Question: What do a wave of baby boomer retirements and a trend toward outsourcing have in common?
Answer: The inability of state and local governments to fill cybersecurity jobs and increased risk of data theft.
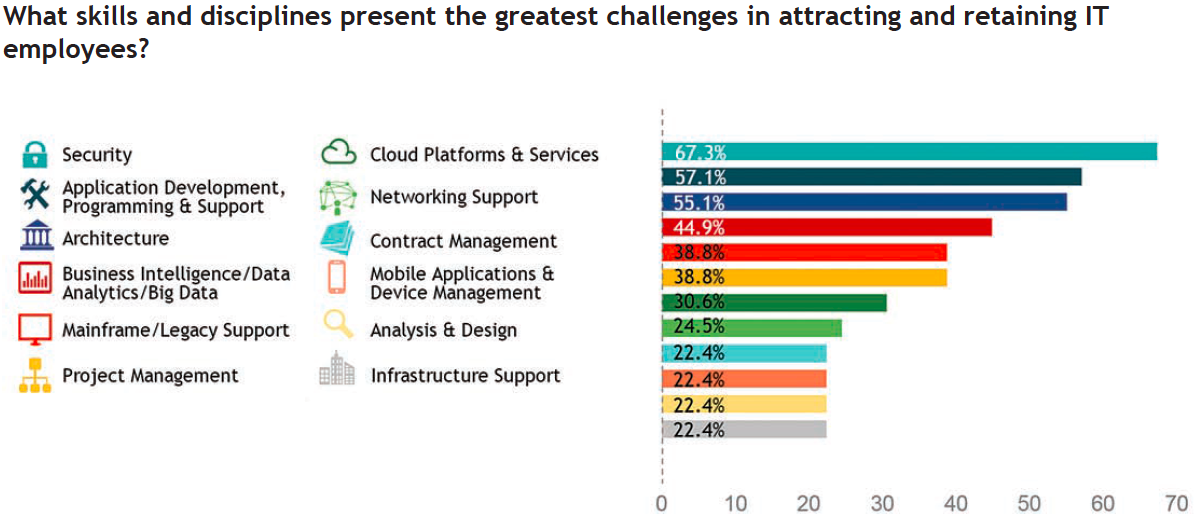
It’s clear that years of wage and hiring freezes have made retirement or a move to the private sector an easy choice for cybersecurity pros in the public sector. From a recent article titled, States struggle to hire cybersecurity experts, “A run on retirement by an entire generation of baby boomers has exacerbated the shortage of qualified IT staff, with 86 percent of managers reporting they are having trouble filling vacant tech positions. The federal government isn’t immune to this trend as it’s been sited that the number of security personnel there has gone from over 400 to the mid-300’s. When asked what skills are most challenging to attract and retain, two-thirds of state IT managers surveyed said “security,” followed by 57 percent who said, “programming and support.” This trend is illustrated in figure below is from the 2015 NASCIO, “State IT Workforce: Facing Reality with Innovation survey.
This got me thinking about the recent attack at the IRS where hackers were able to request back tax returns for an estimated 100,000 people using data they’ve already collected. Where could this data come from? Of the organizations reporting data breaches in the last two years, ten data breaches ranging in size from 100,000 records to millions have been from state governments. While I’m not saying that citizen data used in the IRS fraud attack was stolen exclusively from state governments, this could be one likely source. Yes, I can hear those saying healthcare data can contain SSNs as can HR databases. What I am asserting is these problems are related. To identify fraud, it’s easy to link recent data breaches at the IRS and state governments to the shortage of cybersecurity personnel shortage, budget cuts, pay freezes and attrition.
What do we do about it?
While academic institutions are doing their best to educate more future cybersecurity professionals, most will opt for jobs in the private sector. Many will go to outsourcing companies to which state and local governments will continue to contract. Overall, this means security organizations need to hold vendors accountable for providing solutions that make fraud detection simpler and security operations more efficient.
One area in dire need for support is detection and incident response. Solutions in this area usually are either one or the other — detection or incident response. One always leads to another as the next logical step. When we look at the current targeted attacks, it’s clear attackers know what kinds of defenses are in place and can figure out how to evade them. Even vaunted malware sandboxes aren’t a perfect solution when adding a few lines of code allows malware to detect the sandbox and not execute their malicious code. Once the malware is found, it often takes hours, days or weeks to find all of the hosts that were touched to determine which accounts were compromised and understand what data was stolen. This is hard and time consuming even for the most experienced cybersecurity professionals. This is due to processes built around the disjointed “detection OR incident response” crop of products organizations have bought.
While user behavior analytics products recently on the market give you additional visibility to do a good job of detection, most do not have the capability to build out the entire attack chain…except for Exabeam. Exabeam learns normal behaviors to reveal those that are abnormal, assembles them into user session time lines that include relevant security alerts all in real-time. Not only will you see see the unusual behaviors, you’ll also save hours, days or weeks of time and lower the skill set required to detect and respond.
But please don’t take my word for it…press the demo button below. A 30-minute demo could save your data and weeks of your response team’s time.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











