Automated Investigation Experience
Automate and modernize the entire threat detection, investigation, and response (TDIR) workflow to gain a complete picture of a threat, reduce manual routines, and simplify complex work.
Automate and modernize threat detection, investigation, and response
Today’s cybersecurity teams are buried in a sea of noise, manually investigating alerts that often end with inconclusive outcomes. Exabeam offers automation across the TDIR workflow. Built-in timelines reconstruct the chain of events across all log sources, enriched with relevant context as well as scripted response actions allowing analysts to quickly see and act on meaningful alerts — recapturing two-thirds of the time an analyst spends on detection, triage, and investigation.

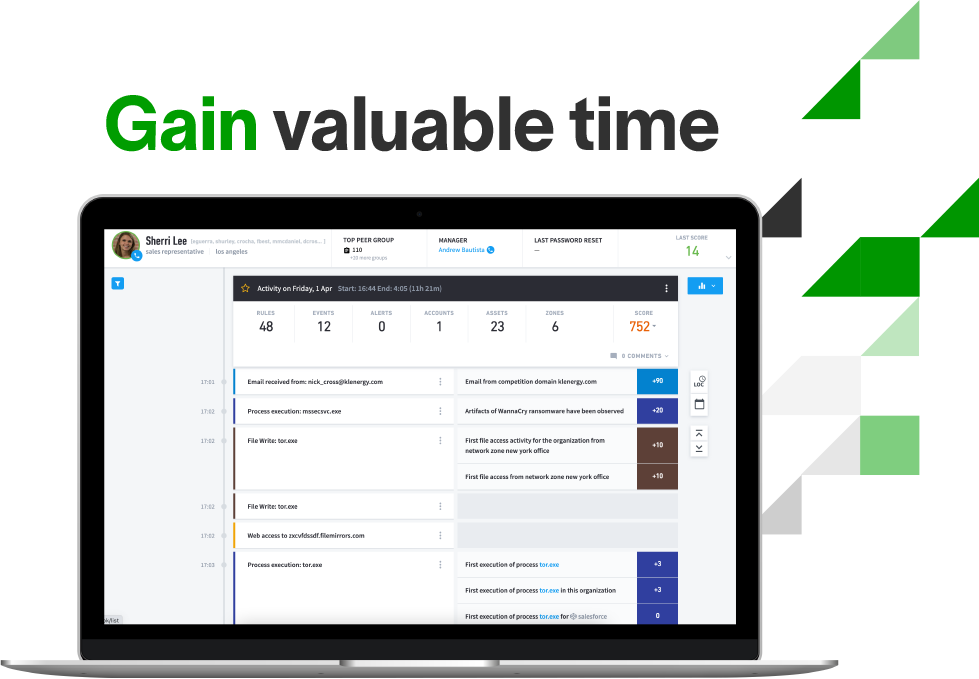
Smart Timelines™
Exabeam baselines normal activity for all users and entities, presenting all notable events visually and chronologically within an automated Smart Timeline. The timeline conveys the complete history of an incident and scores the risk associated with each event, saving an analyst from writing hundreds of queries.
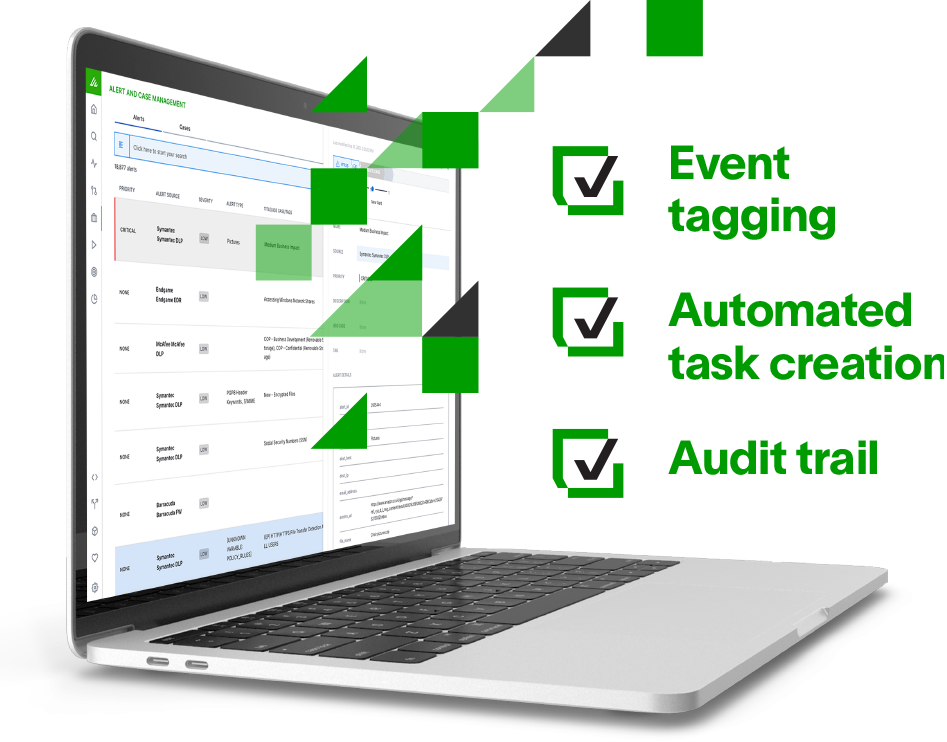
Manage alerts and cases with Threat Center
At the heart of the Exabeam Security Operations Platform is Threat Center, a unified workbench for TDIR. Within Threat Center users can manage incoming events at volume, and get machine learning-assisted insights to address the most crucial events that correspond to anomalies or high-value signatures. Analysts can manually or automatically sort events into incidents for focused investigation and/or escalation — or export cases into other third-party workflow solutions. Auto-attribution of alerts to users and assets, nearby anomalies, and user and host context provides additional context for more effective triage and investigations. Within Exabeam Threat Center case management features allow event tagging, automated task creation with assignment options, and an audit trail for the team’s steps through investigation.
Dynamic alert prioritization
Automates third-party alert prioritization using machine learning context to identify, prioritize, and escalate the alerts which require the most attention. Classifying alerts provides a starting point for the analyst to begin the triage process, focusing time and resources on the alerts of highest risk to the organization.
Outcomes Navigator
Outcomes Navigator maps the feeds that come into Exabeam against the most common security use cases and suggests ways to improve coverage. Outcomes Navigator supports measurable, continuous improvement focusing on outcomes by recommending information, event stream, and parsing configuration changes to close any gaps.


Automation Management
Automation Management compliments Threat Center allowing analysts to orchestrate and automate repeated workflows with APIs to numerous third-party vendors and products with hundreds of actions and operations, from semi- to fully-automated activity. With Automation Management, analysts can automate gathering key pieces of information about incidents through pre-built integrations with security and IT tools, and run response playbooks to programmatically perform investigation, containment, or mitigation. Running response playbooks allows organizations to respond to threats faster and more consistently.
Automation Management includes an intuitive, self-service interface guiding administrators to build custom response actions or set up integrations with third-party IT and security tools. The ability to easily create custom actions and build new playbooks supports creating repeatable workflows, accelerating an organization’s time to remediation (TTR).
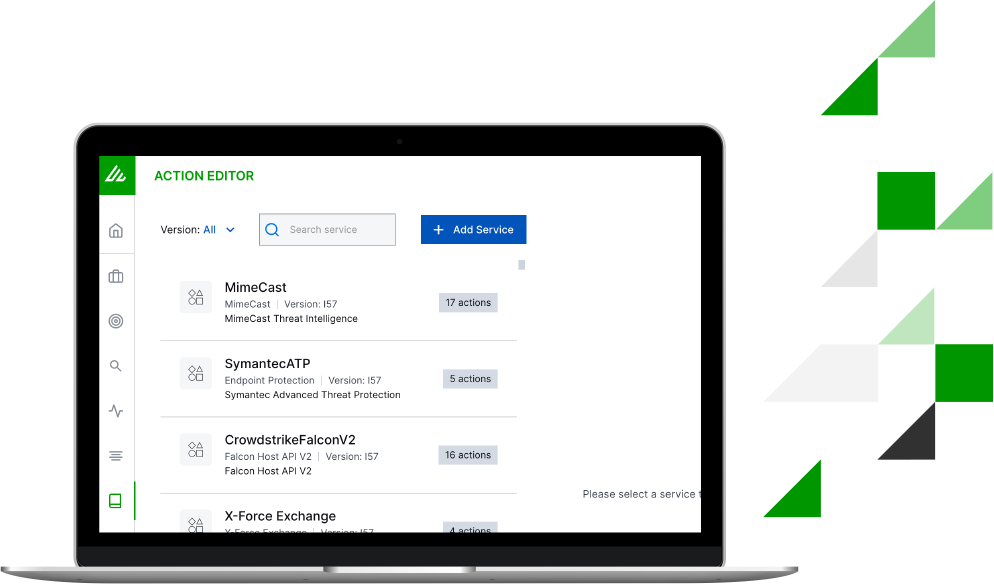
Action Editor
An intuitive, self-service interface guides administrators to build custom response actions or set up integrations with third-party IT and security tools. The ability to easily create custom actions and build new playbooks supports creating repeatable workflows, accelerating an organization’s time to remediation (TTR).

MITRE ATT&CK® Coverage
The Exabeam Security Operations Platform uses the ATT&CK framework as a critical lens to help improve the visibility of your security posture. Support for ATT&CK spans all 14 categories, including 199 techniques and 379 sub-techniques in the ATT&CK framework.
Context Enrichment
Context enrichment provides powerful benefits across several areas of the platform. Exabeam supports enrichment using three methods: threat intelligence, geolocation, and user-host-IP mapping. Armed with the most up-to-date IoCs, our Threat Intelligence Service adds enrichment such as file, domain, IP, URL reputation, and TOR endpoint identification to prioritize or update existing correlations and behavioral models. Geolocation enrichment provides location-based context often not present in logs. Outside of authentication sources, user information is rarely present in logs — Exabeam’s user-host-IP mapping enrichment adds user details to logs which is critical to building behavioral models for detecting anomalous activity.

MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
anomaly rules
Over 1,800 anomaly rules, including cloud infrastructure security, with over 795 behavioral models that automatically baseline normal behavior of users and devices.
reduction in investigation times
Build repeatable workflows to semi- or fully-automate your response activity. 1
1 The combined reduction organizations achieved in a recent study.
Frequently Asked Questions
Answer: Exabeam has hundreds of pre-built integrations with IT and security products, providing a myriad of inbound data sources and response integrations. Please refer to the complete list of integrations.
Answer: Security analysts can filter their view to display third-party alerts by priority. High priority alerts pose the largest threat to your organization. Low priority alerts have the potential to pose a threat, and observational alerts are alerts that Exabeam has classified as repetitive, or noisy. Classifying alerts as high-priority provides a starting point for the analyst to begin the triage process, focusing on the alerts of highest risk to the organization. A security analyst can choose to filter their view based on priority, or see the complete list of alerts.
Answer: Exabeam offers pre-built incident checklists for common incidents, including compromised credentials. Checklists are recommended remediation steps and response playbooks for incident response teams. For specific incident types, there is also the ability to build custom checklists.
Trusted by organizations
around the world





















“We were finding our analysts extremely frustrated with the day-to-day working of previous products. With Exabeam, it was like a breath of fresh air. It’s clean, fresh, fast, and responsive. Something that could have been a 15 or 20 step process is now done with a few clicks.”
Shawn Kay
Cybersecurity Analyst | Interact Software

Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision










