How does your SOC stack up? If you are asking the question, now you can compare your company’s security operations center to peer responses in the Exabeam 2019 State of the SOC Report. It’s our second annual comprehensive survey of U.S. and U.K. cybersecurity professionals who manage and operate SOCs.
Exabeam’s May 2019 survey included CISO, CIO, frontline security analyst, and management roles. We asked respondents like you about basic SOC operations, hiring and staffing, operational processes, technology, and finance and budget. Based on responses, the survey algorithmically determined if a SOC was highly effective (35%), effective (40%), and less effective (25%) in its approach to safeguarding enterprise security.
Some key findings from our report include:
Basic Operations
CIOs and CISOs are more concerned about incident response, automation, and threat hunting while SOC analysts are more focused on procedure and policy, monitoring security tools, and investigations.
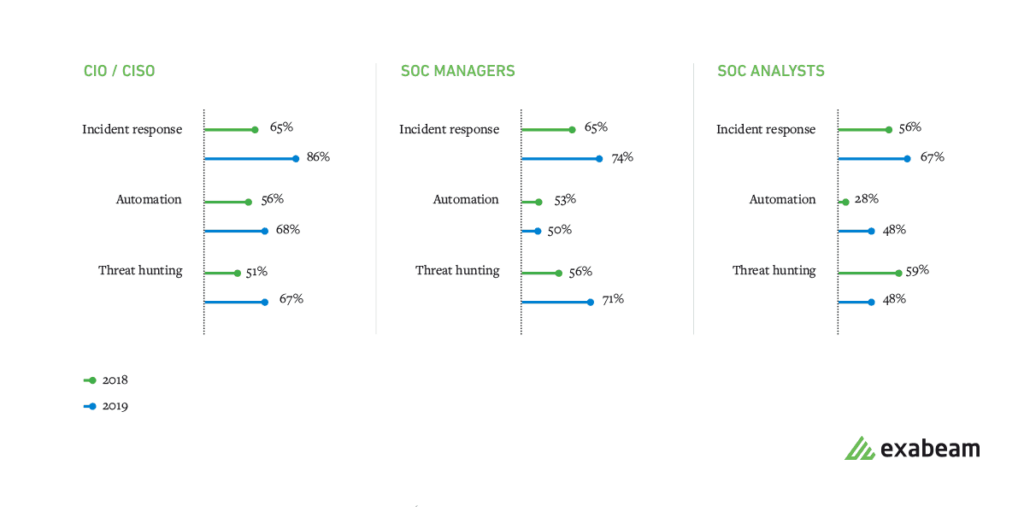
Figure 1: Incident response, automation and threat hunting are areas of concern for SOC leaders and managers.
86% of CIOs / CISOs are involved with incident response (up from 65% a year ago)
67% of CIOs / CISOs are involved with threat hunting (up from 51% a year ago)
48% of SOC analysts use automation (up from 28% a year ago)
50% of SOC managers are involved with automation
Almost half of SOCs continue to outsource business activities. Malware analysis, threat analysis, and threat intelligence are the most frequently outsourced functions. SOC analysts are strongly involved in incident response and automation.
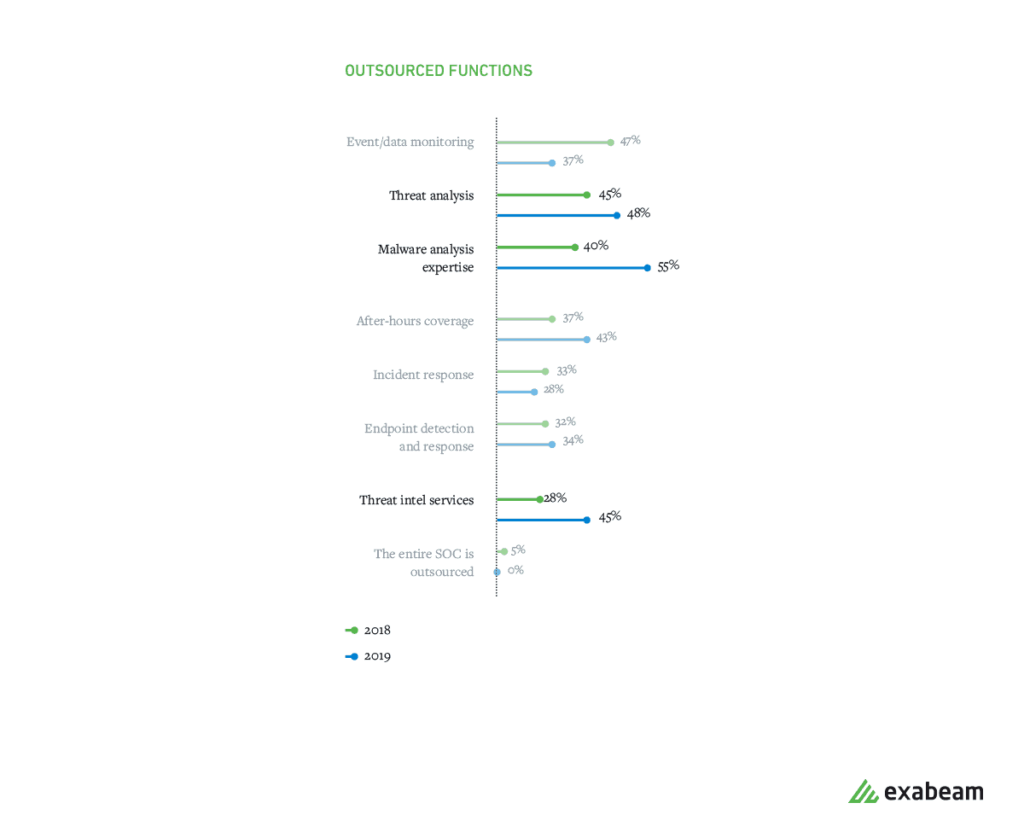
Figure 2: Of outsourced business activities, malware analysis, threat analysis, and threat intelligence are the most frequently outsourced functions.
55% of malware analysis expertise is outsourced (up from 40% a year ago)
45% outsource threat intelligence services (up from 28% a year ago)
37% outsource event/data monitoring (down from 47% a year ago)
Hiring and Staffing
SOC staffing remains an issue for many organizations and is most prevalent among less effective SOCs (46%) compared to more effective SOCs (29%). Retention remains strong due to competitive benefits (44%) and the good or challenging nature of SOC work (42%).
Notably, while hard skills remain critical, 65% of SOCs are placing increased emphasis on soft skills, particularly personal/social.
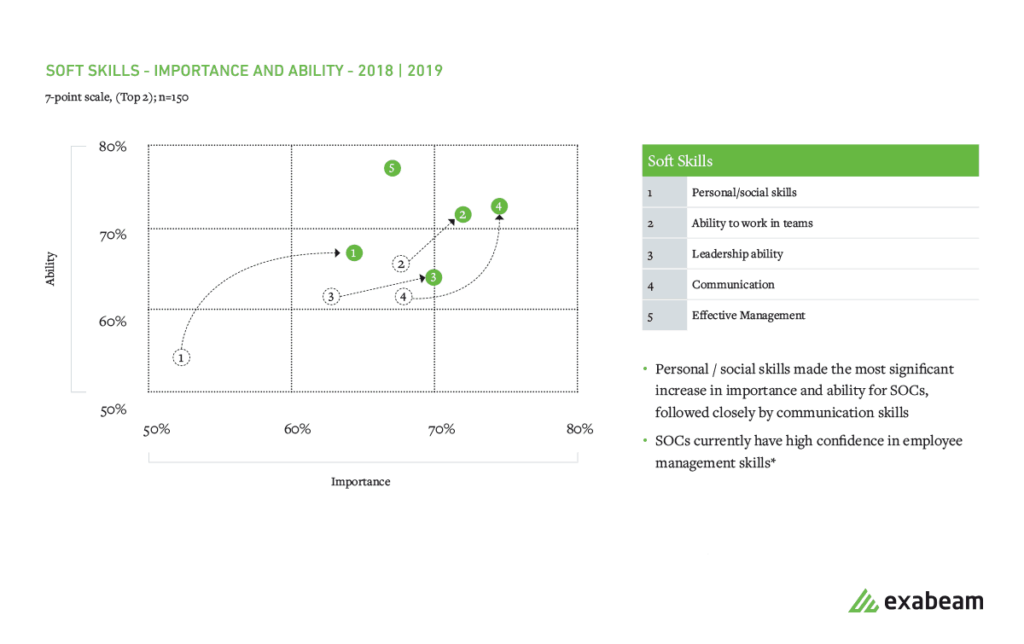
Figure 3: Personal and social skills increased the most in importance for SOCs followed by communication skills.
Process
Generally, SOC effectiveness is unchanged, but the perception of auto-remediation effectiveness has declined; 54% of SOCs were unable to perform auto-remediation (down from 68% a year ago).
All groups agree that too much time is spent on reporting and documentation, while the problem of inexperienced staff is greater in the eyes of CISOs and CIOs than with SOC staff and SOC managers.
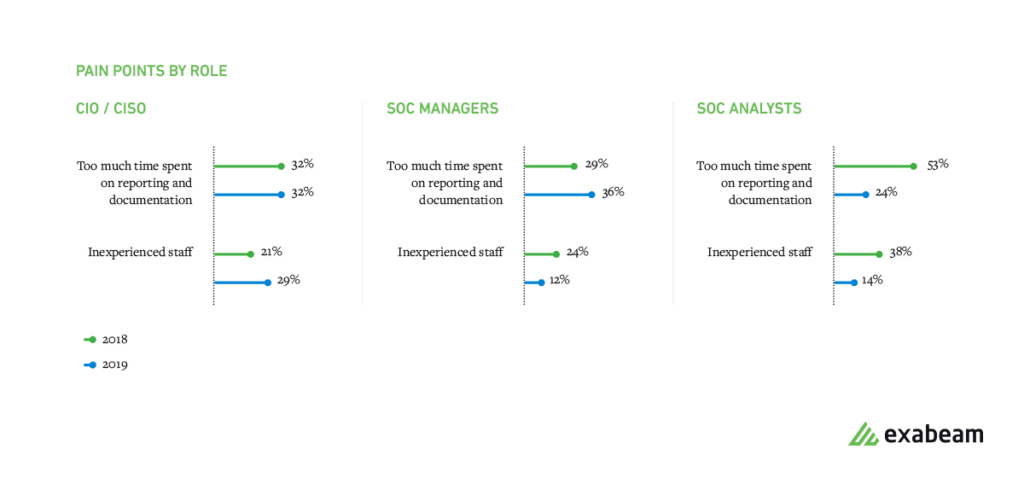
Figure 4: All groups agree that too much time is spent on reporting and documentation.
Technology
Big data analytics, endpoint detection/response, network/cloud monitoring, and identity/access management remain top technology priorities. Keeping up with security alerts remains the top pain point for SOCs.
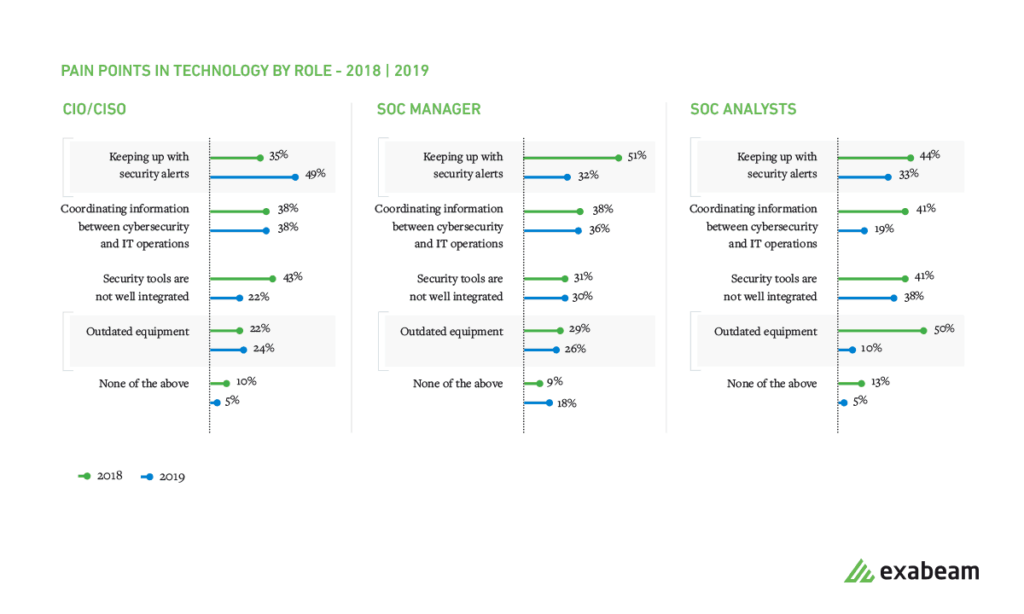
Figure 5: Keeping up with security alerts continues to be a top pain point for SOCs.
Finance and Budget
Technology investment as compared to staffing, facilities and management remains the most underfunded part of the SOC, a sentiment felt more strongly by Americans.
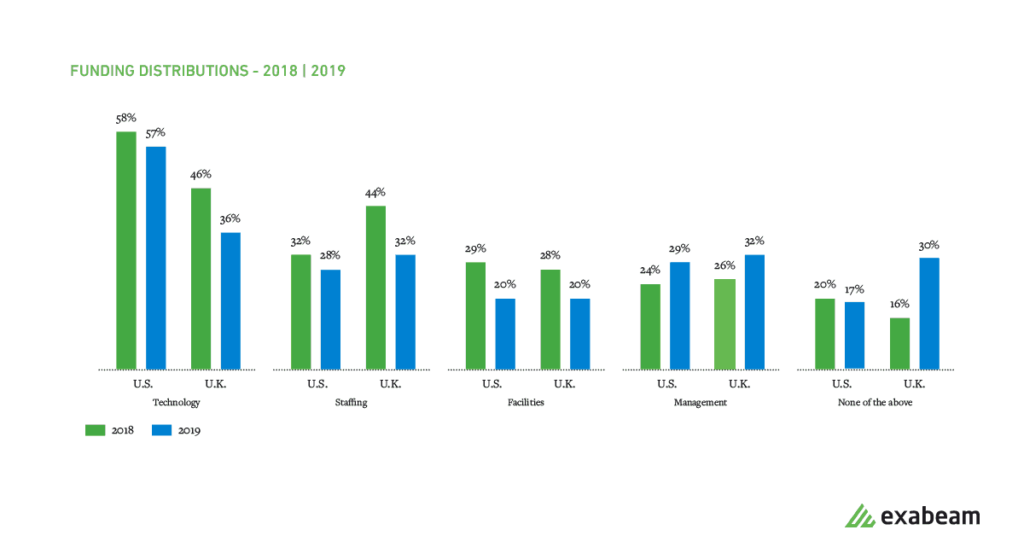
Figure 6: SOCs in the US and UK agree that technology investment remains an underfunded part of the SOC.
The complete report provides a more in-depth presentation of these and many other points of interest. We invite you to get your own copy of the complete report here.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












