See the Breadcrumbs, Follow the Trail
Exabeam doesn’t just collect the dots, we connect them. We piece anomalous activity into a behavioral narrative so you can prioritize the work you do best — deep investigation and determining intent — all with complete visibility across your ecosystem.
Automate the mundane, investigate the impossible
Exabeam offers automated threat detection and triage to manage the flood of merely informative alerts with Dynamic Alert Prioritization. By infusing third-party security alerts with context from user and entity behavior analytics (UEBA), Exabeam dynamically identifies, prioritizes, and escalates the alerts which require the most attention. When combined with automated Smart Timelines™, response playbooks free up valuable time so you can focus on the real threats that require your expertise.
Midmarket companies and enterprises seeking a modular, yet integrated security analytics platform with a focus on user behavior should consider Exabeam.
Joseph Blankenship
VP, Research Director, Forrester Research, Inc.
The Exabeam Resource Library
Learn everything about the Exabeam platform and beyond. Expand your knowledge on information security with our collection of whitepapers, podcasts, webinars and more.
REPORT
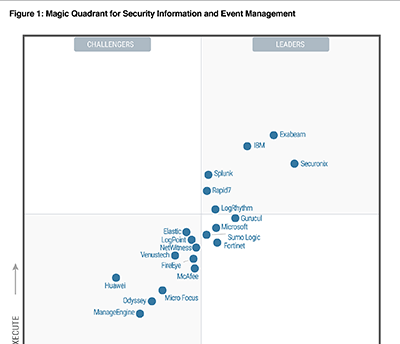
2022 Gartner Magic Quadrant for SIEM
Gartner named Exabeam a leader in the Magic Quadrant for SIEM for the third consecutive year.
Read the Report
WHITE PAPER
SIEM and XDR: A Comparison Guide
Learn how SIEM and open XDR are best suited for different situations. In this comparison guide, we dive into the strengths and differences of SIEM and XDR.
Read the White Paper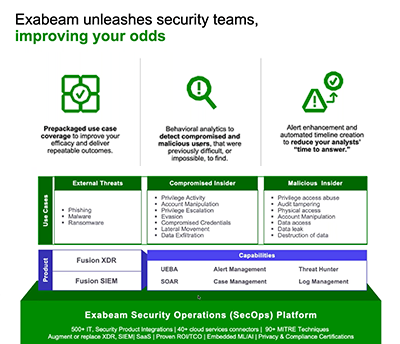
WEBINAR
Top Three Reasons to Replace Your Existing SIEM
SIEMs don’t have to be the bane of your existence, now is the time to take your SOC to the next level.
Watch the WebinarSee the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision







