Ransomware remains just as prolific now as it has over the past several years because for attackers it is the gift that keeps on giving. The cost is no longer just a few thousand dollars in the desperate hope of getting your data back. Let’s take a deeper look at some of the most recent attacks on Toll, TNT Express, Maersk and Pitney Bowes and the financial numbers around them.
Although we think of ransomware as being a relatively new threat in the world of information technology and cybercrime, its origins actually date back to 1989 when Harvard-educated biologist, Joseph L. Popp sent 20,000 compromised diskettes to attendees at an internal AIDS conference organized by the World Health Organization. Victims were asked to pay $189 to recover their files. It was 2013 when ransomware started to be more widely known with Cryptolocker and its many variants grabbing worldwide coverage as organizations were locked out of data and forced to either pay the ransom or invoke their cyber resiliency and business continuity plans. Many discovered the latter didn’t work. Against advice from law enforcement and government agencies such as the Federal Bureau of Investigation (FBI), some organizations paid the ransom in the hope of recovering their data and keeping a low profile from the press and public. Often mixed results ensued where ransoms were paid and the organization never heard anything again.
An unfortunate fallout for the rest of the world was that the more the ransoms got paid, the more prolific the problem became. Ransomware creators quickly developed their own ransomware-as-a-service model providing the malicious software for free and the business model paid dividends as they were taking a cut of any fee paid.
The bad guys got greedy and where originally a ransom of a few thousand dollars was the norm, it is now not uncommon for large targeted organizations to be asked for several millions of dollars to regain access to their data.
Download > THREAT RESEARCH REPORT THE ANATOMY OF A RANSOMWARE ATTACK
Recent costly ransomware examples
Only last week one of Australia’s largest logistics companies, Toll was subject to a ransomware attack from a new variant called Mailto (aka Kazkavkovkiz, Kokoklok and NetWalker). Mailto targeted systems which resulted in both internal and customer-facing tracking systems shutting down. While the ransom demand amount is unknown we already have some insights into the potential costs involved in the restoration of services, company stock values and reputation related losses from similar attacks.
Fellow logistics company TNT Express, part of the FedEx group reported the cost of a Petya malware attack at an estimated $300 million and Danish shipping company Maersk was impacted to the value of $200-300 million in a similar attack.
Finally, Pitney Bowes reported fourth-quarter earnings decreased by $19 million or 3 percent year over year due in part to a ransomware breach in October 2019 that affected its global e-commerce business, presort mailing-services division and its sending-technology group for shipping and mailing.
Stuck between a rock and a hard place
Organizations that have fallen victim to a ransomware attack have many difficult decisions to make and very little time to make them: Do we pay the ransom? Do we try and restore from backup? Do we need to notify this as a breach? For example, under the General Data Protection Regulation (GDPR) an organization that fails to report a breach could be fined up to 4% of the global turnover. On top of that there may be demands from the bad guys, Travelex, for example, was hit last month with a ransomware attack and asked to pay $6 million within two days or face double the payment.
It doesn’t just stop there though. An organization that may have been valued at billions of dollars, now hit by a ransomware attack impacting customers globally sends shockwaves through the investors. Now suddenly that organization is valued at only a few hundred million dollars, public confidence is rocked and revenue is down.
Attack vectors and how the infections occur
94% of all malware including ransomware is delivered by email*
71% of breaches are financially motivated*
*Source: Verizon 2019 Data Breach Investigation Report
What can you do to help detect and prevent ransomware?
Email gateways and email systems do a reasonable job of blocking spam, detecting known malware and performing reputational lookups of senders, but the delivery methods for ransomware by email can change by the hour, if not by the minute. Simply put it is very hard for these systems to catch every potential ransomware email passing through.
Equally some legacy security and incident event management (SIEM) tools also have difficulty in detecting ransomware for the following reasons:
- Reliance on static correlation rules looking for specifics such as subject lines
- No or out-of-date threat intelligence feeds
- Lack of additional user context
- Poor data source quality or bad parsing
- No data or user analytics
Gathering indicators of compromise (IOCs) shown in the examples below for Mailto can prove useful as an additional context in SIEM rules. However, this means we are reliant on the ransomware actually being executed. We ideally want to detect and minimize the risk of that happening as these IOCs can change frequently.
Mailto IOCs
Hash: 416556c9f085ae56e13f32d7c8c99f03efc6974b2897070f46ef5f9736443e8e
Associated files: {ID}-Readme.txt
Mailto email addresses: sevenoneone[@]cock.li, kavariusing[@]tutanota.com (other similar addresses for the same domains have been seen)
Ransom Note Text:
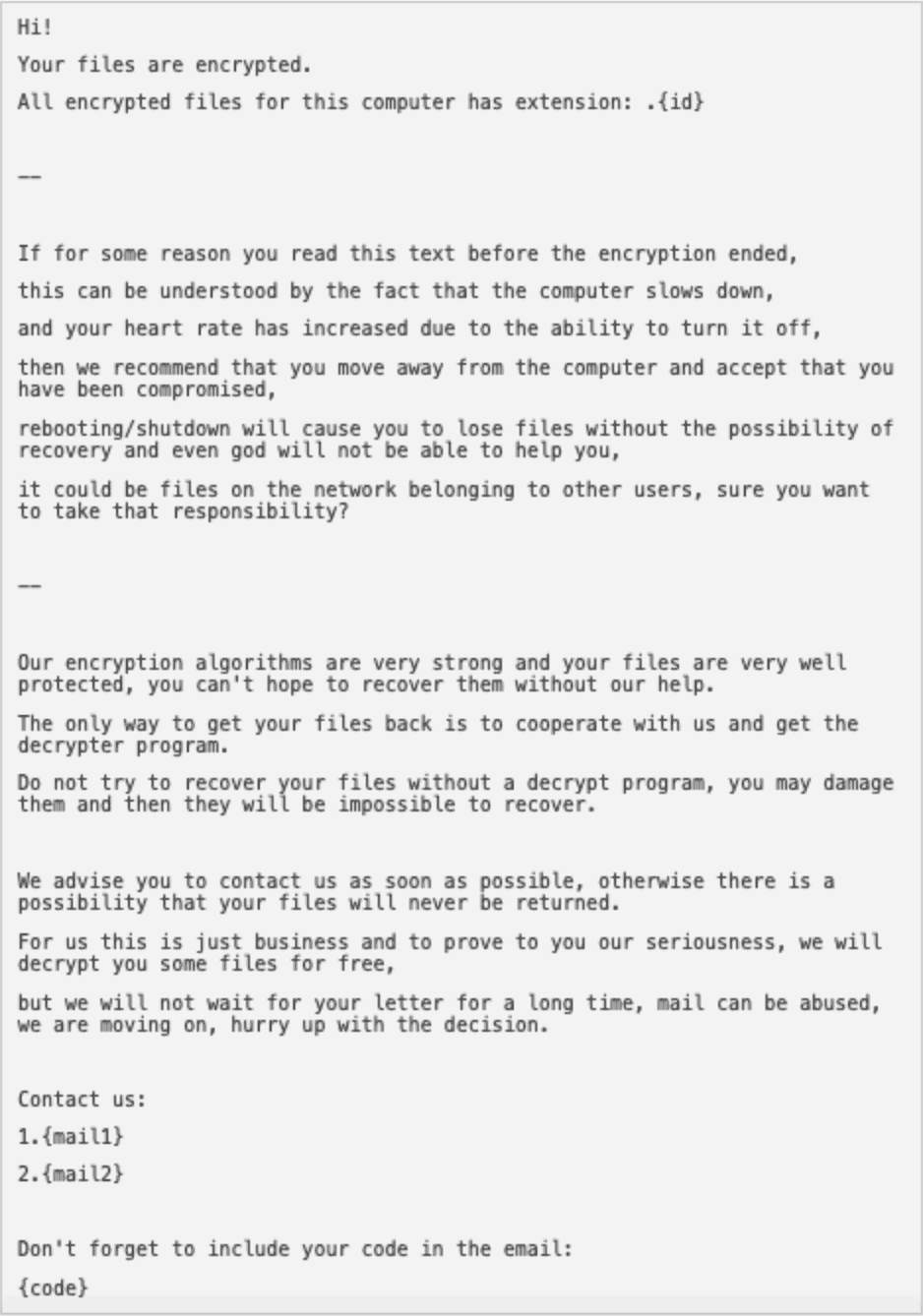
A ransom note associated with the Mailto ransomware with instructions on how to contact the sender.
In a previous role, I was part of a team building out a managed security services provider (MSSP) security operations center (SOC). We were working on detecting ransomware by carefully crafting some static correlation rules with a little bit of Regular Expression (RegEx) to detect more common ransomware campaigns targeting courier delivery companies and utility companies by subject line content. One morning a ransomware campaign was targeting a particular Australian state with a new payload variant, but with similar delivery mechanisms. I was sitting in front of the SIEM when the alert triggered at around 7:00 a.m. I was able to validate the alert and abstract a list of affected users and send the list to our customers who were then able to delete all affected emails within 30 minutes or so. Almost in parallel, another organization in the same state got targeted with the same campaign though their first point of alert was from one of their security vendors who sent out a blanket advisory email at 10:00 a.m. by the time this customer (who didn’t have a SIEM) had searched for all affected users and deleted all the emails it was about 4:00 p.m.
This is a good example of SIEM vs no SIEM. From alert to end of triage was 45 minutes for me and for the other organization it was 9 hours, that’s 8 hours and 15 minutes greater threat exposure time.
Let’s take that a step further.
Since the incident above was almost four years ago, the bad guys have gotten smarter with the way they deploy ransomware. There is less emphasis on large ‘target everyone’ campaigns and much more emphasis on selected targeting. This means some of those original easy to pick up points like the subject line which might have originally told me the postal service was holding a failed delivery are no longer reliable methods of detection. To try to get ahead of the game (or at the very least keep up with) an organization needs a modern SIEM with behavioral analytics capabilities such as Exabeam Advanced Analytics.
We can no longer rely on static correlation rules to detect malicious emails, we need behavioral analytics to tell us something abnormal is going on. For example, our user has received an email from a domain he or she has never seen before or it has an attachment that the organization hasn’t seen before. As the bad guys get smarter, so must our detection capabilities. If a suspicious email does get through and trigger an alert, as an analyst I don’t want to spend critical time building a picture of what has happened. With the help of the Smart Timeline feature in Advanced Analytics within seconds it allows security analysts to quickly review all activity for a user leading up to the delivery of an email through to any actions the user may have taken afterward whether they are deemed anomalous or not.
Equally important as detecting potential ransomware quickly is the ability to triage and remediate. When Advanced Analytics is coupled with Incident Responder, security analysts have the power to automate the triage and response process with a few clicks. These actions include performing analysis of any attached files or links using reputation lookups, detonating attached files in a sandbox and the ability to reach into applications like Microsoft Office365 or Exchange and delete all identified ransomware emails received. These capabilities reduce the time to triage to a few minutes from what would have taken upwards of 30 minutes and for ransomware emails that do reach a user’s mailbox, limiting the risk exposure time is absolutely critical.
Prepare for the worst: develop your business continuity plan (BCP)
An organization must review its current policies around IT security and the following guidance may just save your bacon! Here are five things you can do immediately.
- Review file and folder permissions on anything that a user has access to, whether that’s local endpoints, network drives and shares through to database access. All access permissions must be controlled and, please, do not give everyone read/write rights.
- Design your network so that any critical areas to business data or applications can be isolated in a way to minimize malicious traversal and maintain business continuity.
- Backup your data, validate it and ensure it is kept somewhere on the network where it cannot be maliciously encrypted, deleted or accessed. On the flip side it must also be readily available to facilitate a quick restore.
- If you must restore data, be 110 percent certain the source of malware or infection is removed.
- Create the above items as part of your BCP–and test it! Don’t leave the testing to the day you need that data restored
Remember ransomware is no longer just about encrypting your data on site. The latest ransomware can scrape your data and upload it to an unknown location and entity. Ensure you have controls to prevent and/or detect this with the ability to stop data exfiltration in its tracks. Think cloud access security brokers and data loss prevention.
Technology and security training
Of course, technology plays a major part in your first line of defense and detection but ultimately if ransomware and malicious emails do get through to the user, your organization is then reliant on the user not to open the email, the attachment or click on the link. Having a robust user awareness program to teach users the perils of opening unfamiliar emails on how to identify classic signs of malicious emails such as grammar, attachments and embedded links is critical in protecting an organization.
User awareness programs should have their own budget, be instilled in new employees as part of the onboarding process and something that is implemented, tested and reviewed at least four times a year.
Next Steps
Sign up for a demo to see how the Exabeam solutions combat the ransomware threat to your organization.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













