Insider threats are a growing concern for all organizations—one that is increasingly difficult to manage using conventional security technologies. Unlike other types of security threats, insider threats are complicated by the fact that only a few are caused by intentional malicious insiders.
“The greatest threat to the security of US companies is no longer the hacker attacking from beyond network walls. Now, it is the insiders already within those walls, and equipped with an all-access pass.”
The Future of Insider Threats, by Robert N. Rose; Forbes.com
Beyond full- and part-time employees, insiders include contractors, vendors, customers, interns, and others. Frequently they’re authorized to access some part of your network, but too often their accesses and permissions, (not to mention activities), aren’t being effectively managed by your security team.
Compounding this situation, the number of unmanaged mobile and personal devices connecting to a typical corporate network is growing. When you consider all these risks, you can understand why insider threats require a comprehensive cybersecurity strategy.
Consider the statistics:
- In a 2018 survey by the Ponemon Institute, 59 percent admitted that their organization had experienced a data breach caused by one of their third parties such as a vendor. Forty-two percent said that an insider breach happened within the past 12 months.
- A 2018 Verizon study showed that within the healthcare industry, insiders were responsible for 58 percent of data breaches. They were attributed to a combination of accidental and malicious insider actions.
- Based on more than 700 cases in the CERT insider threat database, 59 percent of departing employees will take sensitive information with them.
When you miss an insider threat, the impact can be severe. A 2018 Ponemon Institute study revealed that the average annual cost of insider-related incidents is USD $8.76 million. And it takes an average of 52 days to resolve each insider threat incident.
In this article:
- The risks of using traditional insider threat security strategies
- Security teams are faced with overwhelming amounts of log data
- Traditional insider threat programs
- The smart approach to managing insider threats
- Understanding user behaviors is key
The risks of using traditional insider threat security strategies
Traditional security measures like using a legacy SIEM typically involve analysts manually examining log files from multiple sources and then trying to make sense of all their data. This usually requires a lot of copying and pasting across multiple files to compile an investigation diary—and you’re unlikely to easily find and mitigate the legitimate security incidents.
Many barriers can interfere with your threat identification and mitigation, including:
- Obtaining the required data to determine if an incident has occurred – You have nearly a zero chance of success without access to the right data, namely network events, endpoint events, and identity-based activity. Do you have full access to all of the data you need to effectively identify insider threats?
- Making sense of the vast amounts of data that reside in different systems and physical locations – Many systems and services are connected to your network and are potential targets. Are you able to understand each of their logs, events, and alerts?
- Segregating insiders and their potential and actual threats from other threats – Can you identify an insider using the tools at your disposal? Are you able to identify that person’s department, location, peer groups, supervisor, and other important information?
- Accurately identifying the “crown jewels” – Which assets will an attacker likely pursue? These can include anything from lists of employees and credentials (login/pw combinations) to lists of customers, internal financials, proprietary code or patents, or even information about the network and types of tools and frameworks used. Are these assets safe, or have they already been unknowingly compromised? Has an insider already created their own logins and credentials, or even exfiltrated data?
- Understanding clues without reliable context on good or bad behavior – What is normal behavior? Can you identify it by looking at log data? Are the policies enforceable – for instance, is it permissible for a key asset to be accessed from a VPN connection originating in China, as an example? Can the same credentials be logged in from two different ISPs?
- Dealing with a large attack surface – How many people and service accounts (including smart devices) have valid credentials on your network? Do any still have accounts or knowledge on how to access your assets after they leave the organization? When a service, website, or device is decommissioned, is it removed from all internal management systems, including root credentials?
- Training and awareness – Do your analysts have the right experience so they can be effective with your current insider threat identification and mitigation solution? Is there clarity on how to investigate when anomalies and security events are escalated?
Security teams are faced with overwhelming amounts of log data
Security teams are tasked with monitoring log data from a multitude of sources, including but not limited to:
- Local network connections such as remote offices, users’ homes, WANs, and travelers on the road using a VPN or VDI
- Cloud services and applications managed by entities or teams outside of security’s direct control
- Document management systems containing your company’s sensitive information
- Distributed printers involved in breaches either electronically, or through the printing of information that is carried out the door.
- Mobile phones, tablets, and other BYOD (managed or unmanaged) connecting to wireless access points and company resources
- Employees receiving and responding to personal emails, visiting social networks, and doing other personal tasks on your network
- Email events or alert from phishing or messages with suspicious URLs
Traditional insider threat programs
Traditional security approaches like correlation rules can’t automate threat detection; They only detect known threats for which the rules have been written. The risks you really need to detect are often of the unknown variety.
Traditional security solutions leave security analysts working in reactive mode, handling events and alerts after they’ve become incidents or even breaches. A lot of sensitive data can leave your organization over the average 52 days it takes to resolve a malicious insider incident.
The smart approach to managing insider threats
Expecting analysts to painstakingly monitor insider threats isn’t a reasonable solution. The smart approach will address the challenges in legacy SIEM solutions:
- Collecting all log data – With a smart SIEM, you can ingest all the log data you need. Ideally, all the critical data is available to your analysts without having to arbitrarily cherry-picking through event logs to see if they have the right information.
- Automated and continuous behavior modeling – The best way to identify anomalous behavior is to first understand what constitutes normal behavior. A user and entity behavior analytics (UEBA) solution automatically creates normal behavior baselines, then continuously models behavior going forward.
- Smart session timeline creation – To surface anomalous behavior, you need to answer the who, what, when, where, and why. A prebuilt, context-rich timeline of every user session and corresponding security event from your stack can give you this insight.
- Threat hunting capabilities – To easily detect anomalous behavior, you’ll want a well-designed, all-inclusive user interface where even entry-level analysts can predictably identify evolving insider threats. Ideally, you should be able to search session timelines to reveal clues to threats. This includes incorporating threat intelligence data automatically to add context to event logs and indicators of compromise.
- Automated response – A complete solution assigns risk scores to behaviors, triggering responses based on risk totals. Depending on the integration within your IT environment, responses can range from simply flagging a user or machine, to running an automated playbook, to mitigating an event without human intervention.
Understanding user behavior is key
User behaviors — especially with service accounts — often provide critical warnings so that you can mitigate and prevent security threats. To manage insider threats based on behaviors, you need to establish a normal behavior baseline for each user. Figure 1 shows a potential insider threat that was identified by baselining their normal behavior against their anomalous activities, resulting in an elevated risk score.
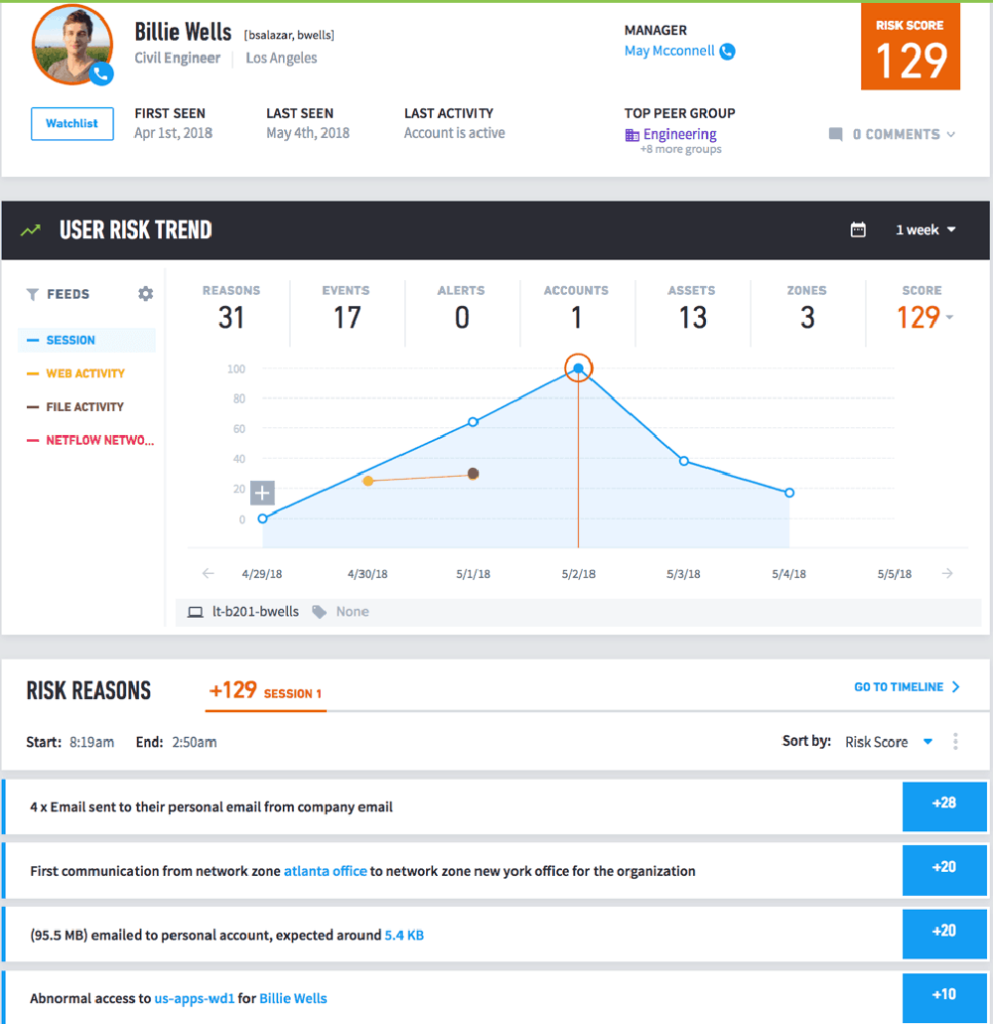
Looking at the timeline, you can review if there are other security events or alerts which are indicative of insider threats. Typically, if you’ve found one indicator, there are other related events that lead to the threat—not just one event—allowing analysts to track down all the security incidents in one timeline.
Learn more about behavior-based approach to manage insider threats
Have a look at these resources:
- How to Find Malicious Insiders: Tackling Insider Threats via Behavioral Indicators
- Sharpening First-Time Access Alerts for Insider Threat Detection
- Fighting Malicious Insider Threats with Data Science
- Exposing Malicious Insider Threats: The Advantages of Using a Behavior-based Approach
- User Behavior Analytics (UBA/UEBA): The Key to Uncovering Insider and Unknown Security Threats
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













