Exabeam Security Log Management
Exabeam Security Log Management can ingest, parse, store, and search log data at scale with a cloud-native data lake, hyper-quick query performance, and dashboarding with options for multi-year log archives.
Cloud-scale Security Log Management
Exabeam Security Log Management offers the industry’s most advanced cloud-native solution in support of security use cases. The product represents the entry point to ingest, parse, store, and search security data in one place, providing a lightning fast, modern search and dashboarding experience across multi-year data. Exabeam Security Log Management delivers affordable log management at scale, without requiring advanced programming, query-building skills, or lengthy deployment cycles.
Cloud-scale visibility
Exabeam Security Log Management is the industry’s most advanced cloud-native solution for security use cases. A powerful user interface allows you to onboard security logs and data to build and monitor parsers, as well as visualize the data consumption and the health of every Exabeam service. Drive desired security outcomes to close critical gaps by understanding your data source coverage and configuration. Learn precisely what to do to improve your security posture by seeing recommended information, event streams, and parsing configurations that adapt to your organization’s needs.
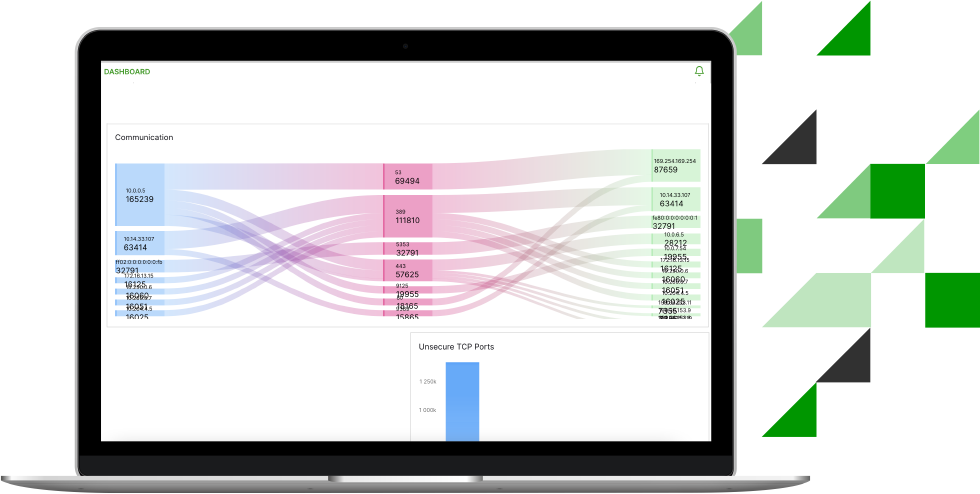

Comprehensive log collection
Securely collect data from on-premises or cloud data sources using a single interface. Parse each raw log into a security event as data travels from the source, identify named fields, and normalize them using a common information model (CIM) for accelerated analysis and added security context. A wizard enables custom parser creation from new or templated log sources, making it easy to develop, deploy, and manage error-free parsers.
- 470+ products under 56 categories, from more than 250 different vendors
- Multiple transport methods: API, agent, syslog, SIEM data lake
- 30+ cloud-delivered security products
- 10+ SaaS productivity applications
- 20+ cloud infrastructure products
- Over 9,500 pre-built log parsers
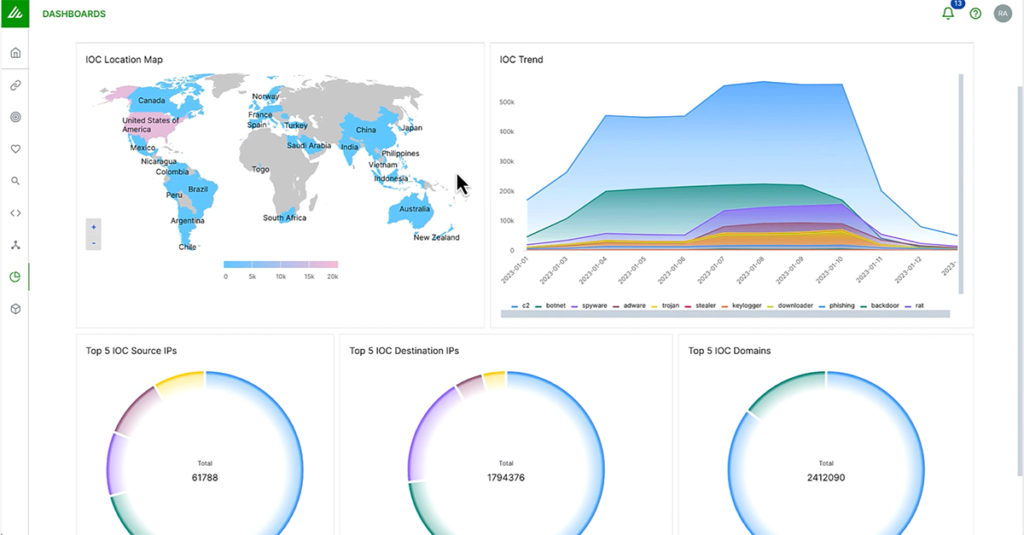
Fast, intuitive search capabilities
An essential capability of Exabeam Security Log Management is Search — a single interface that allows analysts to search across active and archived data using natural language. Additionally, parsed data from Search can be used to quickly create correlation rules, along with 45+ pre-built compliance dashboards.
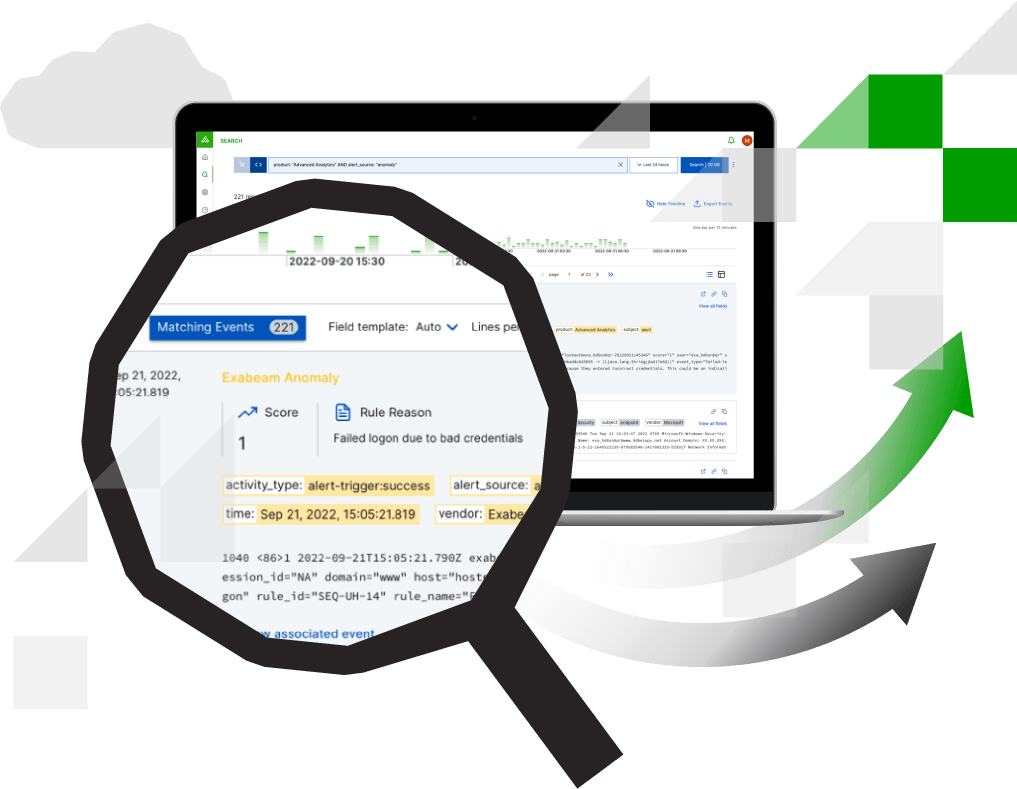

Automated investigation experience
Turn your searches into powerful threat-hunting rules in one click. Properly designed correlation rules enable enterprises to surface a broad range of abnormal behavior and events. To identify these anomalies, define conditions that function as triggers by comparing incoming events with predefined relationships between entities. Write, test, publish, and monitor custom correlation rules for your most critical business entities and assets, including defining higher criticality for those that correspond to Threat Intelligence Service-sourced activity. Add context enrichment to events from multiple commercial and open source threat intelligence feeds, which aggregate, scrub, and rank them, using proprietary machine learning algorithms to produce a highly accurate, up-to-date stream of IoCs.
How it works
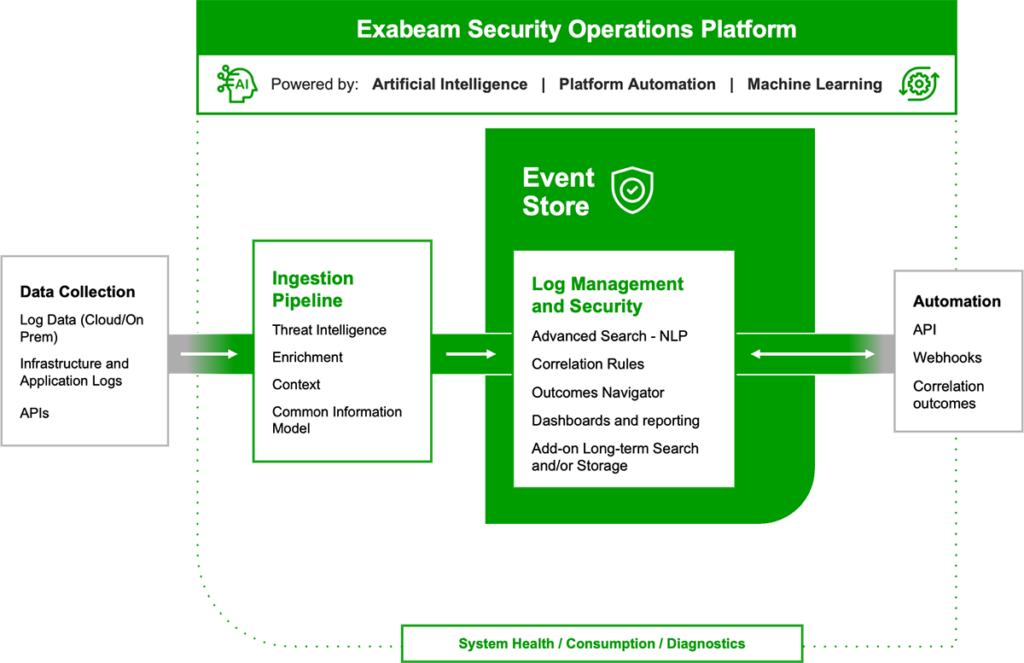
Exabeam Security Log Management ingests, parses, and stores logs; it also uses a new common information model (CIM), data enrichment with threat intelligence, and other context to help create security events. Correlation Rules provides a single interface to write, test, publish, and monitor custom correlation rules to define conditions that function as triggers by comparing incoming events with predefined relationships between entities to identify and escalate anomalies.
integrations
Collect data from more than 680 different product integrations across 350+ different vendors.
pre-built compliance dashboards
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS.
Exabeam Security Log Management features
Exabeam Security Log Management provides a powerful and affordable log management solution, purpose-built for security, that your teams will want to use without a massive learning curve.
Collectors
Collect data from on-premises or cloud data sources from 22 product categories, 292 different vendors, and 549 different products with over 9,500 pre-built log parsers.
Log Stream
Rapid log ingestion processing over 2M events per second using a new common information model (CIM) and parsing at ingest. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline.
Common Information Model (CIM)
The Exabeam CIM provides normalized, security-relevant logs that are faster and easier to parse and, store, so vendor information can be accessed effortlessly.
Search
A simplified search experience with faster natural-language query and instant results over petabyte scale and/or years of data.
Reporting and Dashboards
Print, export, and view dashboard data with pre-built compliance reports, and customize dashboards with 14 different chart types.
Correlation Rule Builder
For your most critical assets, write, test, publish, and monitor custom correlation rules, including defining higher criticality for events that correspond to Threat Intelligence Service-sourced activity.
Outcomes Navigator
Outcomes Navigator maps the feeds that come into the platform against the most common security use cases and suggests ways to improve coverage.
Service Health and Consumption
Visualize your service health for every Exabeam service and application, as well as data consumption, while monitoring your connections and sources.
Threat Intelligence Service
Available at no additional cost and refreshed every 24 hours, the Exabeam Threat Intelligence Service ingests commercial and open source feeds, then aggregates, scrubs, and ranks them, using machine learning algorithms to produce a highly accurate stream of IoCs.
Put Your Security Skills to the Test
Challenge yourself and compete with peers in a formidable game of Exabeam CTF. You’ll get a firsthand view into the power of Exabeam behavioral analytics, threat hunting, and automation and their ability to transform your team’s TDIR capabilities.

“Since we’ve had Exabeam on board, the visibility, detection, and rich feature set has given us a different lens with a huge amount of context around an incident, which has informed our decision making and led to faster response times.”
Lindbergh Caldeira
Security Operations Manager | SA Power Networks

Trusted by organizations
around the world





















Frequently Asked Questions
Answer: Collect data from on-premises or cloud data sources from 22 product categories, 292 different vendors, and 549 different products with 7,937 log parsers pre-packaged.
The platform support several log format standards such as SysLog to ingest nearly all the data in your security stack.
Answer: All your data is protected through an end-to-end encryption data flow pipeline. We start by ingesting logs and data from APIs like Cloud Connectors into Exabeam Site Collector using secure communication channels (Syslog, agents, Kafka sources using SSL/TLS) in your environment and then upload them through TLS-secured channels onto the cloud-delivered Exabeam Security Management Platform (SMP). In addition, Exabeam Cloud encrypts data at rest to ensure the highest level of security for your data.
Exabeam is SOC2 Type II certified. To meet the requirements for certification we have developed and follow strict information security procedures and policies for the security, availability, processing, integrity, confidentiality, and privacy of customer data. This aligns with Exabeam’s ongoing commitment to create and maintain a secure operating environment for our clients’ data.
Answer: Yes. Our solutions are cloud-delivered and licensed accordingly. These solutions are priced by the volume of data ingested by your organization. As your security organization matures and brings in a wider variety and higher volume of data to support expanded requirements, Exabeam offerings can scale to meet your growing needs. SLM comes with one month of data storage, additional extended storage can be purchased.
Explore the many ways Exabeam can work for you
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, SOAR, and TDIR content, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- SIEM replacement: Exabeam Fusion
- SIEM augmentation: Exabeam Security Investigation
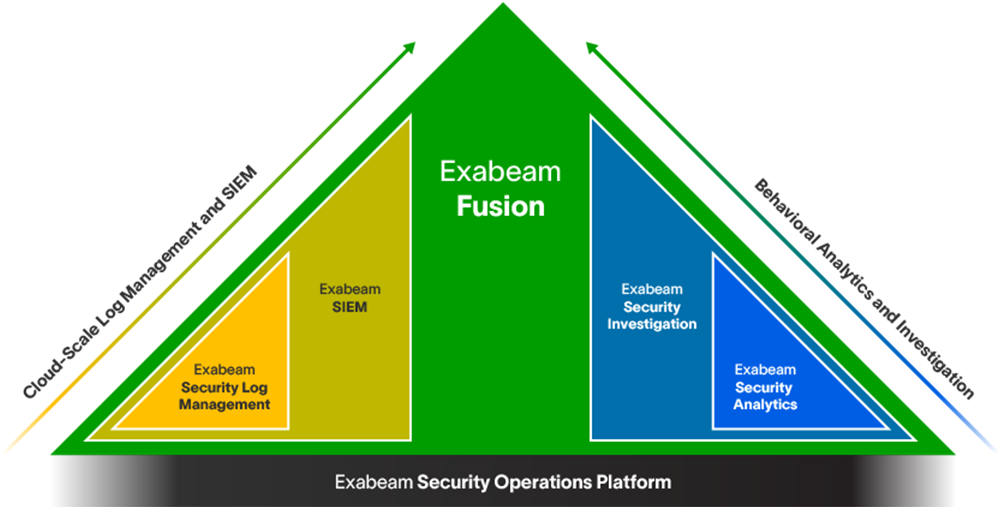
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision