Insider Threat Explainers:
What Is an Insider Threat? Understand the Problem and Discover 4 Defensive Strategies
What is an insider threat?
An insider threat is a malicious activity against an organization that comes from users with legitimate access to an organization’s network, applications or databases. These users can be current employees, former employees, or third parties like partners, contractors, or temporary workers with access to the organization’s physical or digital assets. They can even come in the form of compromised service accounts. While the term is most commonly used to describe illicit or malicious activity, it can also refer to users who unintentionally cause harm to the business.
Why do insiders go bad? The motivation for malicious insiders vary — most often, compromises and data exfiltrations are financially motivated. However, incidents can also result from espionage, retaliation or grudge towards the employee, or just carelessness in poor security hygiene, or an unlocked or stolen access. Insider threats are more common in some industries — such as healthcare, the financial sector and government institutions — but they can compromise the information security of any company.
Types of insider threats
Malicious Insider
An employee or contractor who knowingly looks to steal information or disrupt operations. This may be an opportunist looking for ways to steal information that they can sell or which can help them in their career, or a disgruntled employee looking for ways to hurt an organization, punish or embarrass their employer. An example of a malicious insider are the various Apple engineers who were charged with data theft for stealing driverless car secrets for a China-based company.
Negligent Insider
An employee who does not follow proper IT procedures. For example, someone who leaves their computer without logging out, or an administrator who did not change a default password or failed to apply a security patch. An example of a negligent insider is the data analyst who, without authorization, took home a hard drive with personal data from 26.5 million U.S. military veterans, that was stolen in a home burglary.
Compromised Insider
A common example is an employee whose computer has been infected with malware. This typically happens via phishing scams or by clicking on links that cause malware downloads. Compromised insider machines can be used as a “home base” for cybercriminals, from which they can scan file shares, escalate privileges, infect other systems, and more. As is the case of the recent Twitter breach where attackers used a phone spear phishing attack to gain access to employee credentials and their internal network. The attackers managed to gain information about Twitter’s processes and target employees with access to account support tools to hack high-profile accounts and spread a cryptocurrency scam that earned $120,000.
Insider threat statistics: How big is the problem?
Insider threats are a growing problem, as evidenced by a recent Ponemon study “2020 Cost of Insider Threats: Global Report”:
- 60% of organizations had more than 30 insider-related incidents per year
- 62% of the insider-related incidents were attributed to negligence
- 23% of the insider-related incidents were attributed to criminal insiders
- 14% of the insider-related incidents were attributed to user credential theft
- Number of insider-related incidents increased by 47% in two years
- Companies spend an average of $755,760 on each insider-related incident
Insider Threats are difficult to detect because the threat actor has legitimate access to the organization’s systems and data. That is because an employee needs access to the resources like email, cloud apps or network resources to successfully do their job. Depending on the role, some employees will also need access to sensitive information like financials, patents, and customer information.
Because the threat actor has legitimate credentials and access to the organization’s systems and data, many security products would tag the behavior as normal and not trigger any alerts. Insider Threats become harder to detect as they become more complicated. For example, a threat actor could perform lateral movement to hide their tracks and access high value targets. Or, an insider could leverage a flaw in the system to escalate privileges, as described below.
How to find insider threats
Organizations can spot or predict insider threats by observing user behavior in the workplace and online. Being proactive may allow organizations to catch potentially malicious insiders before they exfiltrate proprietary information or disrupt operations.
What behaviors can your organization use to identify insider threats?
| Employee/Contractor Behavioral Trait | Organizational Event |
|---|---|
| Interest outside scope of their duties | Layoff |
| Working unusual hours without authorization | Annual merit cycle – individuals not promoted |
| Excessive negative commentary about organization | Annual merit cycle – individuals not given raises |
| Drug or alcohol abuse | Potential performance improvement plans, or workplace harassment complaints, and more |
| Financial difficulties | |
| Gambling debt | |
| Change in mental state | Potential performance improvement plans, or workplace harassment complaints, and more |
What suspicious security events can indicate a possible insider threat?
| Behavior | Malicious Insider | Compromised Insider |
|---|---|---|
| Badging into work at unusual times | X | |
| Logging in at unusual times | X | X |
| Logging in from unusual location | X | |
| Accessing systems/applications for the first time | X | X |
| Copying large amounts of information | X | X |
Examples of Insider Threats
Yahoo
In May 2022, Yahoo was hit by an insider threat attack. Qian Sang, a research scientist at the company, received a job offer from a competitor called The Trade Desk. Minutes later, Sang downloaded about 570,000 pages of Yahoo’s intellectual property to his personal devices, including information about Yahoo’s AdLearn product.
It took Yahoo several weeks to realize that Sang had stolen company data, including a competitive analysis of The Trade Desk. Yahoo sent Sang a cease-and-desist letter and brought three charges against him, including intellectual property data theft, claiming that Sang’s actions divested Yahoo’s exclusive control of its trade secrets.
Microsoft
In 2022, Microsoft experienced a data leak due to employee negligence. Cyber security firm spiderSilk discovered the leak – several Microsoft employees exposed their login credentials to the company’s GitHub infrastructure. This information could allow access to Azure servers and possibly other internal Microsoft systems.
Microsoft refused to divulge which systems these credentials protected. An internal investigation determined no one attempted to access the sensitive data, and the company took action to prevent this from occurring again. However, if this mistake exposed EU customer information, Microsoft could have faced a GDPR fine of as much as €20 million.
Proofpoint
What happened to Proofpoint proves that no one is immune to cyberattacks, including cybersecurity firms. In July 2021, Samuel Boone, an ex-employee, stole Proofpoint’s confidential sales enablement data right before starting working at Abnormal Security, a competitor.
Unfortunately, Proofpoint’s data loss prevention (DLP) solution could not prevent the employee from downloading high-value documents to a USB drive. It took Proofpoint several months to discover that Boone had taken these files. By that time, Boone could have achieved significant headway in sales at Abnormal Security. Proofpoint sued Boone in federal court for unlawfully sharing battlecards that could give him and his new employer an unfair advantage.
In July 2020, hackers compromised several high-profile Twitter accounts by launching a phone-based spearphishing campaign targeting Twitter employees. The campaign lured them in through a Bitcoin scam.
The attackers started by looking for information about internal processes and systems. Once they found the right employees to target, the attackers accessed account support tools that enabled them to break into 130 Twitter accounts.
This scam had a relatively minor financial impact on Twitter, and the victims received their money back. However, this incident exposed Twitter’s significant role in the information market and the company’s vulnerability to attacks.
Four ways to prepare against insider threats
There are many things an organization can do to combat insider threats. Here are the four main areas to focus on.
1. Train your employees
Conduct regular anti-phishing training. The most effective technique is for the organization to send phishing emails to its users and focus training on those users who do not recognize the email as a phishing attempt. This will help reduce the number of employees and contractors who may become compromised insiders.
Organizations should also train employees to spot risky behavior among their peers and report it to HR or IT security. An anonymous tip about a disgruntled employee may head off a malicious insider threat.
2. Coordinate IT security and HR
There is no shortage of stories about IT security teams that were blindsided by layoffs. Coordination between the CISO and the head of HR can help prepare IT security. Simply putting affected employees on a watchlist and monitoring their behavior can thwart many threats. Likewise, HR may advise IT security about certain employees that were passed over for a promotion or not given a raise. Tuning data loss prevention (DLP) tools with active thought and input from HR may also give an early warning sign of both self-harm and disgruntlement in terms of the establishment.
3. Build a threat hunting team
Many companies have dedicated threat hunting teams. Rather than reacting to incidents after they are discovered, threat hunting takes a proactive approach. Dedicated individuals on the IT security team look for telltale signs, such as those listed above, to heed off theft or disruption before it occurs.
4. Employ user behavioral analytics
User Behavior Analytics (UBA), also known as User and Entity Behavior Analytics (UEBA), is the tracking, collecting, and analyzing of user and machine data to detect threats within an organization. Using various analytical techniques, UEBA delineates anomalous from normal behaviors. This is typically done by collecting data over a period of time to understand what normal user behavior looks like, then flagging behavior that does not fit that pattern. UEBA can often spot unusual online behaviors – credential abuse, unusual access patterns, large data uploads – that are telltale signs of insider threats. More importantly, UEBA can often spot these unusual behaviors among compromised insiders long before criminals have gained access to critical systems.
Understanding the insider threat kill chain
If you want to understand insider threats in more detail, in this section we explain how insider threats grow and evolve – attacker motivations, methods of compromise, and how insider threats use privilege escalation to do more damage.
Insider threat motivations
More often than not, the ultimate goal of an insider threat is financial gain. Whether this is a malicious insider who has accepted cash for trade secrets, a negligent user who sends a wire-transfer to a fraudulent bank account after receiving a spoofed email from an “executive,” or a compromised insider whose credentials are stolen and used by attackers to exfiltrate and sell personally identifiable information (PII) of their patients. But there are many motivators for insider threats: sabotage, fraud, espionage, reputation damage or professional gain. Insider threats are not limited to exfiltrating or stealing information, any action taken by an “insider” that could negatively impact an organization falls into the insider threat category.
| Insider Type | Motivations | Example | Risks |
|---|---|---|---|
| Malicious | Making money or avenging a slight | Terminated employee plants a logic bomb to execute malicious code | Theft of core company intellectual property. Disruption of operations. Damage to company reputation. |
| Negligent | Ignorance or carelessness | Careless employee posts corporate data in public cloud container | Theft of core company intellectual property. Disruption of operations. Damage to company reputation. |
| Compromised | Oblivious to the risk they pose | An attacker uses compromised credentials to exfiltrate corporate data | Access to sensitive company systems or assets. Theft of core company intellectual property. |
How are employees compromised
There are several means by which an employee can become a compromised insider:
- Phishing – a cybercrime in which a target individual is contacted via email or text message by someone posing as a legitimate institution in order to lure the individual into providing sensitive data, such as personally identifiable information (PII), banking and credit card details, and passwords. Some phishing schemes may also try to entice a target to click on a link that triggers a malware download.
- Malware infection – a cybercrime when a machine is infected with malicious software – malware – infiltrates your computer. The goal of the malware in the case of a compromised insider is to steal sensitive information or user credentials. A Malware infection can be initiated by clicking on a link, downloading a file, or plugging in an infected USB, among other ways.
- Credential theft – a cybercrime aimed at stealing the username and password – the credentials – of a targeted individual. Credential theft can be done in a variety of ways. Phishing and malware infection, mentioned above, are common. Some criminals may engage in social engineering, which is the use of deception to manipulate individuals into divulging their credentials. A bogus call from the IT helpdesk, where the user is asked by the attacker to confirm their username and password, is a common technique.
- Pass-the-hash – a more advanced form of credential theft where the hashed – encrypted or digested – authentication credential is intercepted from one computer and used to gain access to other computers on the network. A pass-the-hash attack is very similar in concept to a password theft attack, but it relies on stealing and reusing password hash values rather than the actual plain text password, especially during RDP sessions.
Insider threats and privilege escalation
Insiders can carry out their plans via abuse of access rights. The attacker may try what is known as privilege escalation, which is taking advantage of system or application flaws to gain access to resources they do not have permission to access.
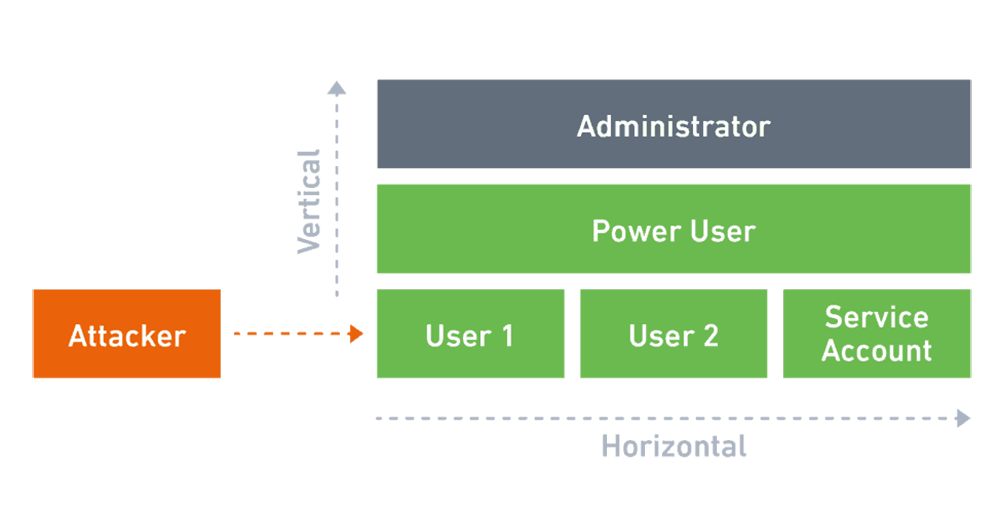
In some cases, abuse of access rights takes the form of someone with privileged access abusing their power. In a historic case from 2008, a system administrator working for the San Francisco city government blocked access to the city’s network and refused to surrender the admin passwords. The worker was disgruntled, and his job was in jeopardy, it was revealed.
These complex threats cannot be detected with traditional correlation rules because they are unknown threats. Instead, a security analyst would need to understand the user’s normal activity to be able to identify abnormal and potentially malicious activity.
Learn More About Insider Threat
Fighting Insider Threats with Data Science
One of the key benefits of a security information and event management (SIEM) platform with user and entity behavior analytics (UEBA) is the ability to solve security use cases without having to be a data scientist. The platform masks the underlying complexity of “doing data science” so that security operations center (SOC) staff can focus on keeping the enterprise safe from attacks. But if you’ve wondered what exactly is going on under the hood, this article provides a high-level glimpse of how Exabeam Security Management Platform (SMP) uses data science to address one of the most important and elusive use cases: insider threat detection.
Related content: Fighting Insider Threats with Data Science
Insider Threat Indicators: Finding the Enemy Within
The value of sensitive data and information to organizations is higher than ever. Many organizations allocate numerous resources to their cyber defensive measures and form a security operations center (SOC) to protect themselves against cyber attacks.
While cyber attacks are a threat to companies, they are not as common and in some cases, not as dangerous, as insider threats which are also much harder to detect.
In this article, we provide you with information about insider threats, including what is an insider threat, the indicators that can help you detect insider threats and the best tools to provide protection against such threats.
Related content: Insider Threat Indicators: Finding the Enemy Within
How to Find Malicious Insiders: Tackling Insider Threats Using Behavioral Indicators
Insider threats are insidious. Because they work within your network, have access to critical systems and assets, and use known devices—they can be very difficult to detect.
Crypto Mining: A Potential Insider Threat Hidden In Your Network
Exabeam’s newly released research looks inside the hidden world of cryptocurrency mining by malicious insiders. Imagine a trusted and privileged insider, a system administrator for example, who has wide access to your network mining cryptocurrency. The activity is undetected and in addition to draining valuable resources increases the attack surface on your network.
The report also provides recommendations on what your organization can do to protect your business from such shadow mining.
Related content: Crypto Mining: A Potential Insider Threat Hidden In Your Network
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Security Operations Center
Authored by Exabeam
- SOC Analyst: Job Description, Skills, and Certifications
- What Is a Security Operations Center? Complete Guide
- 5 SecOps Functions and Best Practices for SecOps Success
Mitre Att&ck
Authored by Exabeam
Malware Protection
Authored by Cynet






