In part one of our internet of things (IoT) blog series, we provided background on the tremendous growth of IoT and their innovative use cases—from alarm systems, to power grid monitoring, to devices that are combating honeybee colony collapse disorder.
We also looked at the 600% increase in IoT attacks that occurred between 2016 – 2017. And we examined that while many organizations have deployed IoT devices, typically they aren’t properly monitored or controlled with the same diligence and policies as other network systems.
Are IoT devices like security cameras, printers, and thermostats creating cybersecurity risks?
Your security operations center (SOC) most likely can tell when a user makes a VPN connection and authenticates with a database server. But do they know when someone makes a connection to a non-computer asset? Can you tell who has accessed your lighting controls, your security cameras, or your fire control system? Do you even know about all of the devices connected to your network? What about network-connected printers?
If your organization is like most, many of these IoT systems aren’t even on your radar, often because there isn’t the necessary monitoring solution for such internet connected devices.
“Research published by academics has resurfaced several serious vulnerabilities in popular internet-connected printers, which if exploited could allow an attacker to remotely steal sensitive documents from print jobs.
“Worse, the researchers say, is that an attacker could use one of the age-old bugs to read the printer’s network credentials, such as for email sharing, or other corporate accounts if the printer is used for other functions, like scanning and faxing.”
– “Flaws in popular printers can let hackers easily steal printed documents,” by Zack Whittaker for Zero Day
What’s at stake?
We all know that letting a hacker take over a critical asset in a hospital, power grid, or military facility could have disastrous results. But what’s the big deal if a hacker takes over a security camera or thermostat? What’s the risk if someone is tinkering with your environmental controls or watching your parking lot? And how does a hacker even access one of these devices?
Unpatched IoT Devices
Many IoT devices are unpatched, connecting to corporate networks through standard internet service providers. A security-conscious organization would likely cordon off these devices through isolated routers, making sure that there are no pathways from the devices to protected network assets.
But hackers can use readily available tools to easily locate publicly connected devices with documented security vulnerabilities. Once they find a target, they can attempt a factory reset and get root access to the device through published lists from a Common Vulnerabilities and Exposure (CVE) site. If successful, they can now control the device, such as watching a video feed.
If a compromised camera is in an organization’s lobby, the attacker can view employees and visitors coming and going, and potentially see what’s being typed on a receptionist’s computer. Moreover, they can initiate a DDoS attack on many device types, rendering them unavailable or unresponsive for an extended period of time.
Lateral moves
Determined attackers can learn, for example, the IP address and model number of the router to which the compromised IoT device is attached. Once that is known, they can determine if the router has vulnerabilities.
For example, some routers have well known code-execution vulnerabilities, and the targeted organization might have failed to apply patches in a timely manner. An attacker could use a tool to crack the router’s hashed data to obtain the router’s credentials, then install and execute code that enables them to scour the network for valuable data. If the original attack vector was a lobby camera, the attacker might already know credentials of at least one network user (possibly obtained by viewing a computer screen or from analyzing user keystrokes).
Given this IoT attack landscape, remember that your organization is exposed to the same compliance regulations such as GDPR (and penalties), regardless of whether a breach is caused by a network-connected device or a user.
Analyzing IoT device behavior
To know what’s happening with your IoT devices, you have to understand their baseline behavior. To do this, you need:
- Visibility into the communication patterns of your network devices. Most communication between machines and network zones is unknown today.
- An understanding of each connected device, including its trusted and normal operating behaviors. For example, has one or more of your devices experienced a password spray or brute force attack?
- Knowledge of asset ownership—who is responsible for a given device? Who originally connected it, and who was the last person to update its configuration? Typically, we find a lack of responsibility for system level behaviors of IoT devices.
- Correlation of IP addresses to device or user names. You need to be able to identify risky devices and the users who have interacted with them.
- An understanding of network activity in the absence of users. Data about firewalls, network packets, and net flow are required to get a complete picture of network behavior.
Users – Exabeam Advanced Analytics (AA) has solved these problems from the perspective of users. It analyzes each network user’s behavior patterns over consecutive sessions, scoring users based on how far they deviate from normal patterns. When a score exceeds a predetermined trigger point, AA notifies your SOC, so they can investigate potential breaches. In addition, your analysts can examine any user, behavior pattern, and time frame to investigate, for example, any unusual events that have occurred.
Devices – Adding to Advanced Analytics, Exabeam Entity Analytics provides the same set of features for your network connected devices (IoT). Entity Analytics monitors any connected devices and notifies you when its behavior patterns fall outside a normal range.
Following an IoT attack chain
Continually monitoring the behavior of each of your IoT entities, such a system can notify you when it detects abnormal behaviors (Fig. 1).
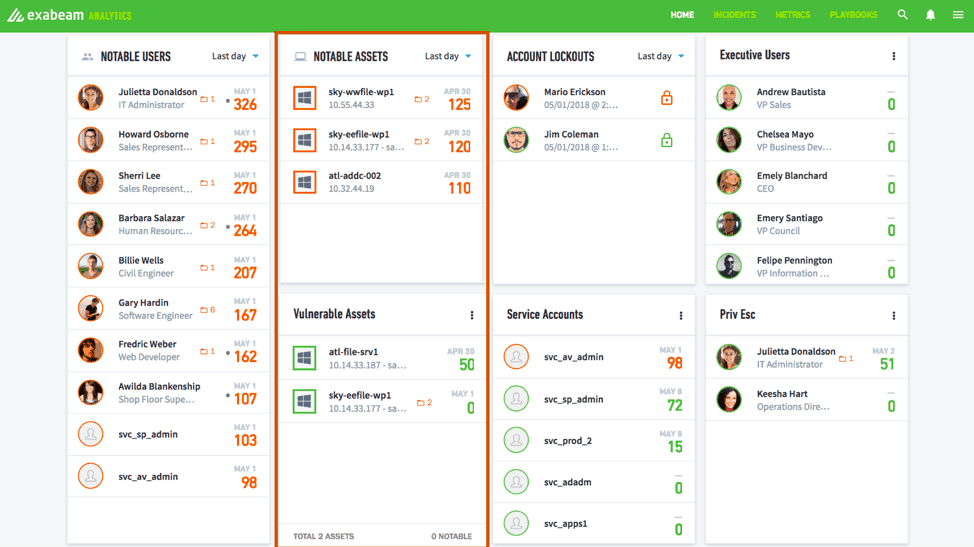
Figure 1 – Exabeam Advanced Analytics dashboard showing notable assets that have high-risk scores
Prebuilt incident timelines answer critical questions and provide you with all of the information you need for a rapid investigation:
- What happened, and in what order?
- Was it normal or abnormal for that particular asset?
- What happened before and after the security incident?
- Was there lateral movement to other users or devices?
In examining the timeline for a device (Fig. 2), you can easily see the progression of events that caused an escalated score.
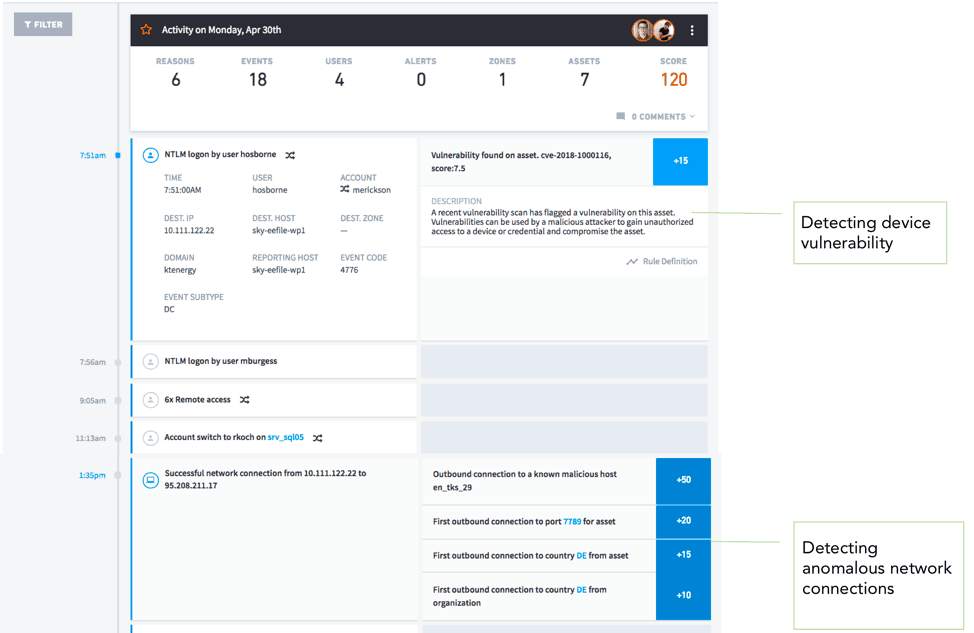
Figure 2 – Event timeline stitches together user and asset behavior. In this example, the risks are due to device vulnerability and anomalous network connections.
The left column shows the time stamp for each event. The right column highlights abnormal events and indicates the number of risk points each event adds to its risk score. User and entity behaviors are integrated into a “single pane of glass” view. This allows even junior-level analysts to instantly pivot from viewing an entity, to viewing the users associated with it and the impacts (Fig. 3).
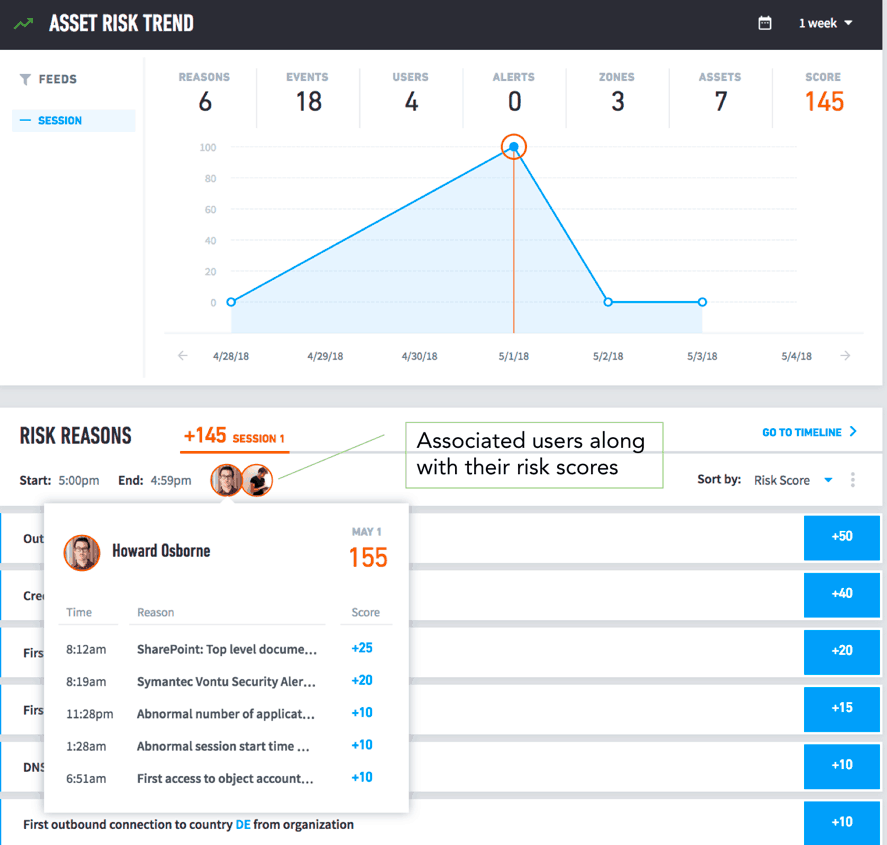
Figure 3 – The ability to pivot between devices and users helps investigators to pinpoint anomalous behavior quicker.
We’ve provided some examples of how IoT hardware interacts with users and other entities on your network. You’ve seen a few of the problems they can cause, as well as the kinds of information you’ll need to successfully track and manage the growing pool of IoT devices.
Remember, most complex threats involve both users and assets. Exabeam Entity Analytics enables you to easily pivot and follow the progression of a security incident—no matter where it reaches your network.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












