Today we announced Exabeam Alert Triage, a new cloud application that categorizes, aggregates and enriches security alerts, so analysts can confidently and efficiently dismiss or escalate security alerts from a single screen. With Alert Triage, analysts get visibility into all of the alerts that security tools have triggered through a centralized view, reducing the likelihood of missing a security alert.
The Problem with Security Alerts Today
Today, analysts receive thousands of security alerts a day spread across disparate tools. Analysts must prioritize alerts to identify which pose the greatest risk to an organization and then decide which alerts to escalate for further review. However, security personnel say they are only able to investigate 45% of the daily alerts they receive, according to research from the Ponemon Institute. Why? One reason is that alerts provide little to no context, which makes it difficult for Tier 1 analysts to make decisions and requires them to spend a lot of time manually gathering evidence. The Ponemon report also notes that 33% of alerts in a traditional SIEM are false positives. Unable to keep up with the volume of alerts, they must ignore a significant number of security alerts and in doing so leave their organization potentially vulnerable to threats.
Success Requires a New Approach to Alert Triaging
Alert Triage categorizes, aggregates and enriches security alerts, so analysts can confidently dismiss or escalate them with new levels of efficiency. Alerts are organized into channels to prioritize and distribute them for review, while similar alerts are also aggregated so they can be reviewed as a group.
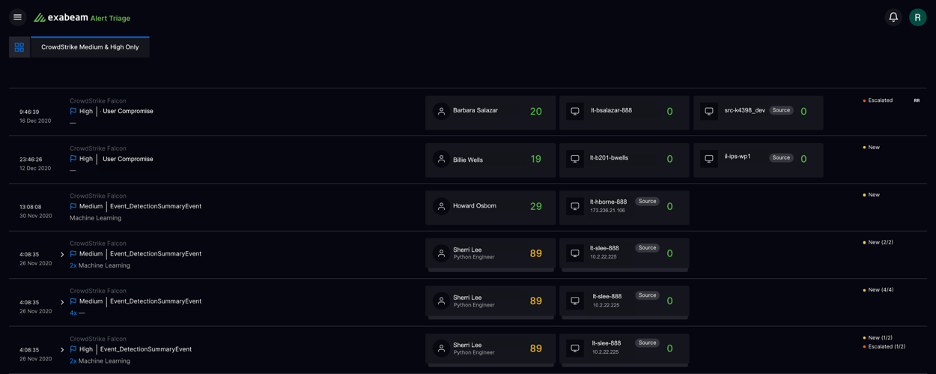
All alerts are then automatically enriched with contextual data including host, IP, severity of alerts, related behavioral anomalies and overall risk scores of associated users and entities. Armed with this information analysts can make a judgment call, without needing to navigate to other products to gather evidence.
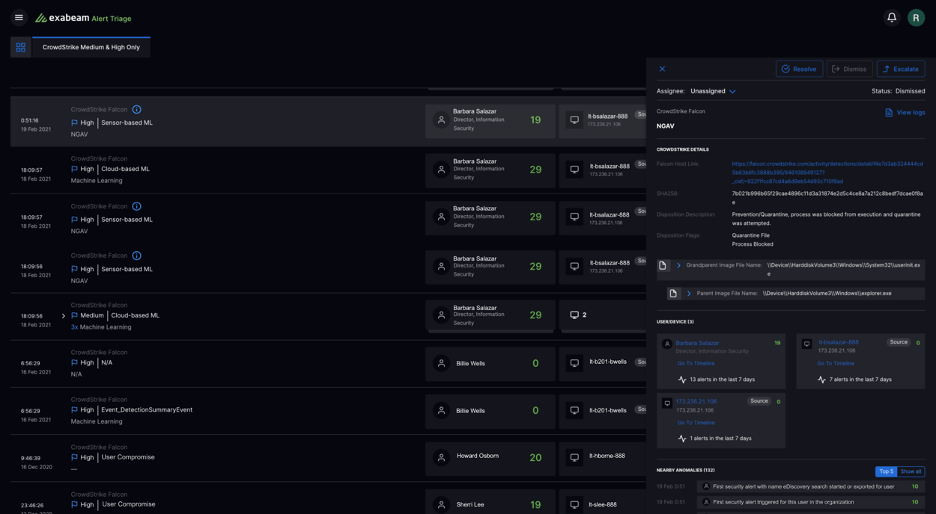
From within an alert in Alert Triage, security analysts can easily navigate to an associated user or entity timeline containing that alert. The timelines answer questions an analyst has like what happened before and after the alert was triggered. The timelines also provide context and answers to questions like:
- What is the nature of the alert?
- Who is the user/asset associated with the alert?
- Is this an actual attack?
- Was the attack successful?
With context readily available, analysts can rapidly triage alerts without the need to pivot and query in a SIEM.
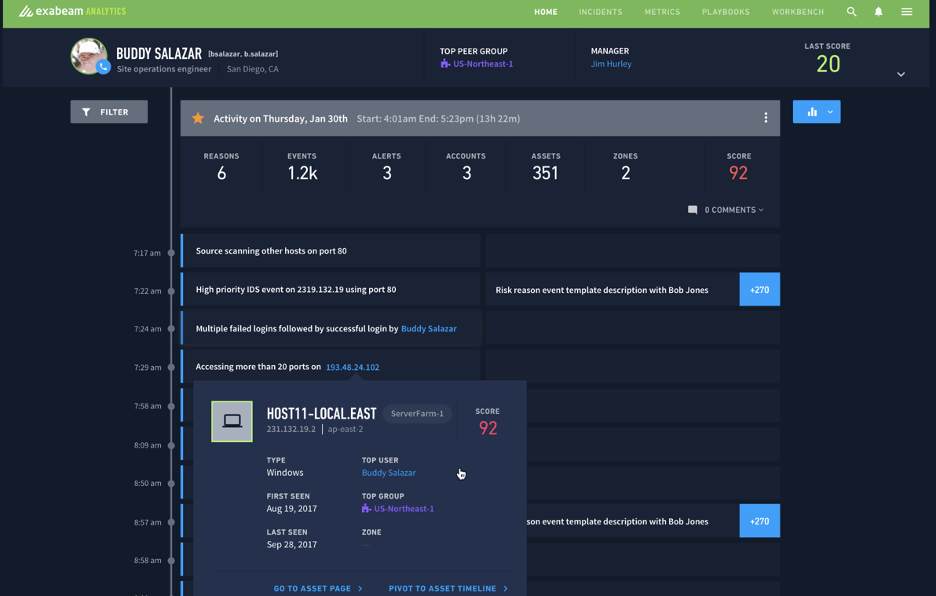
Integration with Case Manager
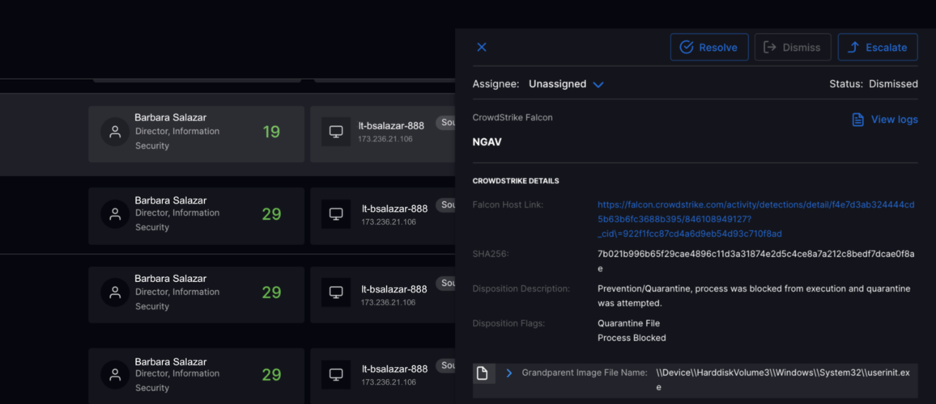
The Alert Triage interface gives analysts the option to dismiss or escalate the alert. When an alert is escalated, an incident is automatically created in Exabeam Case Manager, handing off the alert to the incident response team. The case includes alert-specific information like alert name, type, and severity for an Incident Responder to quickly continue the investigation. Automation of the triage process expedites an analyst’s ability to triage alerts and improves collaboration between triage and response teams.
Outsmart the Odds with Alert Triage
Analysts are spending valuable time focused on false positives, often missing the most urgent and dangerous threats to their organization. With Alert Triage, analysts get improved visibility, security and productivity, allowing them to focus their efforts on the highest priority alerts and take action on them, for a complete and seamless workflow.
Learn more about Exabeam Alert Triage and let us help you outsmart the odds.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












