Exabeam and KPMG co-hosted a special online session titled “Manufacturing Industry CISO Roundtable – From ‘Prevention’ to ‘Discovery,’ the Future and Present of Security Monitoring” on October 20, 2021. The session covered trends in security incidents alongside the approaches and concerns of participating companies regarding security monitoring, and an active discussion took place on the future outlook in the field.
In this report, we introduce the presentations and discussions that took place during the seminar.
The presentations were given by Natsuko Sugimoto, Senior Manager at KPMG Consulting, and Tetsumi Umehara, Sales Engineer at Exabeam Japan. The discussions took place between CISOs from seven manufacturing companies with global business operations.
How do we strengthen security monitoring and what perspectives do we need to take against cyberattacks that have been increasing in number and diversifying in recent years? In the discussion, CISOs addressed these issues while sharing their real-life experiences and challenges faced in their work.
Opening session: “Recent Trends in Security Incidents”
First to speak at the event was Mr. Tomoki Sawada, a partner of KPMG Consulting, who described the concept of the seminar, saying, “Today we would like to introduce recent security trends and have an informal discussion with the CISOs present here about the future of security, and especially monitoring. I hope everyone can actively exchange opinions in their areas of interest and learn from other companies’ activities.”
In the first presentation, Mr. Sugimoto of KPMG Consulting introduced “Recent Trends in Security Incidents.”
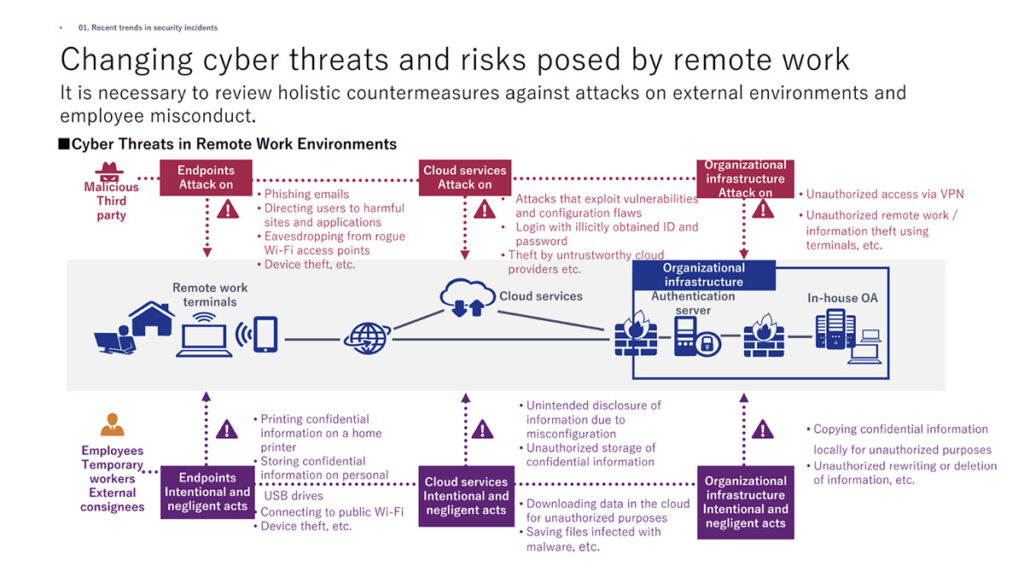
In recent years, cyber attacks have become increasingly advanced and sophisticated, and now include the exploitation of system vulnerabilities and attacks that prey upon employee psychology. One recent trend indicates that companies are struggling to prevent damage from overseas security incidents. In these so-called supply chain attacks, instead of directly attacking the target company, the attackers use weakly secured business partners or subsidiaries as steppingstones to reach their destination.
In addition, more damage is being caused due to business fraud and ransomware, while sophisticated attacks using ransomware are being launched to monetize attacks featuring double or triple extortion threats.
Remote work has become a common practice during the coronavirus pandemic, and this has created new security challenges. Because employees can now work from anywhere, companies need to rethink the conventional approach of “protecting what’s inside the company” and consider attacks on external environments alongside instances of employee misconduct.
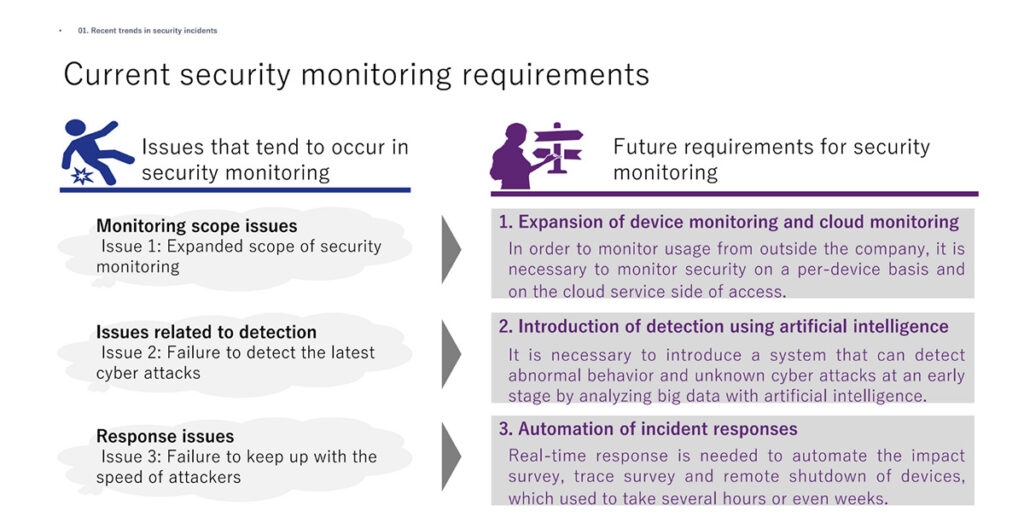
Based on the trends in security incidents mentioned above, Mr. Sugimoto identified three issues that need to be addressed: expansion of the scope of security monitoring, inability to detect the latest cyberattacks, and inability to keep up with the speed of attacks.
It has become apparent that security monitoring cannot keep up with changes in system usage environments, as evidenced by the increasing sophistication of advanced attacks on servers and the growing use of cloud services. Cyber attacks are evolving day by day, and it is often the case that security monitoring and systems cannot cope with the evolution and speed of attacks, including those in which it is difficult to distinguish between normal and abnormal communications and attacks that take place before security patches are issued.
In response to these issues, Mr. Sugimoto noted that “The security monitoring requirements necessary needs to include expansion of device monitoring and cloud monitoring, the introduction of detection using artificial intelligence and automation of incident responses.”
“We need to expand our monitoring system, which to date has been focused on networks and the Internet, to include devices and cloud services. Moreover, we need to create a mechanism for highly accurate predictive detection using AI and machine learning and automation combined with other technologies such as SOAR” he said.
Discussion: ‘Approaches to security monitoring by each participating company (the situation today)’
How do companies protect themselves against the growing threat of cyberattacks? In this discussion, participants outlined initiatives being taken at their respective companies and described the issues and concerns they’re facing.
One of the participants from a large comprehensive construction company shared, “We have introduced EDR and are working on monitoring using internal and external SOC functions. However, we have not yet started constant log monitoring for insider threats. Neither have we started to automate our responses. The events flagged as a high alert are different each time, so we have to interview users one-by-one and respond to the situation.”
“We recently expanded our use of EDR, and alerts are gradually starting to be generated. However, the alerts are difficult to analyze, and from the standpoint of CSIRT, it’s sometimes difficult to know how we should respond to users. In addition, we only receive high-level and critical alerts from the SOC. We have not been able to clarify how to handle smaller events involving files displaying suspicious behavior, and we are struggling to deal with them.” A CISO member from a major comprehensive chemicals manufacturer said.
Another participant from a major electronics manufacturer also shared that, “The use of EDR has been increasing over the past two to three years around the world, and the biggest concern has been complying with the laws and regulations of each country. Laws and regulations on data transfer have become stricter, and it takes time to complete contractual procedures and coordinate with lawyers for monitoring at the center. We are wondering how to conduct global monitoring in light of the laws and regulations in each country.”
As it became clear that each company was increasingly using EDR and the participants shared their concerns, the discussion turned to the topic of “the ideal format for global monitoring.” At this point, Mr. Sawada from KPMG Consulting gave his thoughts on global monitoring based on a case study.
According to Mr. Sawada, “We examined a case study of a company which consolidates its center in one single global location to execute 24-hour integrated security monitoring. It is difficult for an IT department to proceed with EDR of its own accord since the General Data Protection Regulation (GDPR) rules apply when collecting logs. In the future, a third state-level law will be enforced in the U.S., and regulations on personal information are being established in Singapore, Brazil, and Thailand. In addition, responding to China’s cyber security law is a pressing concern. We believe that we need a global monitoring system that considers these issues.”
Mr. Sawada then asked each company about its existing global monitoring system. It became clear that each company used a different monitoring system, whether it was centralized monitoring, a system integrated with Office365’s SOC, or an external service called MSS.
In the discussion on CSIRT systems, while each company used a different system, they all have in common the fact that they’re operated by a limited number of people. By collaborating with their domestic and global offices, group companies, and partner companies, these companies operated with a small support team size considering the size of their companies. Thus, it was evident that each company needed to automate and improve the efficiency of its security operations.
Presentation: ‘Exabeam Use Case Introduction and Demonstration’
Next, Mr. Umehara from Exabeam Japan presented ‘Exabeam Use Cases.’ His presentation began with an introduction to the “Challenges in Promoting Security Measures” survey conducted by IPA in 2020. In the survey, the top three issues cited by the CISOs of each company were “Difficulty in or inadequate risk visualization,” “Inadequate preparation for incidents,” and “Lack of expertise among responsible personnel.” These issues can all be solved by using Exabeam’s solutions.
According to Mr. Umehara, “The main concepts of Exabeam are to use logs to obtain a bird’s eye view on events, to prepare for incidents by creating timelines and playbooks in advance, and to automate SOC operations so that they can be handled by non-specialists.”
Although Exabeam is a next-generation SIEM, it is not just a log analysis and threat detection tool, but rather an ideal solution when used as a baseline and framework for developing advanced security operations.
“As the trend shifts from network monitoring to device monitoring, the SIEM required for next-generation security operations will collect logs originating from users and from as close as possible to applications, and record, store and analyze pre- and post-execution relationships,” said Mr. Umehara.
Speaking on the challenges in log monitoring due to the recent changes in the environment, Mr. Umehara pointed out the common issues that occur in the collection, detection, and investigation, such as the difficulty to collect logs, to detect threat signs before they happen, and the limited number of staff with a deep knowledge of SIEM queries.” Exabeam provides a solution to all these issues.
Mr. Umehara also shared that “Exabeam specifies the logs required to execute a particular use case and provides connectors and parsers to collect the logs. The major advantage of using Exabeam is that there is no need to spend resources or time on log collection. When it comes to threat detection, machine learning models and detection rules that analyze the collected logs are built-in beforehand according to the use case, freeing the user from the burden of maintenance. At the investigation stage, a timeline is automatically generated in advance without the need for any specialized queries. This means it’s possible to instantly identify the behavior of users and machines, greatly reducing the time required for investigation,”
After demonstrating the Exabeam solution, Mr. Umehara introduced the concept of ‘outsourced security operations’ with some recent user cases. “In many cases, SOC operations are outsourced due to manpower and system issues. However, the disadvantages of outsourcing are often overlooked,” he cautioned.
The disadvantages of outsourcing noted by Exabeam are as follows: “15% of alerts require organizational involvement, and organizational resources cannot be completely replaced,” “It’s not possible to train engineers who can handle alerts within the organization” and “Threat signs are not proactively investigated and handed over to the appropriate party.” He concluded his presentation by saying, “We have received many similar inquiries at Exabeam, and we would like to discuss the outsourcing of security operations with everyone participating today.”
Presentation: ‘Key Points for Advanced Security Monitoring’
In the final presentation of the day, Mr. Sugimoto of KPMG Consulting introduced the “Key Points of Advanced Security Monitoring.” He observed that a recent shift in cyber security measures has been occurring, from many companies that used to implement a defined security measure model to using AI and big data for advanced detection and countermeasures.
Especially in the U.S., the trend is shifting toward advanced monitoring using AI and machine learning. The AI/machine learning approach is gaining popularity recently by promoting advanced monitoring while reducing labor and others costs and also as a solution for security personnel shortage.
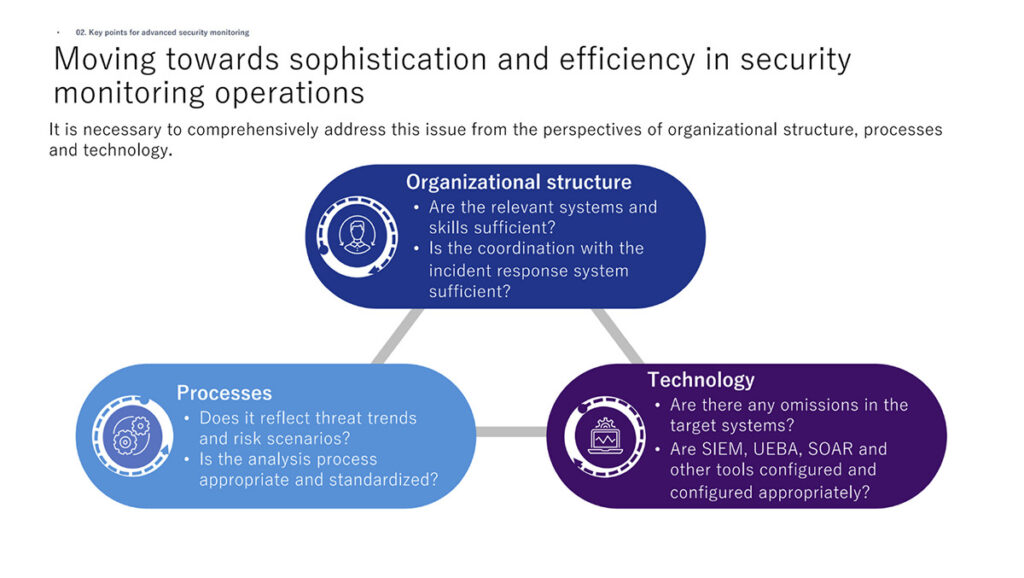
Mr. Sugimoto went on to emphasize, “Many tools and technologies have been developed that improve the sophistication and efficiency of security monitoring operations, but we must still take a comprehensive approach from the perspectives of organizational structure, processes, and technology.”
Mr. Sugimoto observed that “We need to to create an integrated environment for operations, by training staff to deal with the shortage of security personnel, and establishing a system for responding to incidents after they are detected and build an analysis process for alerts.”
Discussion: ‘Security monitoring concerns and future outlook of the participating companies’
In the final session, the participants discussed the future approaches in advanced security monitoring and the prospects for internalizing and outsourcing SOC organizations based on the previous presentations. The following answers were given regarding the approaches and the future outlook of each company.
A participant from a major comprehensive chemicals manufacturer shared, “We implemented Exabeam in October 2021 and it is currently running in parallel with our existing SIEM solution. The existing SIEM is used for static monitoring of events such as company-wide file server account threat alerts. When we think about the future, monitoring the internal network alone will not suffice. Assuming that the monitoring will be extended to the Internet side and multiple alerts will occur, there will be a limit to how much we can handle by setting rules manually ourselves. We will need to automate some of the responses and manually take care of the remaining issues.
Another major electronics manufacturer mentioned, “We are switching to in-house security monitoring to increase response speed. Regarding insider threats, we are trying to find out how to detect people taking data outside the company by improving the algorithm. There are still a lot of false positives, but the good thing about in-house monitoring is that we can proceed with this kind of work on our own. The SIEM products available globally are getting much better, and we think it makes sense to make good use of SIEM to improve in-house monitoring.
According to a major comprehensive construction company “Our SOC system will continue to be a mix of internal and external systems. We will do what can only be done in-house and ask outside companies to do the rest. As the response time is greater when we ask for outside help, we have a system in place to handle requests from outside the company internally as a hedge against risk. We believe that it is better to have a hybrid system where the right people are in the right places, using both internal and external resources.
Many participating companies expressed their expectations for automation and in-house production to cope with the expansion of monitoring targets and increase the speed and flexibility of incident response.
Closing: Summary
Mr. Shimizu concluded the seminar by thanking the participants. “We would like to continue to hear from end-users about global use cases of Exabeam and cases of insider threats. Regarding security monitoring, I would like to continue to share information and discuss relevant issues with all of you,” he said.
Security monitoring issues and approaches faced by each company were revealed during the discussions, and Exabeam’s solutions were shown to be a possible answer to many of the issues raised. As a next-generation SIEM platform that utilizes AI and machine learning, Exabeam is certain to play an increasingly important role in the future.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












