Every organization can expect to deal with a security event that will develop into a security incident. The ramifications of a security incident range from long arduous nights and weekends to public disclosure that impacts the firm’s brand and reputation. As a previous incident handler, I held the responsibility of managing multiple workstreams to reduce the risk exposure presented by an incident.
I also learned that as an incident handler, there are various aspects of the incident to consider. However, for simplicity, incidents are divided into technical and business impact tracks. From the technical perspective, the focus is to ensure there is a deep understanding of the attack, the scope of the environment, and validate the availability of logs to perform a comprehensive analysis. Most importantly, the technical analysis needs to result in an executive presentation to brief upper management on the incident timeline. The business impact track involves considerations such as legal requirements, public and internal communications, business operations, and short- and long-term remediations.
On average, the mean-time-to-identify a breach is 197 days or approximately 28 weeks, according to IBM Security. A security operations center (SOC) prioritizes the logs it ingests due to financial constraints of hardware and licensing, therefore, I experienced various instances where the SIEM only contained logs for 90 days. During a large incident, timelines are constantly pushed back as new discoveries such as indicators of compromises (IOCs) and tactics, techniques and procedures (TTPs) are made throughout the analysis. For an incident handler, the incident requires the assistance of other teams to obtain local logs of systems that are possibly in-scope. The log analysis process itself is a manual and daunting task that needs to be accurate and developed at a fast pace.
What do executives care about?
Incident handlers need to prioritize the information that is communicated to executives. In my experience, executives are most concerned about the following:
- Attack vector and TTPs
Every large incident consists of unique attack vectors and a combination of TTPs specific to the organization’s environment. During an executive briefing, an incident handler needs to communicate the exploited attack vector and provide examples of TTPs the adversary used to infiltrate the organization. In addition, the incident handler needs to be prepared to answer questions regarding the possibility of the adversary residing in other areas within the environment. Another important point is to identify patient zero as a starting point to begin dissecting the initial attack vector and track the TTPs used throughout the incident. - Short-term remediations
Once the executives understand the attack, incident handlers need to provide a list of short-term remediation actions that will impact the organization at a larger scale. For example, if the adversary moved across the environment using remote desktop protocol (RDP), the incident handler needs to work with security engineering and the IT department to understand how to harden access. Executives find this information valuable as they can assist in accelerating the changes required to make the environment more secure. - Incident timeline start date
The incident timeline is critical to an investigation as it provides a specific time frame for an incident handler to scope the incident. Executives need to know the length of time of the intrusion along with the ability to retrospectively search for activities performed by the adversary. Incident handlers need to ensure the incident start date is precise and accurate. - Total compromised users and systems
Large incidents have the ability to expand at a rapid pace. As an incident grows, it is imperative for incident handlers to track metrics such as the total compromised users and systems. As the number of compromised users are mapped to the incident timeline, incident handlers can begin to identify motives and commonalities across the compromised users. For example, patient zero is a system administrator. However, the adversary moved laterally to compromise users in the innovation team, so the incident handler can determine the adversary targeted the system administrator for initial access. Depending on the level of logging performed by the organization, incident handlers might need to focus on manual analysis to determine each compromised user’s system access.
In addition to compromised users, incident handlers need a thorough understanding of the compromised systems the adversary targeted. The adversary may have targeted those systems because of the data it stores or processes. The analysis of compromised systems can lead to a damage assessment and/or a breach notification. For example, if the innovation team had access to a system that stored production customer data, the legal team may decide to analyze its contractual obligations to notify the customer and provide the customer with identity theft monitoring. Executives need to know about the total number of compromised users and systems to help gauge if there are any organization-wide response efforts that need to take place. - Public relations and communications
Public disclosure of a high severity incident can cause significant damage to a firm’s brand. The communications team needs to have a prepared media holding statement in case the incident becomes public. Social media should be monitored to proactively identify any public comments related to the incident. For example, if the incident disrupts a customer-facing service, the firm can expect customers to post the issue on social media platforms. Executives want to ensure the firm is prepared to make statements to the media and proactively reach out to dissatisfied customers. - Legal obligations
Throughout the incident, the legal team is available to provide counsel. Executives need to understand the legal implications of an incident such as obligations for contractual and regulatory reporting or data breach disclosure which may consist of employee, customer, or vendor data. If the legal team concludes that the firm is obligated to disclose the breach, legal can have a conversation on next steps such as notification logistics, setting up a team to answer questions from impacted parties, and provide identity theft monitoring, if required. - Business operations
Data breaches can impact core business functions that can cause significant and lasting issues. For example, if an adversary compromises the firm’s payroll system two days prior to the next payroll cycle, can the firm continue business operations without delaying their employees pay? Executives value continuing business operations while limiting impact. The firm can experience repercussions if as in our previous scenario, employees are not paid and they publicly post or contact the media which will lead to a public relations issue. Part of the role of incident handlers is to interweave the technical and business side of an incident together to provide executives with a comprehensive analysis.
Presenting the incident to executives
Two critical items can help in briefings to the executive team: data visualization and accurate data of the incident.
Helping your team visualize the incident
During critical incidents, I had to update executives on a daily basis. When communicating the details of the incident, I found it helpful to create visualizations of how the situation transpired. These visualizations gave the executives a quick summary of the complexity of the issue. However, I often spent hours developing a PowerPoint presentation that could effectively communicate the technical details into non-technical terms. I found developing a timeline in PowerPoint is time-consuming and had less time to perform technical analysis. As my team made new discoveries, I would update these PowerPoint presentations. Again, the iterations of updating these presentations took away time from continuing the investigation.
Pinpointing and presenting relevant data to the C-team
In a presentation to the executives, information such as patient zero, the timing and length of the incident are critical. I would work with my colleagues to hunt for the information and manually stitch the event together. It was difficult to find the data because legacy SIEMs are excellent at displaying the data if an analyst writes the right queries. If the analyst is not familiar with the environment or the data set, the timeline may be inaccurate.
Another challenge analysts face is deciphering which logs are relevant. As incidents require over 100 days of retrospective searching, the incident may expand to tens or hundreds of thousands of logs that require review.
Below is an example of a traditional SIEM – an analyst enters a query, continues to pivot, and expands based on new findings. In the screenshot below, we can see that our scope is only a few hours, however, we have over 3,000 events that an analyst needs to analyze. For environments that use DHCP for workstations, analysts are tasked with tracking an IP address back to a workstation in a specific point in time – this exercise alone is daunting and time-consuming.
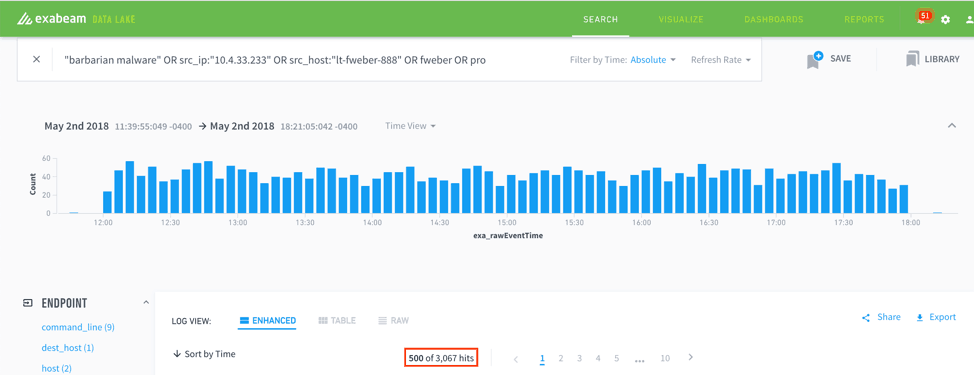
Figure 1: This example shows how within a few hours 3,000 events have been generated by a single incident. Analysts often have to review a few months of log data for a security incident.
Automating visualizations and timelines for executive briefings
Incident handlers and analysts now have a better way to analyze and present the data using Exabeam Advanced Analytics. The Advanced Analytics engine is able to stitch together user sessions and identify anomalous activity based on known TTPs or deviations of behavior using our machine learning engine. Analysts are able to view a user’s session, quickly obtain context on the user, and identify anomalous activity during that user’s session. Most importantly, they are not required to learn a new query language. An intuitive point-and-click solution helps analysts focus on their core function which is to analyze the data to make a decision.
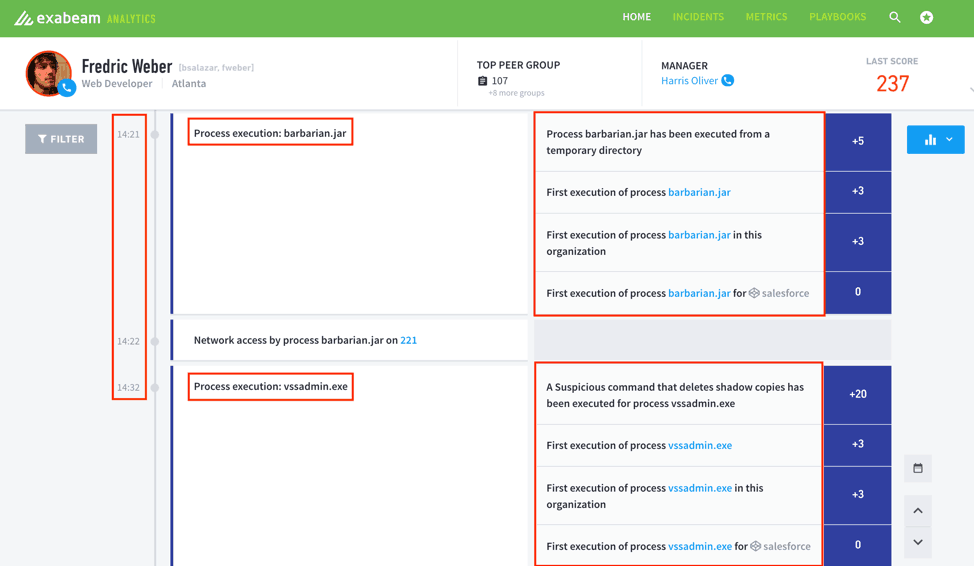
Figure 2: Exabeam Analytics Smart Timelines presents a history of user sessions and identifies anomalous activity based on known TTPs or deviations of behavior through machine learning.
Conclusion
Incident handlers are responsible for several workstreams during an incident and for coordinating the action and response. As a result, during an incident, it is important to include other teams such as legal and public relations to handle the incident appropriately. Finally, the visualization of a timeline with the investigation findings is invaluable for executives and other teams involved during an incident. Visualization provides an alternative, summarized method to follow and understand the incident helping build a quicker path to resolution.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













