I spent last week engaging with the 250 Exabeam customers and partners attending our annual user conference, Exabeam Spotlight19. It is a great opportunity to identify market trends.
Not surprisingly, the trends from Spotlight 2018 were still evident in presentations and discussions: cloud security, IoT, the skills gap, attack vector proliferation and big data (you can read my post from last year, here), but the conversation had also moved forward during the year. The uber theme for me this year was that folks were quickly making headway using existing and new tools to deal with these persistent challenges.
Discussion of the skills gap and how to deal with big data problems centered more squarely on automation as a solution. Similarly, MITRE’s ATT&CK knowledge base saw rapid adoption over the past year as a way to think about dealing with the proliferation of attack vectors. The most exciting trend for me though was to see how companies are stretching the tools they have to cover unique and industry-specific use cases, often outside their core security areas of responsibilities.
Automation
The need for increased automation in security operations is dire. A lot of cyber talent has a military or signal intelligence background so it was no surprise when one cybersecurity manager declared that the demeanor of his overworked team was synonymous to combat fatigue. Managers are in a situation where they can’t take anyone (engineers or analysts) off the front line.
The staff shortage is compounded by the volume of work. One of the retailers present is getting attacked 15 million times a month. They detect malware in an email every 2 minutes. Similarly, the head of a global cyber team that numbers in the 100s noted that the massive number of logs exceeds what humans can monitor. They see 10 billion events per month. His response? “We absolutely must automate!” They expect to replace all of their tier 1 analysts.
The news this year is that many attendees have begun marrying man with machine. For a cybersecurity manager in the construction business, the starting point is automating the mundane. This was echoed by many including a security leader in a law firm who is automating the simple stuff to, “take clicking, typing, copying and pasting out of the equation.” Another attendee took a broader approach: “engaging your brain requires a human,” he said, “otherwise evaluate how to speed up the process.”
MITRE ATT&CK
Another tool that is rapidly becoming part of the mainstream is the MITRE ATT&CK knowledge base. A good proxy for its rise in popularity is the growing number of Google searches over the past couple of years:
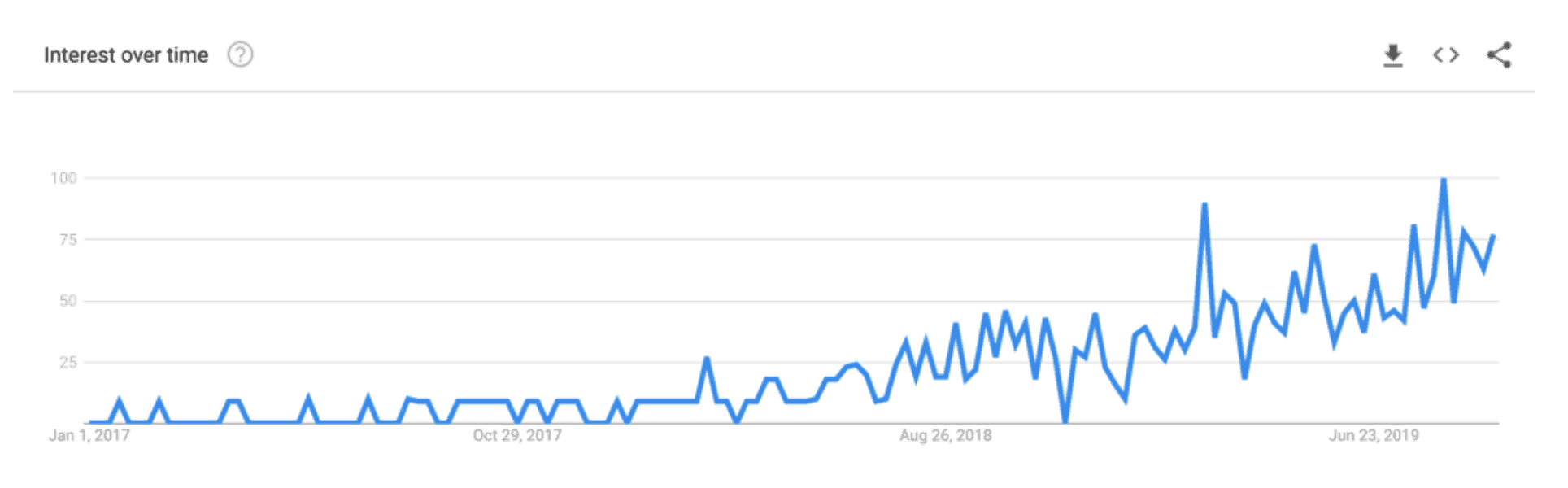
Google analytics data showing increased search volume over time for “MITRE ATT&CK”
A common starting point was for companies to use the knowledge base as a heat map. In his presentation, Kevin Urbanowicz, Managing Director, Cyber Risk Services at Deloitte, advocated that security teams use ATT&CK to identify blind spots and prioritize where to focus. In the words of another presenter, the goal of using ATT&CK was to build a “minefield” by being able to detect various techniques at each step of an attack.
Several presentations discussed how Exabeam allowed security teams to detect these techniques. Don Sheehan, Director, Cyber Services at Grant Thornton discussed how Exabeam helped detect Mimikatz, as an example of detecting the ATT&CK credential dumping technique. Hackers use credential dumping to obtain credentials typically in the form of a hash or Kerberos tickets. Both endpoint and network logs are required for this use case. Endpoint logs can be used to detect the downloading of Mimikatz, its hash and lsass (local security authority subsystem service) access while network logs can show the exfiltration of data and can detect a malicious destination IP. However, as Don pointed out, “legitimate lsass activity appears with high frequency in endpoint logs. In order to determine this instance is likely malicious, Exabeam analytics are necessary. By looking at the endpoint and network activity holistically and as a series of events, the lsass activity can be determined to be part of a potential attack involving credential dumping.”
You can read about Exabeam’s latest product feature releases, including the ability to use MITRE ATT&CK labels in investigations and threat hunting, here.
Industry-specific use cases
The final trend that jumped out to me involved the broader use of existing analytics and response tools. Some use cases like phishing and DLP are common across industries. No one was surprised that an attendee saw 20,000 messages being sent from two users two weeks ago and has 2-3 big phishing attacks per quarter. It’s also not news that every industry, in fact every company, has specific risks that they need to focus on more than others. What was new at Spotlight19 was the degree to which organizations had used Exabeam’s SIEM to deploy industry-specific use cases, and how some of those use cases were extending beyond traditional security and compliance.
Grant Thorton walked through a healthcare example. Organizations are monitoring electronic health records (EHR) for HIPAA compliance and general governance. For example, companies are conducting user activity audits and review distribution to understand how employees are accessing systems and data. They are also using analytical models to identify risks from other behavior, for example, to detect if a doctor accesses an abnormally high number of patient records compared to his past behavior or his peer group, or if that doctor is prescribing a drug to himself at a rate four times as high as his peers … all on Sundays.
In the finance sphere we recognized a bank with a Security Management Excellence award for both monitoring traditional security use cases as well as anomalies in their banking applications including SWIFT. The broader use of analytics allows the application and security teams to have a 360-degree view of employee behavior.

Exabeam CEO Nir Polak (with sunglasses) and award winners at Spotlight19.
Several airline customers stepped further outside of traditional cybersecurity use cases, monitoring baggage travel times and fraudulent use of friends and family buddy passes. Where the airlines were similar to most industries is that they monitor IT and other devices, the difference is that their devices are really big: they collect data from some planes every time they land at an airport (planes now have servers after all).
Other use cases are counter-intuitive outside of specific industries. For example, a law firm’s top three use cases were phishing, malware and web security. The third has unique applications at the law firm as they sometimes deal with cases that involve content that would otherwise be inappropriate for the workplace. However, their attorneys need to access the sites as part of their casework. Moreover, the sites that the security team needs to provide access to likely contain malware, further complicating their job.
Another counter-intuitive situation was discussed in the airline panel during the opening keynotes. It was pointed out that at an airline, a user could log in from Singapore, and again 10 hours later in New York and then 6 hours later in San Francisco. This type of “Superman” behavior would be alarming for most companies, but in the airline industry this is normal, and the security team needs to adjust their criteria for building baselines of normal behavior.
In conclusion
It is easy to get jaded by news headlines about the latest breach. While I don’t expect the headlines to go away tomorrow, it was great to hear from so many organizations about the progress they are making to reduce their risks.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












