detection rules, models, and compliance reports that show auditors security controls are in place and work as designed.
- GDPR
- PCI DSS
- SOX
Ensure your organization meets GDPR requirements while protecting individual privacy.
The goal of GDPR is to protect the personal data of European Union (EU) citizens. GDPR applies to any company doing business with an EU organization or an individual. Non-compliance could result in stiff fines, up to 4% of the organization’s worldwide annual revenue.
AUTOMATE AND SIMPLIFY GDPR COMPLIANCE WITH EXABEAM:
Identify new and emerging external threats
GDPR mandates that organizations keep up with evolving threats by employing state-of-the-art technologies capable of scaling with the problem (articles 25 and 32).
Exabeam pre-packaged detection models free analysts from writing and updating correlation rules to identify evolving threats.
Exabeam behavioral analytics baselines normal behavior of all users and entities and, if any user or entity drifts away from normal, they are instantly flagged and assigned a risk score. Exabeam then gathers all related events into a cohesive timeline. As a result, analysts can see new and emerging threats with ease.
Mitigate internal threats
Threats originating from inside the organization are the most difficult to detect. GDPR directs organizations to carefully consider the risk of unauthorized access, alteration, destruction, or exfiltration of personal data at every stage of handling (Article 24).
Identity and network access controls help organizations create a system protection framework, but fail to account for the ways insiders accidentally or maliciously threaten the organization. Exabeam can gather logs from over 500 productivity and security applications and map activity to individuals, using analytics to fill in missing log fields. Using behavioral analysis, Exabeam then baselines normal user activity against which it can alert on abnormalities and deviations. Whether it’s a privilege escalation, or a related data exfiltration event, threats are readily identified.
Use pre-defined compliance reports
To achieve GDPR compliance, organizations need to demonstrate that they monitor critical infrastructure holding the personal data of EU citizens.
Using a powerful compliance and forensics reporting engine, Exabeam generates a series of built-in, GDPR-specific reports, that help reduce the time to show compliance to auditors.
Protect employee Personally Identifiable Information (PII)
Protecting employee PII from unwarranted access is a critical GDPR requirement.
Exabeam provides role-based access control (RBAC) to enforce PII data masking. With Exabeam, risky actions representing potential security incidents are surfaced to analysts. User information can remain masked until a credible risk has been identified and the incident is forwarded to data privacy officers (DPOs) for de-masking. Individual privacy is therefore maintained.
Reduce breach response time, minimize data exposure
GDPR requires breach notification within 72 hours, but most organizations struggle to know when one has occurred. Using traditional tools such as a legacy SIEM, it could take days, weeks, or even months to detect a breach, let alone understand its complete scope and data exposure.
With Exabeam, it is easy for analysts to detect an incident and see the attack scope. By applying behavior-based risk scoring to all users and devices, Exabeam reduces noise from false positives and keeps analysts focused on actual incidents. Exabeam Smart Timelines supercharge detection, investigation, and response processes by automatically collecting all investigation artifacts in a single cohesive timeline.
Secure credit card data and accelerate PCI DSS compliance.
PCI DSS promotes cardholder data security while facilitating broad, global adoption of consistent data security measures. PCI compliance is a must for any organization handling credit card data, and failure to comply can result in daily penalties and fines.
AUTOMATE AND SIMPLIFY PCI DSS COMPLIANCE WITH EXABEAM:
Comprehensive compliance logging
Monitoring and analyzing events, as well as maintaining continuous visibility are crucial components of PCI-DSS.
Use pre-defined PCI-DSS compliance reports, such as “Failed VPN Logins” and “Remote Session Timeouts,” making it easy to show compliance to auditors. Exabeam Cloud Archive retains up to ten years of online searchable data meeting retention requirements for internal compliance stakeholders and external auditors.
Automated, fast threat detection using behavioral analysis
Ensuring rapid threat detection is a key PCI-DSS requirement. PCI-DSS also emphasizes continuous account monitoring—especially for privileged users and third-party vendors with special access. However, if legitimate users’ credentials are used by an attacker, most organizations’ security controls will not detect.
Exabeam continuously baselines the normal behavior of all users and entities on the network using behavioral analytics. Any deviations from normal behavior are instantly flagged and assigned a risk score. All activity is also automatically organized into timelines that provide context for security teams to investigate and take decisive action. As a result, analysts can detect insider threats, compromised accounts, data loss, and other advanced threats.
Enhance PCI scope reduction efforts to save money
Most organizations limit PCI scope to lower the cost of the PCI-DSS assessment; to lower the cost and difficulty of implementing and maintaining PCI-DSS controls, and to reduce the likelihood of non-compliance.
Exabeam provides hundreds of pre-built detection models to immediately flag PCI scope violations and save your organization from surprises during PCI audit time.
Effective, automated incident response
Another PCI-DSS tenet is to quickly and effectively respond to any incident.
Exabeam Smart Timelines are created for every user and every device, every day automatically. Smart Timelines provide a chronological list of all activities—normal and abnormal—so analysts can see an entire attack, not just pieces of it. With a clear understanding of the scope of the attack, analysts can use pre-defined response actions and playbooks, or create their own to orchestrate and automate remediation.
Enforce internal controls and reporting requirements necessary to meet SOX compliance.
SOX regulation aims to protect shareholders and the general public from accounting errors and fraudulent corporate practices, to improve the accuracy of corporate disclosures.
AUTOMATE AND SIMPLIFY SOX COMPLIANCE WITH EXABEAM:
Monitor security events, including sensitive file access
Businesses operate in distributed environments leveraging internal and external infrastructure. To gain visibility across these domains and monitor them for SOX compliance, logs must be collected from all of these operating environments.
Exabeam gives security teams the edge they need to quickly and accurately identify risky activity related to financial reporting no matter where it occurs. Exabeam ingests log data across disparate domains (e.g., cloud, database, email, application) and assembles it into a coherent activity chain to improve analyst visibility. Regarding the detection of data tampering specifically, Exabeam has built-in file monitoring models that track every file-related action—including initial access, attaching data to an email, downloading, or even writing to a USB drive.
Detect compromised credentials
Ensuring only authorized personnel access sensitive data is a fundamental requirement for financial systems. The only way to meet this requirement is to understand all users’ and entities ’ “normal” behavior.
Exabeam models users and entities to determine their normal behavior and then notifies analysts when any suspicious activity —including activity by users with valid credentials -occurs. Exabeam provides actionable insights about alerts from other security solutions, giving analysts the context to take quick, decisive action.
Enable rapid investigation
SOX Section 302 requires organizations to implement systems that protect against data tampering, track timelines, and evaluate the who-what-where-when of data access. For insider threats—especially those involving lateral movement—it may be difficult and time-consuming, if not impossible, to create accurate incident timelines.
Exabeam user and entity behavior analytics identify risky activities, then automatically creates timelines so analysts can investigate them. Automating parts of the investigation removes pressure on limited human resources and help analysts efficiently fulfill the Section 302 requirement.
Effective incident response
Prevention is a core tenet of SOX, and has historically been the security teams’ focal point. But attacks do occur, and incident response must be effective.
Exabeam Smart Timelines are timelines that are created for every user and every device, every day automatically. Smart Timelines uniquely provide a chronological list of all activity—normal and abnormal—so analysts can see an entire attack, not just pieces of it. With a clear understanding of the scope of the attack, analysts can then use pre-defined response actions and playbooks, or create their own to orchestrate and automate remediation.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
pre-built compliance dashboards
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool.
reduction in investigation times
Build repeatable workflows to semi- or fully-automate your response activity. 1
1 The combined reduction organizations achieved in a recent study.
Explore the many ways Exabeam can work for you
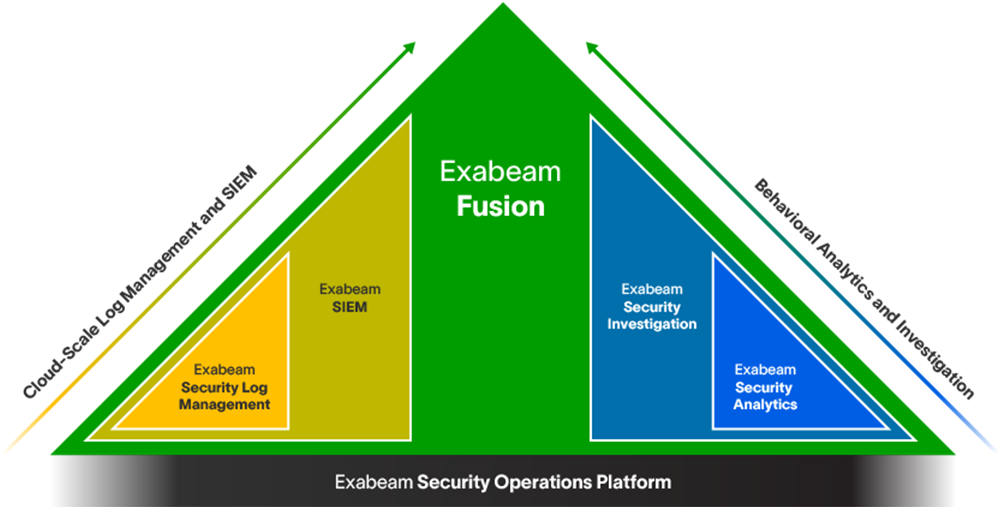
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, automation, and TDIR content on top, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- Get started: Exabeam Security Log Management
- SIEM replacement: Exabeam SIEM and Exabeam Fusion
- SIEM augmentation: Exabeam Security Analytics and Exabeam Security Investigation
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

WHITE PAPER
Adhering to GDPR Security Controls with Exabeam
Learn how Exabeam helps organizations better monitor access of personal data and ensure alignment with the European General Data Protection Regulation.

BLOG POST
SOX Compliance: Requirements and Checklist
Understanding the requirements of the regulation is only half the battle when it comes to SOX compliance. To achieve compliance effectively, you will need the right technology stack in place.

WHITE PAPER
Implementing PCI DSS 3.2 Controls with Exabeam
Learn how Exabeam can be used to help companies meet various security controls detailed within PCI-DSS.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision






