MITRE ATT&CK Explainers:
What is MITRE ATT&CK®: An Explainer
What is MITRE ATT&CK?
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations of cybersecurity threats. They’re displayed in matrices that are arranged by attack stages, from initial system access to data theft or machine control. There are matrices for common desktop platforms—Linux, macOS and Windows, technologies like cloud, containers, network, ICS, and mobile platforms.
This is part of an extensive series of guides about information security.
What are Tactics in the ATT&CK Framework?
ATT&CK stands for adversarial tactics, techniques, and common knowledge. The tactics are a modern way of looking at cyberattacks. Rather than looking at the results of an attack, aka an indicator of compromise (IoC), it identifies tactics that indicate an attack is in progress. Tactics are the “why” of an attack technique.
The Enterprise ATT&CK matrix (learn about all three matrices below) has 14 tactics:
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Command & Control
- Collection
- Exfiltration
- Impact
What are Techniques in the ATT&CK Framework?
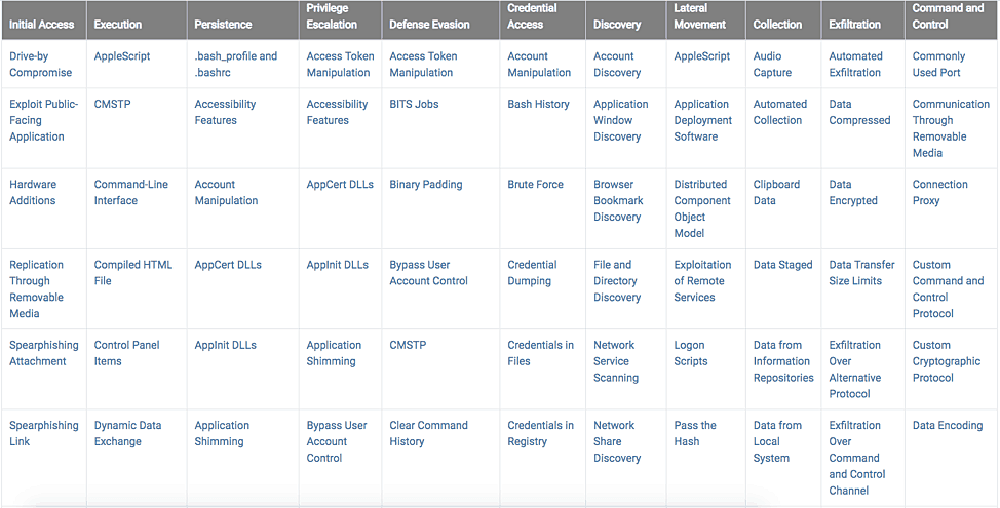
The second “T” in ATT&CK stands for techniques. Each tactic includes a set of techniques that have been seen used by malware and threat actors. Techniques represent the “how”—how attackers carry out a tactic in practice. For example, if the tactic is privilege escalation, the techniques will be various ways attackers carry out privilege escalation in real world attacks.
There are currently 185 techniques and 367 sub-techniques in the Enterprise ATT&CK matrix, and Mitre continuously adds more. Each technique has a four-digit code—for example, Abuse Elevation Control Mechanism is T1548.
Each technique contains specific information about how threat actors operate, such as the privileges required, the platforms on which the technology is commonly used, and how to detect commands or activities associated with the technique.
What is Common Knowledge in the ATT&CK Framework?
The “CK” at the end of ATT&CK stands for common knowledge. This is the documented use of tactics and techniques by adversaries. Essentially, common knowledge is the documentation of procedures. Those familiar with cybersecurity may be familiar with the term “tactics, techniques, and procedures,” or TTP. (The “CK” makes for a sexier acronym than “P”— always a must in government projects.)
Who is MITRE?
MITRE is a government-funded research organization based in Bedford, MA, and McLean, VA. The company was spun out of MIT in 1958 and has been involved in a range of commercial and top secret projects for a range of agencies. These included the development of the FAA air traffic control system and the AWACS airborne radar system. MITRE has a substantial cybersecurity practice funded by the National Institute of Standards and Technology (NIST).
(Interestingly, MITRE is not an acronym, though some thought it stood for Massachusetts Institute of Technology Research and Engineering. The name is the creation of James McCormack, an early board member, who wanted a name that meant nothing, but sounded evocative.)
What is the Goal of MITRE ATT&CK?
The goal of the Mitre security initiative is to create a comprehensive list of known adversary tactics and techniques used during a cyberattack. Open to government, education, and commercial organizations, it should be able to collect a wide, and hopefully exhaustive, range of attack stages and sequences. MITRE ATT&CK is intended to create a standard taxonomy to make communications between organizations more specific.
ATT&CK was created out of a need to systematically categorize adversary behavior as part of conducting structured adversary emulation exercises within MITRE’s Fort Meade Experiment research environment.
What are the ATT&CK Matrices?
There are three matrices in the ATT&CK framework:
- Enterprise ATT&CK – an adversary model that explains actions an attacker can take to operate inside a corporate network. It mainly focuses on post-compromise behavior. This matrix can help prioritize network defense, explaining the tactics, techniques, and procedures (TTPs) attackers use once inside the network.
- PRE-ATT&CK – this matrix focuses on activities performed before an attack, largely outside the organization’s view. It helps security teams understand how attacker perform reconnaissance and select their point of entry, and makes it possible to more effectively monitor and identify attacker activities outside the boundaries of the corporate network.
- Mobile ATT&CK – based on the NIST Mobile Threat Catalogue, this is a threat model describing tactics and techniques attackers can use to infiltrate mobile devices. These include “network-based effects”, attack methods which can be performed without direct access to the device.
How Do You Use the ATT&CK Matrix?
The MITRE ATT&CK Matrix visually arranges all known tactics and techniques into an easy to understand format. Attack tactics are shown across the top, and individual techniques are listed down each column.
In the Enterprise ATT&CK matrix, an attack sequence would involve at least one technique per tactic, and a completed attack sequence would be built by moving from left (Initial Access) to right (Command and Control). It is possible for multiple techniques to be used for one tactic. For example, an attacker might try both an attachment and a link in a spear phishing exploit.
It’s not necessary for an attacker to use all eleven tactics across the top of the matrix. Rather, the attacker will use the minimum number of tactics to achieve their objective, as it’s more efficient and provides less chance of discovery. In this attack (shown in Figure 3), the adversary performs Initial Access to the credentials of the CEO’s administrative assistant using a spear phishing link delivered in an email. Once they have the admin’s credentials, the attacker will look for a remote system in the Discovery stage.
Figure 3 shows an example attack with techniques from each tactical stage of the attack.
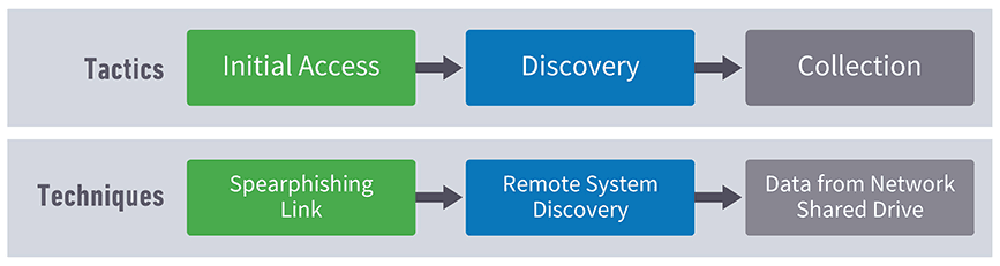
Let’s assume that they’re after sensitive data in a Dropbox folder to which the admin also has access, so there is no need to escalate privileges. Collection, which is the last stage, is performed by downloading files from Dropbox to the attacker’s machine.
Note that if using behavior analytics, a security analyst might detect the attack in process by identifying anomalous user behavior. For example, let’s say the admin clicked a link that no one in the company has ever clicked before, then the admin accessed a particular Dropbox folder at an unusual time. During the final stage of the attack, the attacker’s computer accessed the Dropbox folder for the first time. With behavioral analytics, these activities would be flagged as suspicious user behavior.
How Does MITRE ATT&CK Compare to Lockheed Martin’s Cyber Kill Chain?
Lockheed Martin’s Cyber Kill Chain®? and ATT&CK resemble each other in that both are models that define the steps an attacker uses to achieve their goal. Lockheed Martin’s Cyber Kill Chain identifies seven steps in an attack:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control
- Actions on objectives
ATT&CK has ten steps that make up an attack chain:
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection and xfiltration
- Command and control
In addition to more granularity in the attack chain tactics, ATT&CK delineates the techniques that can be used in each stage, whereas Lockheed Martin’s Cyber Kill Chain does not.
What Can Be Done with MITRE ATT&CK?
There are a number of ways an organization can use MITRE ATT&CK. Here are the primary use cases.
- Adversary Emulation – ATT&CK can be used to create adversary emulation scenarios to test and verify defenses against common adversary techniques.
- Red Teaming – ATT&CK can be used to create red team plans and organize operations to avoid certain defensive measures that may be in place within a network.
- Behavioral Analytics Development – ATT&CK can be used to construct and test behavioral analytics to detect adversarial behavior within an environment.
- Defensive Gap Assessment – ATT&CK can be used as a common behavior-focused adversary model to assess tools, monitoring, and mitigations of existing defenses within an organization’s enterprise.
- SOC Maturity Assessment – ATT&CK can be used as one measurement to determine how effective a SOC is at detecting, analyzing, and responding to intrusions.
- Cyber Threat Intelligence Enrichment – ATT&CK is useful for understanding and documenting adversary group profiles from a behavioral perspective that is agnostic of the tools the group may use.
MITRE ATT&CK Framework Tools and Resources
Here is a list of tools and resources you can use to take advantage of the ATT&CK Framework.
ATT&CK Navigator
This is a free tool you can use to map your security controls to ATT&CK techniques. Specifically, you can add detective controls, preventive controls, and even display layers of observed behavior. The Navigator can be used online for simple models and scenarios, or downloaded and set up internally as a more permanent solution.
Direct link: https://github.com/mitre-attack/attack-navigator
MITRE Cyber Analytics Repository (CAR)
This is an analytics knowledge base provided by MITRE. It provides a large dataset of hypotheses, information domains which specify the context of the analytics (for example, host, network), references to specific ATT&CK TTPs, and pseudocode showing how the analytic can be implemented.
Direct link: https://car.mitre.org/
Caldera
An open source network security framework designed to emulate attacks and automate security responses. It can be used by red teams as well as incident responders. Its automated actions are based on the MITRE ATT&CK Framework.
Direct link: https://github.com/mitre/caldera
Red Canary Atomic Red Team
This open source tool can simulate hostile behavior mapped to the MITRE ATT&CK Framework. It is a simple test library that security teams can run to test their security controls. These are focused tests, which have few dependencies, and are defined in a structured format that can be used by automation frameworks.
Direct link: https://github.com/redcanaryco/atomic-red-team
Red Team Automation
This is yet another open source automation tool that can simulate malicious behavior based on MITRE ATT&CK tactics and techniques. It includes a Python script which can simulate over 50 tactics, with a compiled binary application that performs activities such as injecting processes and simulating beacons.
Direct link: https://github.com/endgameinc/RTA
Exabeam’s Relationship with MITRE ATT&CK
Exabeam security researchers participate in MITRE ATT&CK discussions and events. They have also contributed several new techniques that are pending publishing and researchers have performed extensive research on how to perform machine learning-based anomaly detection to effectively apply MITRE ATT&CK into the security analyst’s detection arsenal.
Exabeam will be adopting MITRE ATT&CK in the Exabeam Security Management Platform and Exabeam Cloud Security Services starting in 2019.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Log Management
Authored by Exabeam
- What Is Log Management? Process & Tools
- 5 Best Log Analysis Tools You Should Know in 2023
- 7 Critical Log Management Best Practices
Security Operations Center
Authored by Exabeam
- SOC Analyst: Job Description, Skills, and Certifications
- What Is a Security Operations Center? Complete Guide
- 5 SecOps Functions and Best Practices for SecOps Success
Disaster Recovery
Authored by Cloudian






