Problem
When was the last time your car’s “idiot light” came on? Did you know what to do?
Think about the last time you went to take your car to the mechanic. It probably wasn’t immediately obvious to you why the check engine light came on, or where that strange noise under the hood was coming from. But the first thing your automotive technician probably did was plug in an onboard diagnostics (OBD) to gain more information about the problem.
The term “idiot light” in part originated from frustrations in the automotive industry around the transition from more detailed sensors and gauges in a vehicle to simple indicator warnings. An alert only turned on when a fault had already occurred, without any context or guidance on what the vehicle owner should do next.
The same problem holds true in the world of security; SIEMs light up all the time with hundreds of alerts, each and every day. At Exabeam, if an attacker makes their way in the network, we sometimes use the saying that their abnormal behavior “lights up like a christmas tree”. Yet even when our behavior analytics found abnormal activity to provide an early warning of an attack in progress, we still fell short of providing analysts a means to quickly understand how to address the incident.
Introducing: Automated Incident Diagnosis
With Automated Incident Diagnosis, Exabeam analyzes abnormal behavior to automatically diagnose the type of threat associated with an incident and classifies it by use case. Prescriptive checklists immediately appear at the bottom of the case for analysts to easily access and follow investigation, containment and remediation steps specific to the identified use case. Incidents are also further automatically enriched with MITRE labels, user context, past anomalous activity and key evidence.
This new feature enables security teams to help their analysts be more efficient and achieve faster time to resolution using automation and standardization. Automatic classification and enrichment surface key details for analysts to understand the scope of an incident (“what is happening?”), while prescriptive checklists guide analysts (“how should I approach this incident?”).
How it works
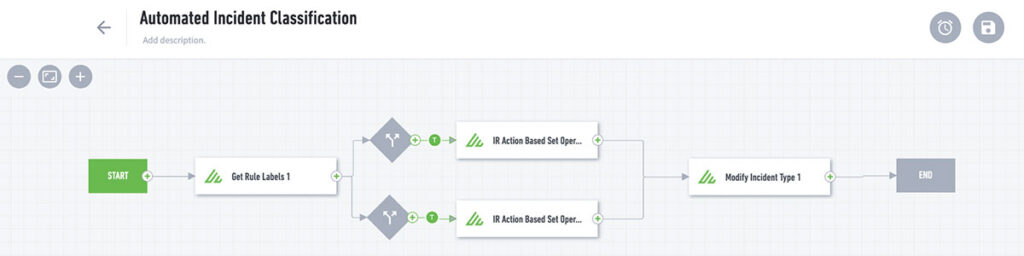
Step 1: Incident classification
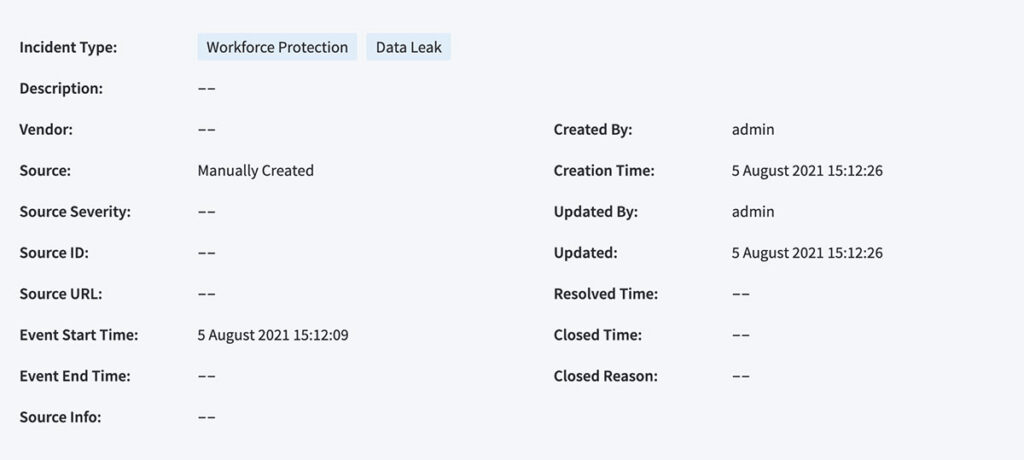
Exabeam Incident Responder analyzes the rules and models triggered by a user’s abnormal activity and maps it back to a specific use case. This feature runs whenever a notable incident is generated and automatically adds a tag to the top of the incident indicating the use case under the “Incident Type”.
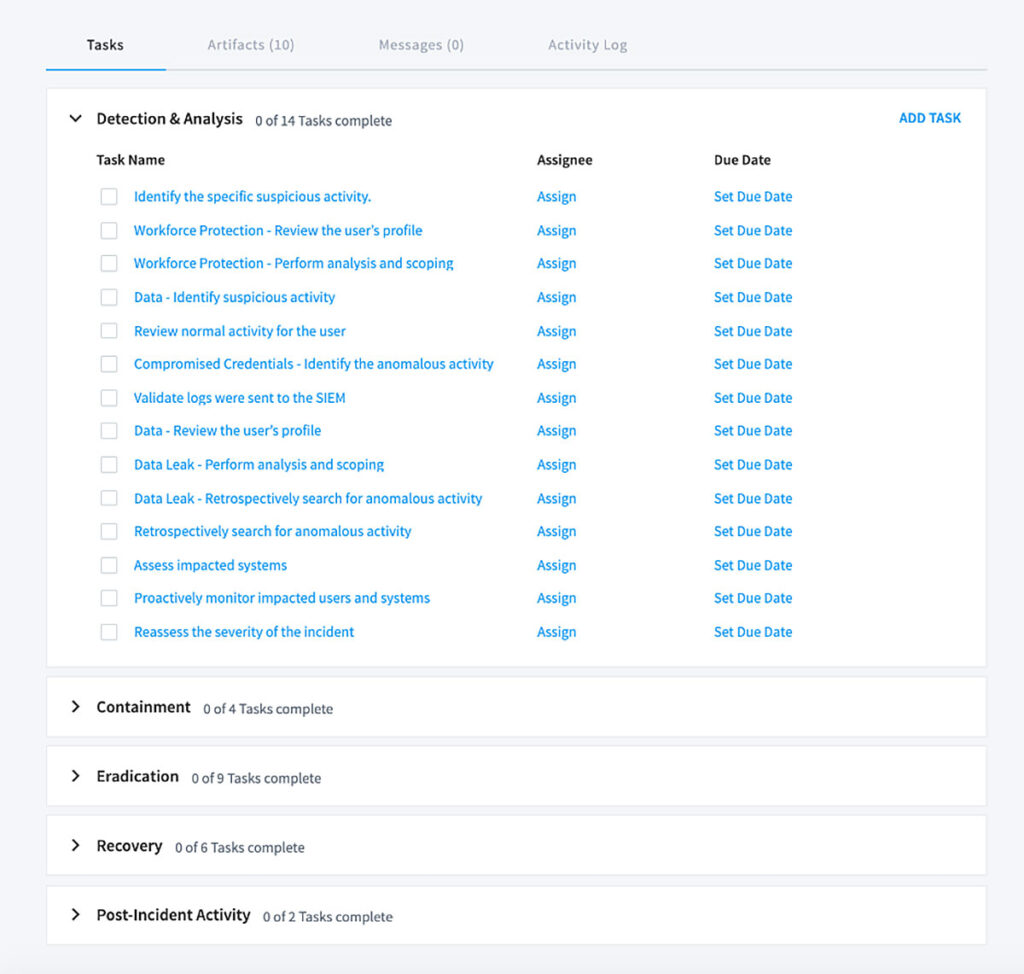
Step 2: Prescriptive checklists
Leveraging decades of security practitioner experience from our own sales engineers and experts, we’ve developed 20 distinct checklists for each Exabeam use case. By following a checklist, SOCs can ensure their teams are adopting best practices while standardizing their approach to similar incidents by use case. These guide analysts to answer key investigation questions, such as “Has the user switched accounts, or accessed this system before? Have they accessed any malicious files or domains? What role do they have or which department do they belong to?” Checklists may be further modified for your organization’s specific needs.
Step 3: Incident enrichment
Next, this feature gathers contextual information for an incident. Previously, analysts working on a “notable” incident sometimes needed to manually pivot back to a user’s timeline to obtain details like MITRE TTPs associated with an incident, a user’s role or department, previous abnormal activity, or related incidents for the same user. Now this feature extracts key evidence to automatically append to an incident, such as IP addresses or URLs that can be used for further automated response actions, such as obtaining the domain reputation through a third party threat intelligence service. Automatically enriching an incident helps make an analyst more efficient by embedding key details directly in a case, right at their fingertips.
Conclusion
Security analysts are knowledge workers. Despite hours spent triaging, or chasing false positives, at the end of the day, the value they bring to their organizations is their ability to ask and find answers to difficult questions around security incidents. Much like a skilled mechanic, they are often tasked with quickly assessing the scope of a problem, then putting together a plan for repair. At Exabeam, we believe that arming these knowledge workers with the right tools to perform their job is key to the success of the SOC and providing value to the rest of the organization.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













