Part 3 of the Security in the Cloud Series
“The physical security of source code does not get the attention it demands. Protecting source code is no less important than protecting data.”
– Michael Facemire, Forrester Research Vice President and Principal Analyst
Major global clothing companies have offices and factories located throughout the world. Like most large enterprises, clothing companies have software developers that are creating applications.
This blog focuses on a global clothing manufacturer that embraces cloud technology, using cloud services for software development and source code version control. It considers its source code to be intellectual property (IP) worthy of protection. They would be competitively and financially damaged if their source code fell into the wrong hands. Equally damaging, someone with malicious intent could inject malware or ransomware to interfere with operations or extort money in exchange for restoring access.
Source code is the human-readable blueprint for a computer application—instructions to make digital devices carry out intended tasks. Anyone with the appropriate skills and source code access can modify it to do things it wasn’t created to do—for example, provide “backdoor access” to other company resources.
The problem: Controlling access to cloud services
In many organizations, cloud credentials might be outside the scope of internal network security policies and controls. For example, it’s not unusual for software developers to provision their own cloud services and define their own credentials. They then proceed to create applications within their self-provisioned cloud services.
Should a developer leave the company, the standard off-boarding policies might not include removing their cloud-based resource access. The former employee can continue to access the cloud resources, and the company is unaware that a security breach is occurring.
In the case of the clothing company, terminated employees were using preexisting credentials to continue accessing cloud-based source code belonging to the company. Because the credentials remained valid after they left the company, the infiltrators wouldn’t have been detected through reviewing network access control logs.
Discovering the attack
GitHub is a cloud-based source code repository and management system often used among distributed software developers. Provided they have valid credentials for a given repository, globally-dispersed developers can contribute to the source code of any application stored there. The security issue of terminated employees still having access was not a GitHub shortcoming, but rather a gap in the way the clothing company deprovisioned those who had departed.
In our subject company, Exabeam Advanced Analytics discovered security breaches by analyzing logs from both GitHub and the company’s human resources (HR) system. The HR system had correctly flagged the developers as having been terminated, but the GitHub logs revealed that a few former employees had retained their credentials and continued to access the company’s source code repositories.
Preventing source code theft
The clothing company had used the log data from both GitHub and its HR sources to baseline normal employee behavior. All events for employees could be seen and investigated in Exabeam Smart Timelines, a feature of Advanced Analytics that captured these behaviors together with the other notable events and the users’ risk scores in a timeline.
Figure 1 shows a related, but fabricated, example of a Smart Timeline for a user who has given notice that they are leaving the company. Their risk score is elevated because they are logging into to their systems earlier than usual (anomalous behavior) and accessing GitHub remotely for the first time (another anomalous behavior)—a potential sign that they are looking to take corporate IP with them when they leave the company.
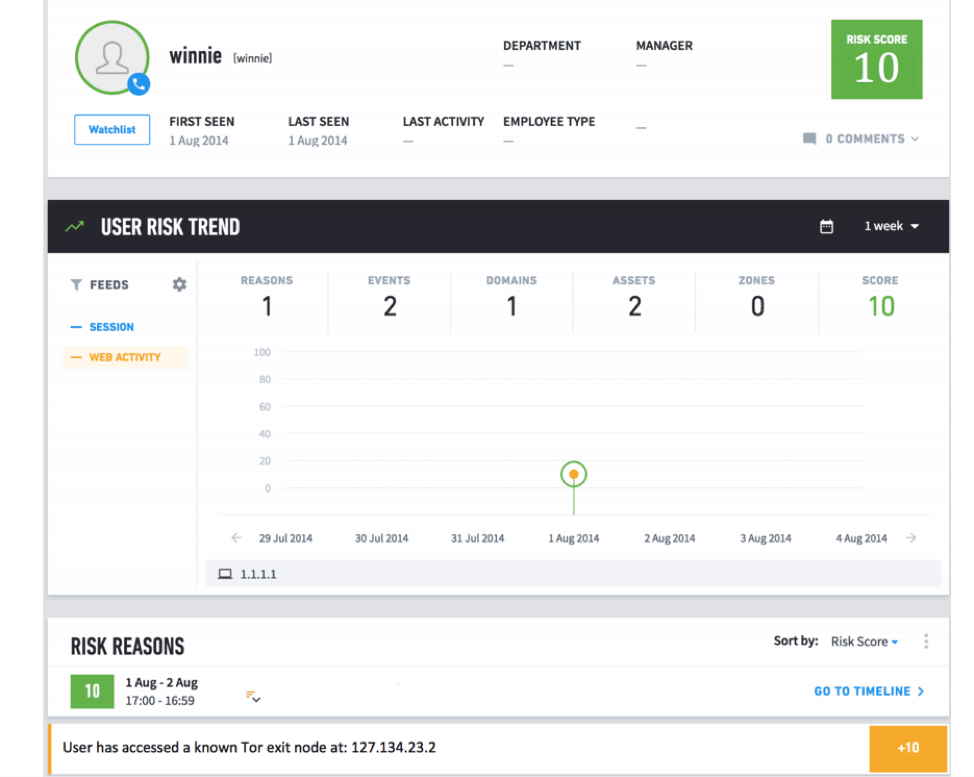
At the retail company, once Advanced Analytics surfaced the developers’ behaviors with an alert, it was a simple matter for security analysts to revoke the associated GitHub credentials so they could no longer access the source code resources.
The clothing company was fortunate to have collected HR system logs. Because of the traditional pricing model of most legacy SIEM products, customers pay based on their log volume. In an effort to reduce costs, organizations might decide to not include HR logs because they may not realize they could help expose security threats. Exabeam pricing isn’t based on log volume, so customers, like the clothing company, can include all of their available log data, without having to guess which logs might be useful in the future.
The importance of strategies for securing the cloud
With more enterprises deploying critical resources within their cloud services, the cyber threat landscape can extend to a larger attack surface that could be outside of security’s traditional span of control. Critical data might be aligned with the user credentials that they don’t manage. And it’s become more of a challenge to shut down access when employees and contractors depart an organization.
Now security teams can easily and immediately discover who is illicitly accessing their cloud resources and revoke their user credentials when the off-boarding process has missed this important step.
Advanced Analytics, based on user and entity behavior analytics (UEBA), automatically analyzes the user and entity behaviors across cloud networks—reducing risks in the cloud.
For more strategies on securing the cloud, see:
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












